
Claude Cowork: The Evolution of Agentic AI and the Dawn of the Autonomous Digital Colleague
Reading Time: 15 minutesTL;DR Claude Cowork is an Autonomous Digital Colleague (high-agency tool) designed to transition AI into the “Agentic Era”...

How Are Executives Thinking About AI in 2026?
Reading Time: 13 minutesSix Mandates: Executive AI Governance in 2026 TL;DR: Executive AI Governance in 2026 AI is a CEO Mandate:...

Sun Tzu’s “The Art of War” and Business Strategy
Reading Time: 11 minutesTable of Contents Sun Tzu and Modern Business Strategy The Enduring Relevance of Ancient Strategic Thought Foundational Strategic...
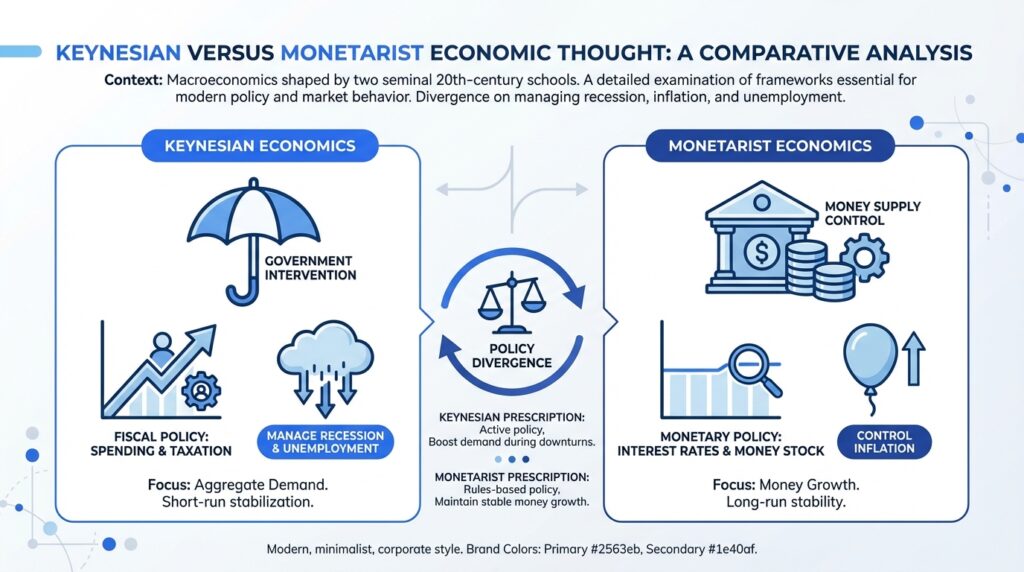
Keynesian vs. Monetarist Economics
Reading Time: 19 minutesKeynesian versus Monetarist Economic Thought: A Comparative Analysis Macroeconomics is mainly influenced by two key theories from the...
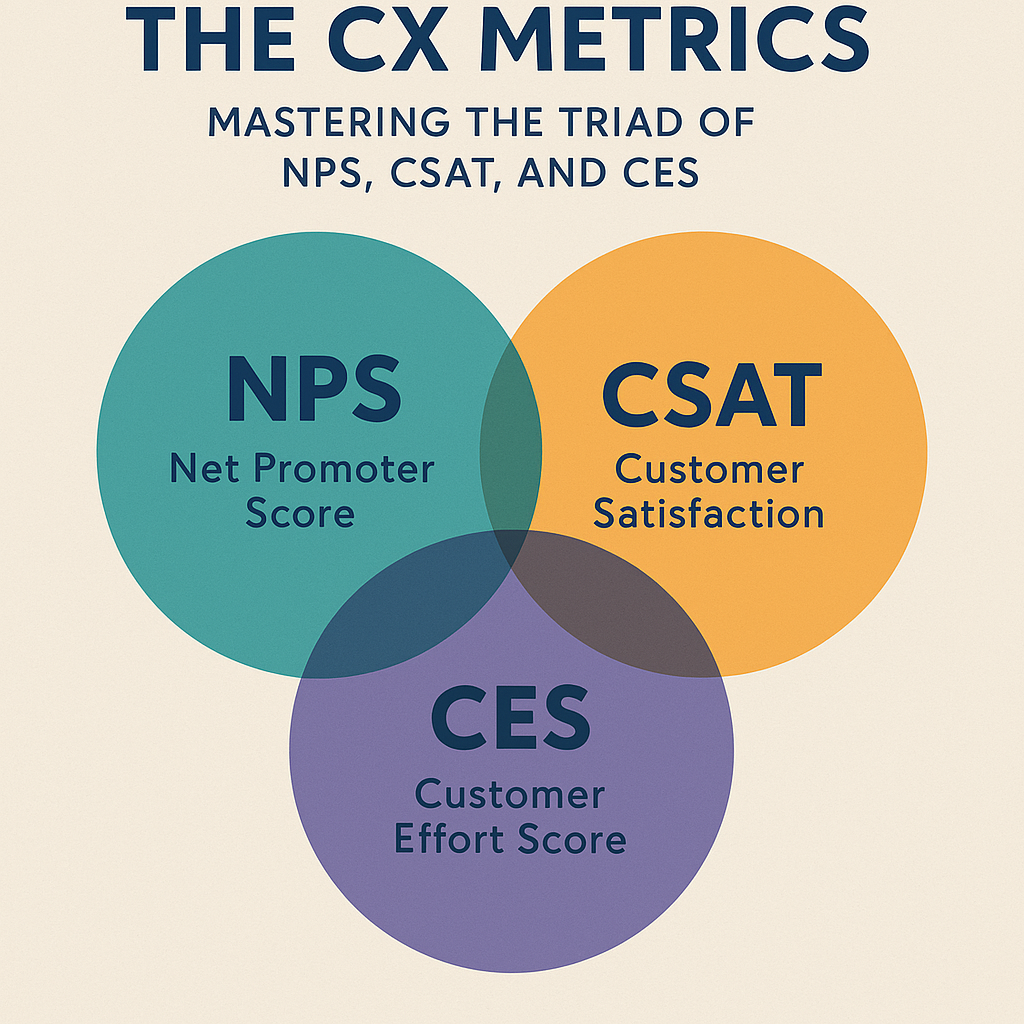
The Key to Customer Success: Implementing NPS, CSAT, and CES Practices
Reading Time: 7 minutesIntroduction Overview of Customer Success Customer success has evolved into a cornerstone of sustainable business growth. It’s not...

