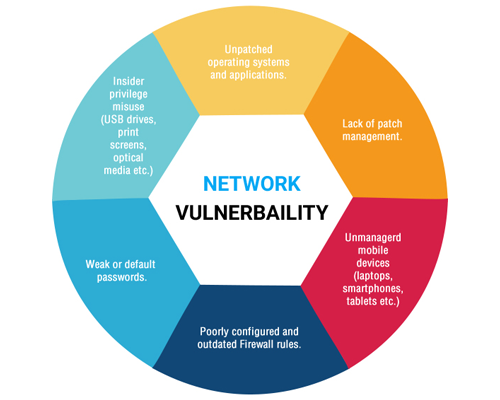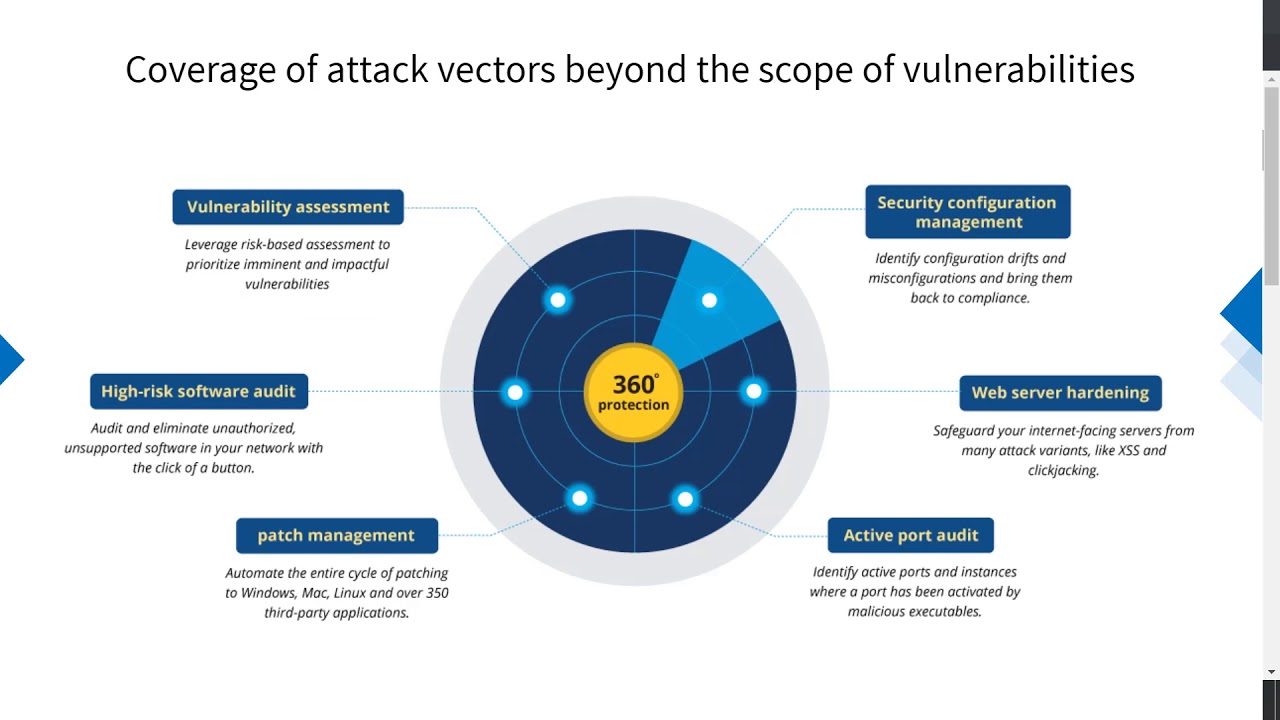
Introduction
An effective IT network security vulnerability management program is essential for businesses to protect their sensitive data and prevent unauthorized access to their networks. This article will discuss the five key components that are crucial for the success of such a program.