The Enterprise Guide to Agentic AI Strategy and Governance
Reading Time: 8 minutesUnderstanding Agentic AI Strategy Definition and Overview Agentic AI refers to autonomous artificial intelligence systems capable of making...

AI Web Browsers: Revolutionizing Online Surfing in 2025 and Beyond
Reading Time: 8 minutesEvolution of Web Browsers History of Web Browsers Web browsers started in the early 1990s when Tim Berners-Lee...

Keynesian Economics: A Comprehensive Analysis
Reading Time: 8 minutesOverview of Keynesian Economics Introduction to Keynesian Economics Keynesian Economics, named after the British economist John Maynard Keynes,...

Jaguar Land Rover Cybersecurity Breach August 2025
Reading Time: 2 minutesIn August 2025, Jaguar Land Rover (JLR) experienced a significant cyberattack that stopped global manufacturing for over six...

Git for Beginners: The What, Why, and How Made Easy
Reading Time: 9 minutesIntroduction Understanding the Basics of Git Git is a powerful version control system that has revolutionized the way...

The Seven Cs of Effective Communication
Reading Time: 8 minutesOverview of Effective Communication Definition and Importance of Effective Communication Effective communication means clearly and persuasively sharing information...

Microsoft Purview: The Must-Have Tool for Data Management
Reading Time: 6 minutesIntroduction Overview of Microsoft Purview In today’s complex digital landscape, businesses continually grapple with vast amounts of data....
Azure DevOps Empowers Developers: A Complete Overview
Reading Time: 7 minutesIntroduction Overview of Azure DevOps Azure DevOps is a comprehensive suite of tools and services designed to support...
Windows Autopilot: Setup, Requirements, and Challenges
Reading Time: 6 minutesIntroduction Overview of Windows Autopilot Windows Autopilot is a modern deployment tool designed to streamline the process of...

Small Language Models: A General Introduction
Reading Time: 7 minutesOverview of Small Language Models Definition of Small Language Models Small language models are AI that perform natural...

Google Breach From Voice Phishing to Extortion
Reading Time: 7 minutesOverview of Google Breach Incident Summary of the Incident In June, Google discovered a breach in its Salesforce...
ISO 42001 AI Management System: A Comprehensive Guide
Reading Time: 7 minutesOverview of ISO 42001 ISO 42001 is a standard that helps organizations with sustainable management, promoting environmental and...

GPT-5: Theory and Practise
Reading Time: 7 minutesIntroduction Overview of GPT-5 GPT-5, the latest version of OpenAI’s Generative Pre-trained Transformer series, marks a major advancement...

The Future of Shopping: Exploring the Rise of Agentic Commerce
Reading Time: 7 minutesIntroduction Definition of Agentic Commerce Agentic commerce is a new shopping trend that allows consumers more control over...

America's AI Action Plan: From Vision to Execution
Reading Time: 6 minutesBackground of America’s AI Action Plan Overview of AI Action Plan The AI Action Plan represents a comprehensive...

The Learning-Innovation Nexus: Decoding the Connection
Reading Time: 6 minutesThe Interplay Between Learning and Innovation Defining Learning and Innovation At the core of any successful venture or...

Qantas Cybersecurity Fallout: Understanding the Data Breach
Reading Time: 7 minutesOverview of Qantas Data Breach Incident Brief Background of Qantas Qantas, Australia’s flag carrier, is renowned for its...

From Traditional to Agile: Transforming Leadership in the Digital Age
Reading Time: 8 minutesUnderstanding Traditional Leadership Definition of Traditional Leadership Traditional leadership is often defined as a management style characterized by...

Self-Determination Theory (SDT): The Key to Motivation and Personal Growth
Reading Time: 7 minutesOverview of Self-Determination Theory Definition of Self-Determination Theory Self-Determination Theory (SDT) is a psychological framework that emphasizes the...

Positive Organizational Behavior: Strategies for Organizations
Reading Time: 11 minutesIntroduction Definition of Positive Organizational Behavior Positive Organizational Behavior (POB) refers to the study and application of positive...

In Search of Excellence: Inspirations from Peters and Waterman
Reading Time: 7 minutesIntroduction Overview of In Search of Excellence “In Search of Excellence” by Tom Peters and Robert Waterman, published...

Unleashing the Power of Marketing: Insights from Seth Godin
Reading Time: 9 minutesOverview of Seth Godin Background and Career Seth Godin is not just a marketing expert; he’s a visionary...

The Model Context Protocol (MCP): Overview and Applications
Reading Time: 7 minutesOverview of the Model Context Protocol Definition of the Model Context Protocol The Model Context Protocol (MCP) is...
Generative Engine Optimization: A Comprehensive Guide
Reading Time: 7 minutesIntroduction Understanding Generative Engine Optimization In today’s digital landscape, businesses face an ever-increasing competition. Generative Engine Optimization (G.E.O.)...
Mastering Social Media Dashboards: Best Practices for Digital Marketing Success
Reading Time: 7 minutesIntroduction Overview of Social Media Dashboards In today’s fast-paced digital landscape, Social Media Dashboards act as the command...

IBM X-Force Threat Intelligence Index 2025
Reading Time: 8 minutesOverview of IBM X-Force 2025 Threat Intelligence Index Introduction to IBM X-Force 2025 Threat Intelligence Index The IBM...

Mandiant's M-Trends 2025 Report
Reading Time: 6 minutesOverview of Mandiant’s M-Trends 2025 Report Introduction to Mandiant Mandiant, a leader in cybersecurity, has excelled in incident...

The Microsoft 2025 Work Trend Index Report
Reading Time: 7 minutesThe Birth of the Frontier Firm: Navigating the AI Revolution in Business We stand on the precipice of...

Microsoft 365 Copilot: A Comprehensive Guide
Reading Time: 7 minutesOverview of Microsoft 365 Copilot Microsoft 365 Copilot is an innovative tool designed to enhance productivity within the...

Cybersecurity Adoption in the Workplace
Reading Time: 9 minutesIntroduction Overview of Literature Review on Cybersecurity Adoption in the Workplace In today’s digitally driven world, the significance...

Groupthink Demystified: Tips for Encouraging Critical Thinking
Reading Time: 4 minutesUnderstanding Groupthink Definition and Explanation of Groupthink To tackle the challenges posed by groupthink, it is essential first...

Transforming Marketing Operations: The AI and Machine Learning Evolution
Reading Time: 7 minutesIntroduction The Rise of AI and Machine Learning in Marketing Operations In recent years, the marketing landscape has...

Generative AI Adoption in the Workplace
Reading Time: 7 minutesOverview of Generative AI Adoption in the Workplace Definition of Generative AI Generative AI is a class of...

Mastering Marketing through the Lens of Behavioral Economics
Reading Time: 7 minutesIntroduction Understanding Behavioral Economics in Marketing Behavioral economics merges principles of psychology and economics, offering valuable insights into...

Strategic Listening: Your Key to Building Stronger Connections and Achieving Goals
Reading Time: 8 minutesIntroduction Definition of Strategic Listening Strategic listening is more than just passively hearing words; it’s an intentional process...
Content Marketing Trends to Watch in 2025 and How to Adapt
Reading Time: 7 minutesOverview of Content Marketing Trends by 2025 Definition of Content Marketing Content marketing is a strategic marketing approach...

Innovative Marketing Strategies: Harnessing Digital Transformation
Reading Time: 8 minutesIntroduction Definition of Digital Transformation in Marketing Digital transformation in marketing refers to integrating digital technology into all...

Brand Refresh: Signs It’s Time to Revamp Your Brand Identity
Reading Time: 7 minutesUnderstanding Brand Identity Refresh Definition of Brand Identity Brand identity encompasses all the elements that signify and define...
AI Strategies for Marketing Success
Reading Time: 7 minutesIntroduction Understanding AI in Marketing Artificial intelligence (AI) has emerged as a marketing game-changer in today’s fast-paced digital...
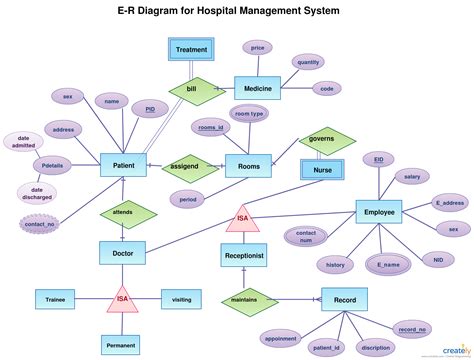
Entity Relationship Diagrams (ERD): A Comprehensive Guide for Beginners
Reading Time: 8 minutesIntroduction What is an Entity Relationship Diagram (ERD)? Entity Relationship Diagrams, commonly known as ERDs, are powerful visual...