Definition of IT Network Security Vulnerability Management Program
An IT network security vulnerability management program is a strategic approach that identifies, evaluates, and prioritizes security vulnerabilities within an organization’s network infrastructure. It aims to minimize potential risks by implementing appropriate controls and regularly monitoring and updating the network’s security measures.
Importance of an effective program
Having an effective IT network security vulnerability management program is crucial for several reasons:
- Risk Assessment: Identifying and assessing vulnerabilities in the network helps an organization understand its security posture and prioritize security efforts accordingly.
- Prevent Data Breaches: A robust vulnerability management program can help prevent data breaches, which can cause significant financial losses and damage to an organization’s reputation.
- Compliance with regulations: Many industries have specific regulations and standards that require robust security measures to protect sensitive customer information. An effective program ensures compliance with these regulations.
- Minimize Downtime: Regular assessments and proactive remediation of vulnerabilities help to reduce network downtime caused by security incidents.
- Continual Improvement: An effective vulnerability management program should be dynamic and continually adapted to changing threat landscapes and emergent vulnerabilities, ensuring ongoing protection against evolving cybersecurity threats.
Implementing and maintaining an effective IT network security vulnerability management program requires a proactive approach, regular monitoring, and a commitment to security from all levels of the organization. By prioritizing these five key components, organizations can significantly strengthen their network security and protect their valuable assets from potential threats.
Program Planning
An effective IT network security vulnerability management program plays a crucial role in safeguarding sensitive data and preventing cyber threats. To ensure the efficiency and success of such a program, it is important to pay attention to these key components:
Identifying and assessing vulnerabilities
The first step in building a strong vulnerability management program is identifying and assessing vulnerabilities within your network infrastructure. This involves conducting regular scans and assessments to identify potential weaknesses and security gaps. By understanding your network’s vulnerabilities, you can prioritize the most critical ones and take appropriate actions to mitigate the risks.
Establishing risk management goals and objectives
To effectively address vulnerabilities, it is important to establish clear risk management goals and objectives. By defining what you aim to achieve in terms of risk reduction and security improvement, you can align your vulnerability management efforts with your organization’s overall strategic objectives. This ensures that your program is focused and results-oriented.
Developing a comprehensive plan for vulnerability management
A comprehensive plan is essential for effectively managing vulnerabilities. This plan should include procedures for vulnerability detection, prioritization, remediation, and ongoing monitoring. Outline the roles and responsibilities of team members in vulnerability management and identify the necessary tools and resources for the program. By having a well-defined plan in place, you can ensure consistency and efficiency in addressing vulnerabilities across your network.
Regular vulnerability scanning and patch management
Regular vulnerability scanning is critical for identifying new vulnerabilities and assessing the effectiveness of existing security controls. By conducting scans on a regular basis, you can stay proactive in addressing emerging threats and vulnerabilities. Additionally, patch management is essential for keeping your network infrastructure up to date with the latest security patches. This helps prevent exploitation of known vulnerabilities by cybercriminals.
Continuous monitoring and improvement
An effective vulnerability management program is not a one-time effort but an ongoing process. Continuous monitoring and improvement are necessary to ensure that your network remains secure against evolving threats. By regularly reviewing and updating your vulnerability management program, you can adapt to new vulnerabilities, technologies, and industry best practices.
A comprehensive IT network security vulnerability management program encompasses various key components. These components are vulnerability identification, risk management goals, comprehensive planning, regular scanning and patch management, and continuous monitoring. By focusing on these key areas, organizations can strengthen their network security and protect against potential cyber threats.
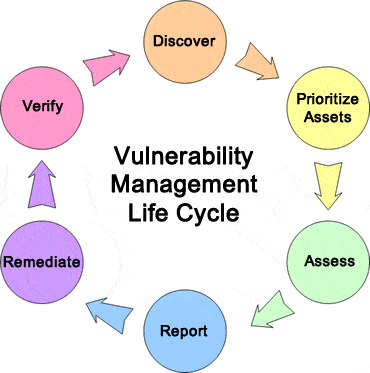
Vulnerability Scanning and Assessment
Conducting regular scans for vulnerabilities
To ensure the security of your IT network, it is crucial to conduct regular vulnerability scans. These scans identify weaknesses and potential entry points that attackers could exploit. By scanning your network on a regular basis, you can stay ahead of emerging threats and address vulnerabilities promptly.