The Rise of AI Agents Replacing Traditional Software
Reading Time: 7 minutesThe Evolution of Software Development Historical Overview The journey of software development is as fascinating as it is...
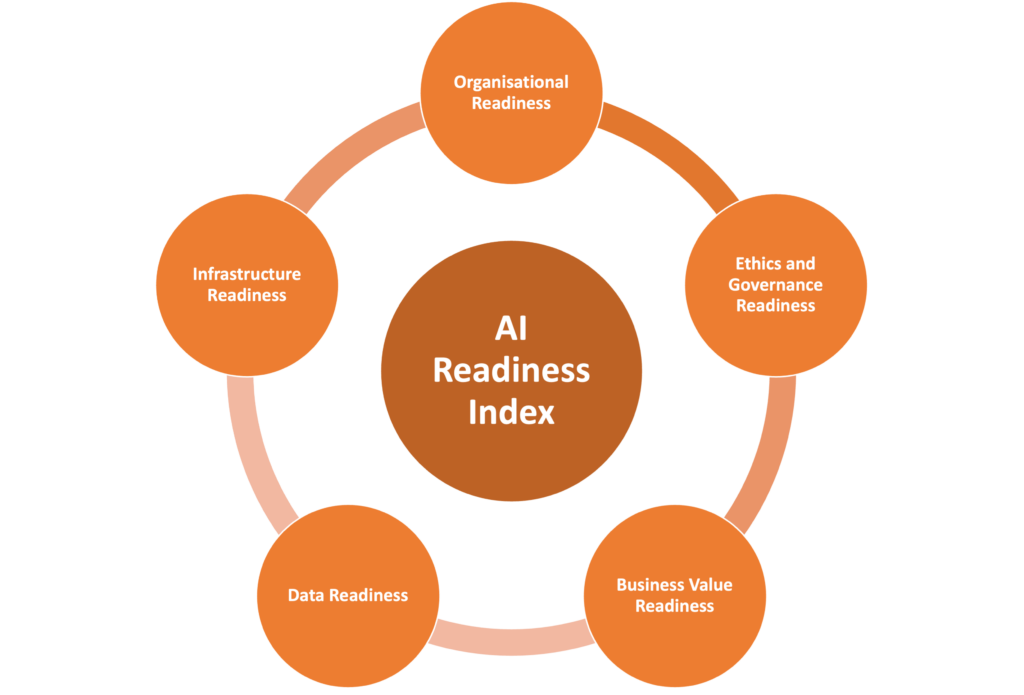
Technology Readiness Index (TRI): A Roadmap for Enhancing Business Technology Capacities
Reading Time: 6 minutesTechnology Readiness Index: A Roadmap for Enhancing Business Technology Capacities The Technology Readiness Index (TRI) is a vital...
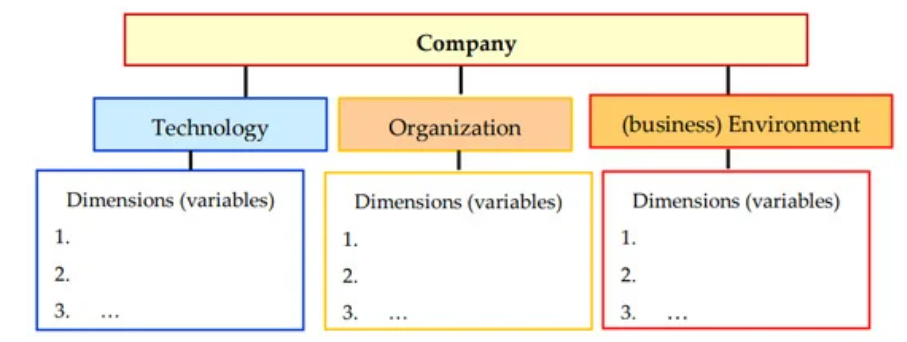
Technology-Organization-Environment (TOE) Framework
Reading Time: 7 minutesOverview of the Technology-Organization-Environment (TOE) Framework Definition and Meaning of TOE Framework The Technology-Organization-Environment (TOE) framework offers a...
Unified Theory of Acceptance and Use of Technology (UTAUT) Demystified: Understanding User Attitudes Towards Technology
Reading Time: 7 minutesIntroduction Overview of Unified Theory of Acceptance and Use of Technology (UTAUT) The Unified Theory of Acceptance and...
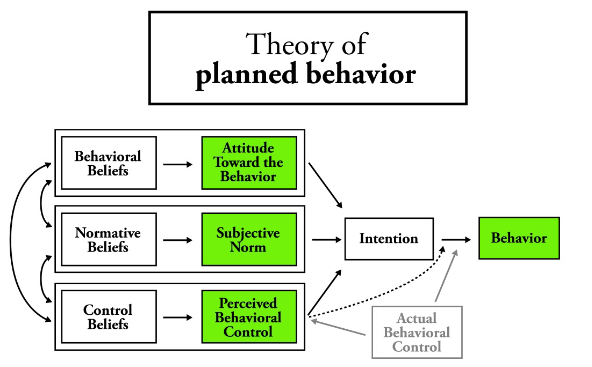
Theory of Planned Behavior (TPB): How to Apply the Theory in Real-Life Situations
Reading Time: 7 minutesIntroduction Overview of the Theory of Planned Behavior (TPB) The Theory of Planned Behavior (TPB) provides a comprehensive...
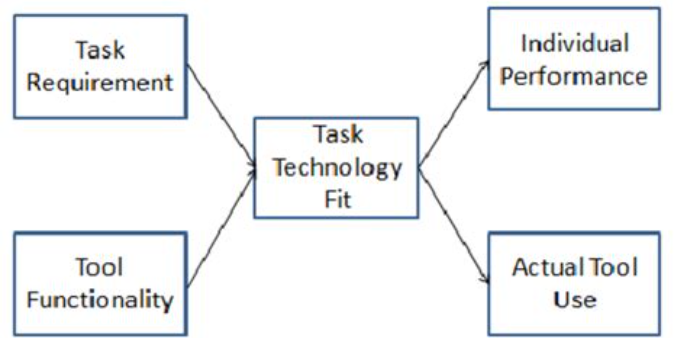
Task-Technology Fit (TTF) Model: Theory and Practice
Reading Time: 7 minutesOverview of the Task-Technology Fit (TTF) Model Definition and Background The Task-Technology Fit (TTF) Model is a theoretical...
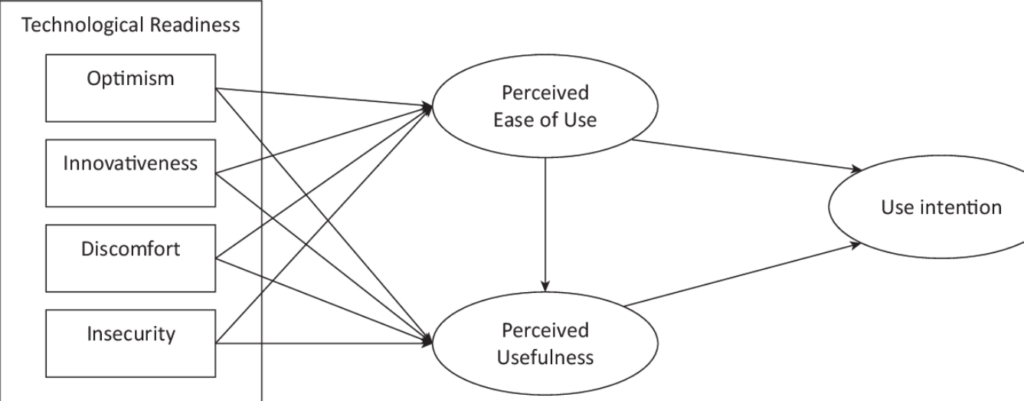
Technology Readiness and Acceptance Model (TRAM): A Comprehensive Guide to Technology Readiness and Acceptance
Reading Time: 7 minutesIntroduction Definition of Technology Readiness and Acceptance Model (TRAM) The Technology Readiness and Acceptance Model (TRAM) is a...
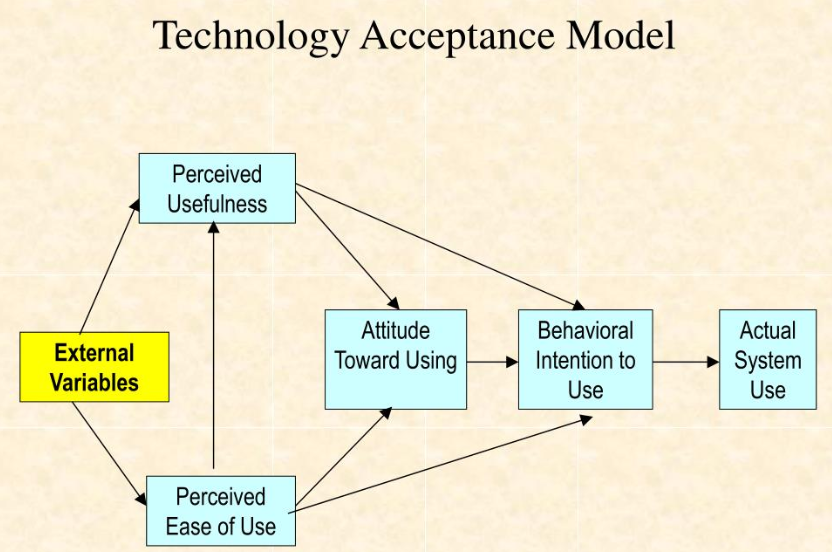
Technology Acceptance Model (TAM) Explained: A Deep Dive into User Adoption
Reading Time: 8 minutesOverview of the Technology Acceptance Model (TAM) Introduction to TAM The Technology Acceptance Model (TAM) is a pivotal...

SEO: Tips and Tricks for Optimizing Your Site for Search Engines
Reading Time: 8 minutesIntroduction to SEO What is SEO? Search Engine Optimization (SEO) enhances a website’s visibility on search engines like...
Identity and Access Management: The Key to Protecting Your Data and Privacy
Reading Time: 8 minutesIntroduction Importance of Identity and Access Management In today’s digital landscape, the significance of Identity and Access Management...
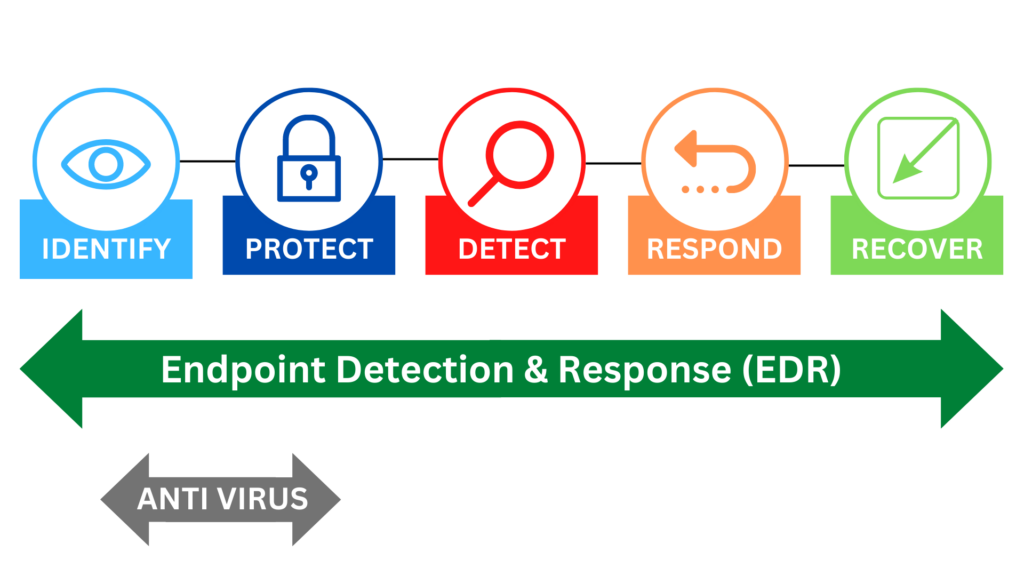
EDR Landscape: A Deep Dive into Market Trends, Leading Vendors, and Cutting-Edge Technology
Reading Time: 8 minutesOverview of EDR Landscape In today’s digital world, where cyber threats seem to evolve faster than our ability...

Medibank Breach of 2022: A Detailed Analysis
Reading Time: 7 minutesIntroduction Overview of the Medibank Breach In late 2022, the healthcare sector faced a significant challenge as Medibank,...
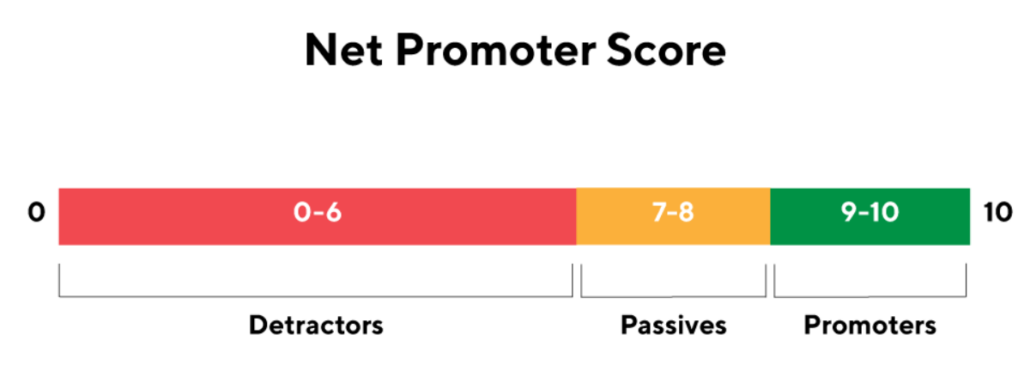
NPS: Strategies to Enhance Customer Loyalty and Boost Business Growth
Reading Time: 9 minutesIntroduction Understanding NPS The Net Promoter Score (NPS) has emerged as a leading metric for understanding customer loyalty...