Prioritizing and categorizing vulnerabilities based on severity
Not all vulnerabilities are created equal. Some pose a higher risk to your network than others. It is vital to prioritize and categorize vulnerabilities based on their severity levels. This allows you to focus your resources and attention on the most critical vulnerabilities that could have the biggest impact on your network security. By doing so, you can effectively allocate your time and effort to mitigate the most significant risks.
Performing detailed assessments to identify root causes and potential impacts
After identifying vulnerabilities, it is crucial to assess them thoroughly to understand their root causes and potential impacts on your network. This involves investigating the vulnerabilities further, assessing their potential impact on your network infrastructure, and determining the underlying factors that make them exploitable. By performing these assessments, you can gain valuable insights into the vulnerabilities and develop effective strategies to remediate them.
In summary, an effective IT network security vulnerability management program includes conducting regular vulnerability scans, prioritizing and categorizing vulnerabilities based on severity, and performing detailed assessments to identify root causes and potential impacts. By implementing these key components, you can proactively secure your IT network and reduce the risk of cyberattacks.

Remediation and Patch Management
Creating an action plan for addressing vulnerabilities
An effective IT network security vulnerability management program involves creating a comprehensive action plan for addressing vulnerabilities. This plan should include the following key components:
- Vulnerability Assessment: Conduct regular vulnerability assessments to identify potential weaknesses or flaws in your IT network. This will help you prioritize the vulnerabilities that need immediate attention.
- Risk Assessment: Once vulnerabilities are identified, conduct a risk assessment to determine the potential impact they could have on your network and business operations. This will help you prioritize remediation efforts based on the severity of each vulnerability.
- Prioritization: Prioritize and categorize vulnerabilities based on their severity and potential impact. This will help you allocate resources effectively and address the most critical vulnerabilities first.
- Remediation Plan: Develop a detailed remediation plan that outlines the steps and strategies for addressing each vulnerability. This plan should include timelines, responsibilities, and resources needed for remediation.
Implementing patches and updates in a timely manner
One of the key components of an effective IT network security vulnerability management program is the timely implementation of patches and updates. This involves the following actions:
- Monitoring: Continuously monitor for new vulnerabilities and patches released by software vendors and security organizations. Stay up-to-date with the latest security advisories and ensure you have access to reliable sources of vulnerability information.
- Testing: Before deploying patches and updates, perform thorough testing to ensure compatibility with your network infrastructure and applications. This will help prevent any unforeseen issues or disruptions.
- Patch Management: Implement a centralized patch management system to streamline the distribution and deployment of patches across your network. This will help ensure consistency and efficiency in the patching process.
- Timely Deployment: Deploy patches and updates in a timely manner, prioritizing critical patches with known vulnerabilities. Delaying patch deployment increases the risk of exploitation by threat actors.
By following these key components, you can establish an effective IT network security vulnerability management program that helps protect your organization’s critical assets and information from potential cyber threats.
Monitoring and Reporting
When it comes to IT network security, a proactive and comprehensive vulnerability management program is essential for protecting sensitive data and preventing cyber threats. Let’s take a closer look at five key components that are crucial for an effective vulnerability management program.
Establishing continuous monitoring processes
Continuous monitoring is a fundamental aspect of a successful vulnerability management program. It involves regularly scanning and assessing the IT network for potential vulnerabilities and weaknesses. By implementing continuous monitoring processes, organizations can identify and address security issues in real-time, reducing the risk of a breach.
Leveraging automated tools for real-time vulnerability tracking
Manual vulnerability tracking can be time-consuming and prone to human error. That’s why it’s important to leverage automated tools that can provide real-time vulnerability tracking. These tools can detect and report vulnerabilities as soon as they are identified, allowing IT teams to respond promptly and mitigate potential risks.
Generating comprehensive reports for management and stakeholders
Regular reporting is vital for keeping management and stakeholders informed about the current state of the network security. Comprehensive reports should include details about vulnerabilities discovered, their severity levels, and recommendations for remediation. By providing clear and concise reports, IT teams can effectively communicate the risks and necessary actions to key decision-makers.
By following these key components, organizations can establish a robust vulnerability management program that ensures the ongoing security of their IT networks. It’s important to remember that vulnerability management is an ongoing process that requires constant monitoring, assessment, and remediation. With a proactive approach to network security, businesses can minimize the risk of cyberattacks and protect their valuable data.
Program Evaluation and Improvement
Regularly assessing the effectiveness of the program
To ensure the effectiveness of an IT network security vulnerability management program, it is crucial to regularly assess its performance. Monitoring and evaluating different parts of the program, like identifying and fixing vulnerabilities, handling incidents, and following security policies. Regular assessments help identify any weaknesses or gaps in the program and allow for timely adjustments and improvements.
Identifying areas for improvement and implementing necessary changes
To maintain the highest level of security, it is essential to identify areas for improvement within the vulnerability management program. This can be done through comprehensive analysis of past incidents and vulnerabilities, feedback from stakeholders, and benchmarking against best practices. Once areas for improvement are identified, necessary changes should be implemented promptly. This may involve updating policies and procedures, enhancing training programs, or investing in new security technologies.
Keeping up with emerging threats and evolving security technologies
An effective IT network security vulnerability management program must constantly adapt to emerging threats and evolving security technologies. Cybersecurity threats are evolving at a rapid pace, and new vulnerabilities are discovered regularly. It is important to stay up-to-date with the latest threat intelligence and adjust vulnerability management strategies accordingly. Additionally, advancements in security technologies, such as machine learning and artificial intelligence, can enhance the effectiveness of vulnerability management programs. By staying informed and implementing the latest security technologies, organizations can better protect their networks and data.
An effective IT network security program should not only find and fix vulnerabilities, but also evaluate and improve itself to stay protected from new threats.By regularly assessing effectiveness, identifying areas for improvement, and staying abreast of emerging threats, organizations can ensure their networks are protected against potential security breaches.
Conclusion
In conclusion, an effective IT Network Security Vulnerability Management Program is crucial for businesses to protect against the ever-growing threat of cyber attacks. By implementing these five key components – vulnerability assessment, prioritization, remediation, continuous monitoring, and employee education – organizations can significantly reduce their risk of falling victim to security breaches.
Summary of the key componentsof an effective IT Network Security Vulnerability Management Program
- Vulnerability assessment: Regularly scan your network for vulnerabilities and identify potential weaknesses in your IT infrastructure.
- Prioritization: Evaluate the severity and impact of each vulnerability to prioritize remediation efforts based on the level of risk they pose to your systems.
- Remediation: Develop a systematic process for addressing and fixing vulnerabilities, including patching software, updating systems, and implementing security controls.
- Continuous monitoring: Implement real-time monitoring tools to detect and respond to new vulnerabilities or threats as they emerge, ensuring ongoing protection against potential attacks.
- Employee education: Train employees on best practices for cybersecurity, including password hygiene, phishing awareness, and safe internet browsing, to create a strong human firewall against potential breaches.
Importance of investing in a robust program to safeguard against cyber threats
Investing in a robust IT Network Security Vulnerability Management Program is vital for businesses of all sizes. Cyber threats are constantly evolving, and organizations must stay one step ahead to protect their sensitive data, maintain customer trust, and prevent financial losses from breaches or system downtime.
By taking proactive measures to identify and address vulnerabilities, organizations can minimize the potential impact of attacks, reduce downtime, and avoid costly legal and reputational consequences.