Penetration Testing Execution Standard (PTES): A Comprehensive Guide
Reading Time: 7 minutesIntroduction to Penetration Testing Execution Standard (PTES) As organizations increasingly rely on technology, the need for effective cybersecurity...
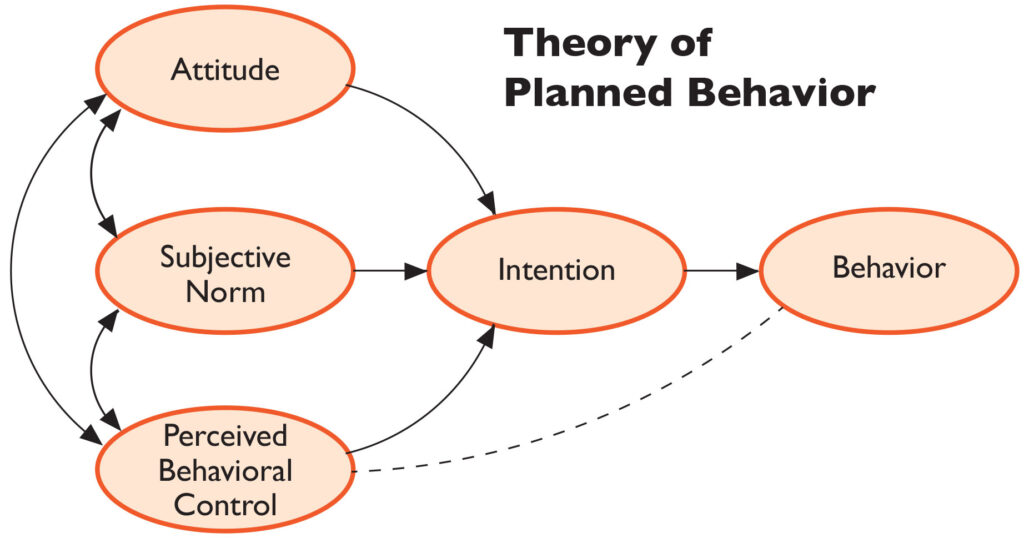
The Theory of Planned Behaviour: A Guide to Successful Technology Adoption
Reading Time: 9 minutesIntroduction The Theory of Planned Behaviour (TPB) is a widely recognized psychological theory that provides insights into human...

The Crowdstrike Service Disruption in July 2024
Reading Time: 6 minutesIntroduction Overview of the Crowdstrike Service Disruption in July 2024 In July 2024, Crowdstrike, a leading cybersecurity firm,...

The Bangladesh Bank Cybersecurity Crisis 2016: Lessons Learned and Future Implications
Reading Time: 6 minutesIntroduction Background of The Bangladesh Bank Cybersecurity Crisis The Bangladesh Bank cybersecurity crisis, which unfolded in early 2016,...
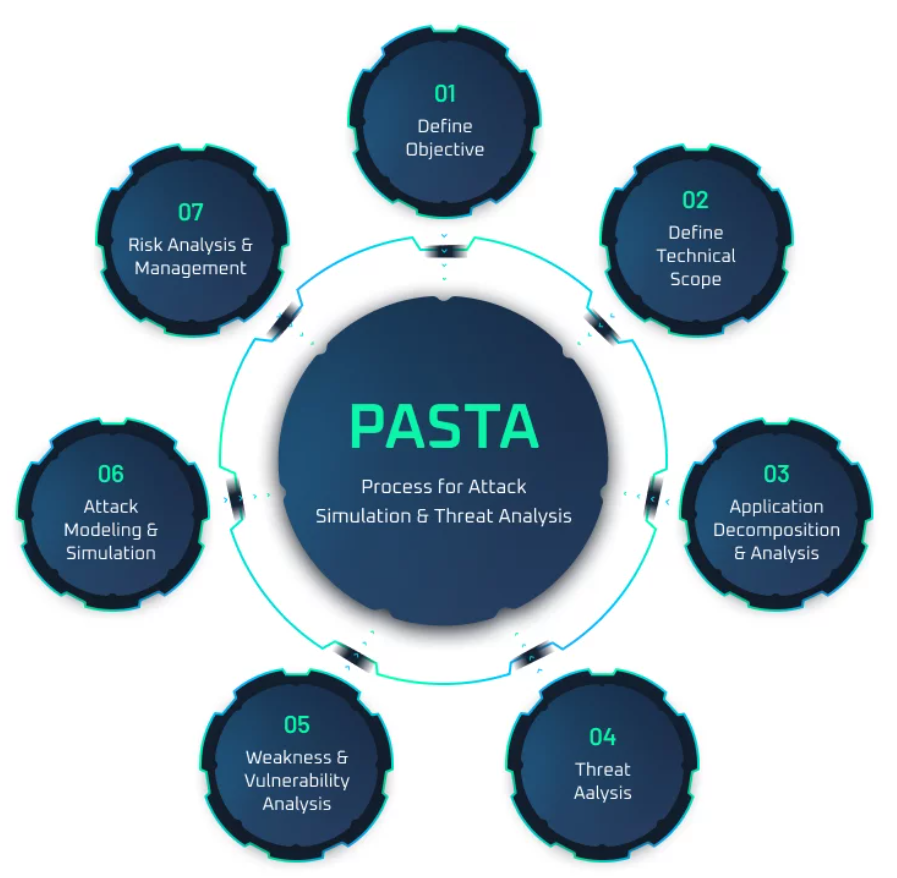
PASTA Threat Model Framework: A Comprehensive Guide
Reading Time: 8 minutesIntroduction to PASTA Threat Model Framework Source: threat-modeling.com Overview of PASTA Threat Model Framework The PASTA Threat Model...

Password Attacks
Reading Time: 5 minutesDefinition of password attacks A password attack is an unauthorised attempt to access a user’s account or system...

Social Media Marketing: Strategic Steps to Success
Reading Time: 7 minutesUnderstanding Your Target Audience Identifying and understanding the target audience is crucial in social media marketing. By pinpointing...

Cybersecurity Hacks: The Top 10 That Shook the World
Reading Time: 10 minutesIntroduction In today’s digital age, the importance of cybersecurity cannot be overstated. A single cyber attack can have...
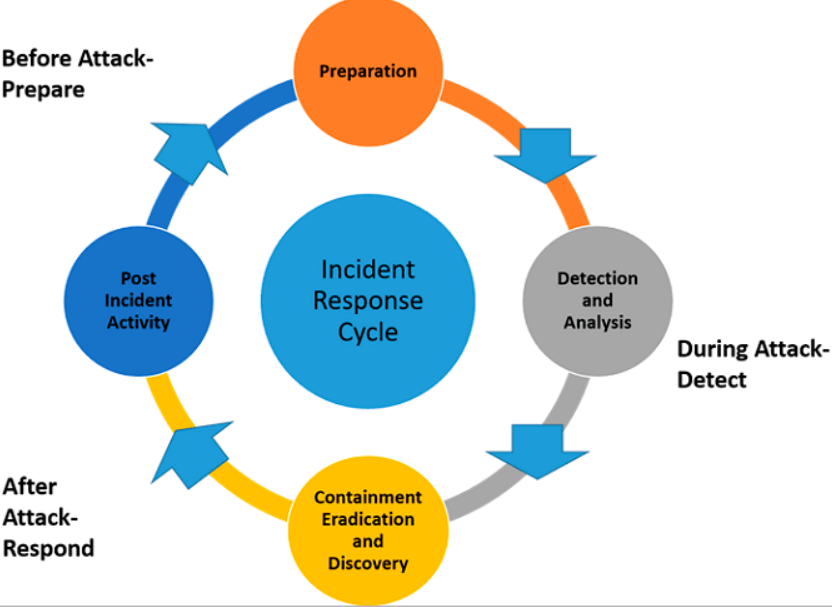
The NIST Incident Response Lifecycle: From Detection to Recovery
Reading Time: 10 minutesIntroduction The NIST Incident Response Lifecycle is a comprehensive framework organizations can use to effectively manage and respond...

Virtual Machines: A Beginner's Guide
Reading Time: 9 minutesIntroduction to Virtual Machines Considering diving into the world of virtualization? Look no further! This beginner’s guide will...

Qualitative Data Analysis: A Beginner’s Guide
Reading Time: 7 minutesIntroduction to Qualitative Data Analysis Qualitative data analysis is an important part of research because it helps us...

Survey Design Secrets: Engaging Techniques for High Participation
Reading Time: 7 minutesImportance of Survey Design Source: www.snapsurveys.com Survey design plays a crucial role in ensuring high participation rates. A...

The Hawthorne Effect: How It Shaped Today's Management Strategies
Reading Time: 8 minutesIntroduction to the Hawthorne Effect The Hawthorne Effect, named after a series of studies conducted in the 1920s...

Building a Culture of Cybersecurity: Strategies for Employee Adoption
Reading Time: 7 minutesImportance of Building a Culture of Cybersecurity In today's digital age, building a culture of cybersecurity is of...

The Essentials 8 Cybersecurity Framework is Vital for Australian Businesses
Reading Time: 6 minutesUnderstanding the Essentials 8 Cybersecurity Framework Overview of the Essentials 8 Cybersecurity Framework In the digital age, cybersecurity...
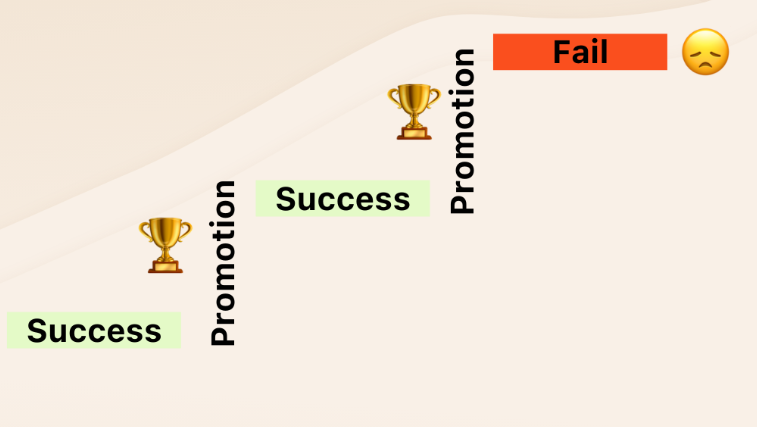
The Peter Principle: How to Promote Based on Potential, Not Performance
Reading Time: 8 minutesUnderstanding the Peter Principle The Peter Principle refers to the phenomenon where individuals are promoted to positions of...
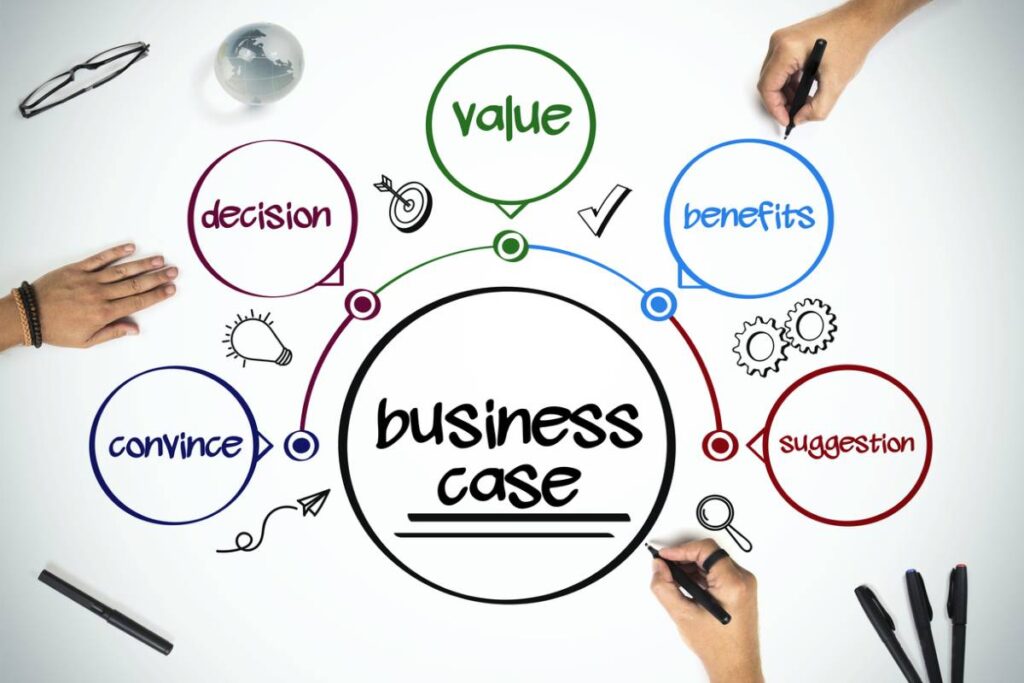
The Business Case: 5 Essential Components To Writing One
Reading Time: 8 minutesIntroduction to Business Cases A business case is a crucial document that outlines the justification and potential benefits...

Technology and The Business Case
Reading Time: 10 minutesUnderstanding Your Business Needs and Goals Tie technology to a business case The decision should start with these...

Phishing Emails: How to Identify, Prevent, and Protect Yourself from Online Scams
Reading Time: 4 minutesWe’ve all heard about phishing emails, but do we know what they are and how to protect ourselves?...
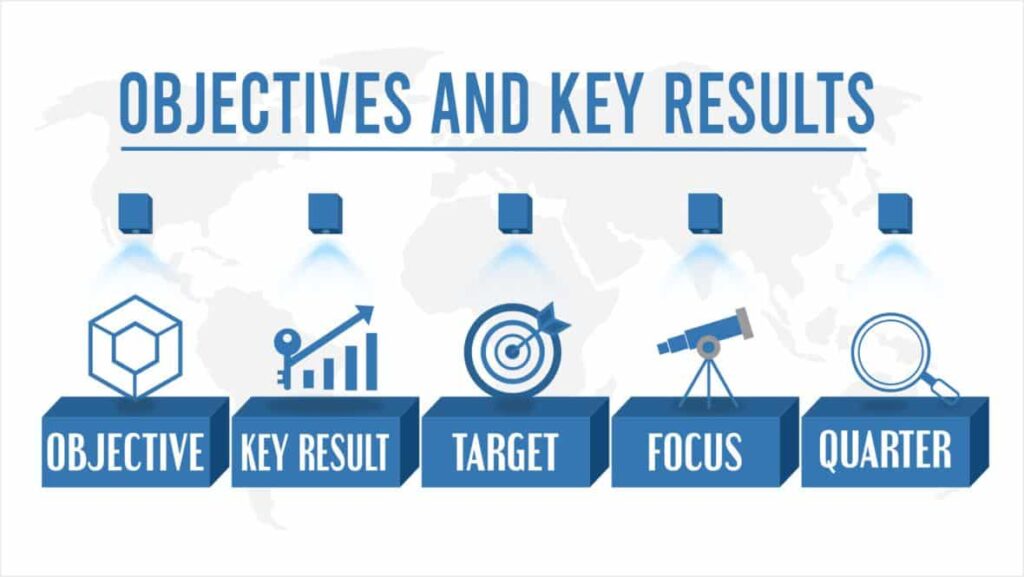
OKRs: A Comprehensive Guide to Boosting Goal-setting and Performance
Reading Time: 3 minutesWelcome to our comprehensive guide on demystifying OKRs, a goal-setting framework that can boost performance and drive organisational...

Ansoff Matrix for Strategic Planning
Reading Time: 2 minutes The Ansoff Matrix is a strategic management tool that helps businesses to identify the possible ways they...

LastPass Hacked Many Times: A Deep Dive into the Vulnerabilities
Reading Time: 10 minutesIntroduction Source: duet-cdn.vox-cdn.com LastPass is a popular password management tool known for its convenience and ability to securely...
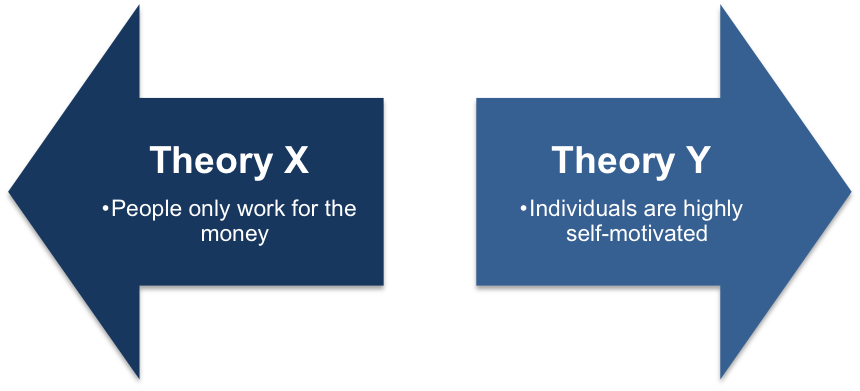
McGregor Theory X and Y
Reading Time: 2 minutesMcGregor Theory X and Y: Understanding Management Styles for Organisational Success In the realm of organisational behaviour and...

The Colonial Pipeline Cyberattack
Reading Time: 12 minutesOverview of the Colonial Pipeline Cyber Attack The Colonial Pipeline cyberattack was a big event that affected the...
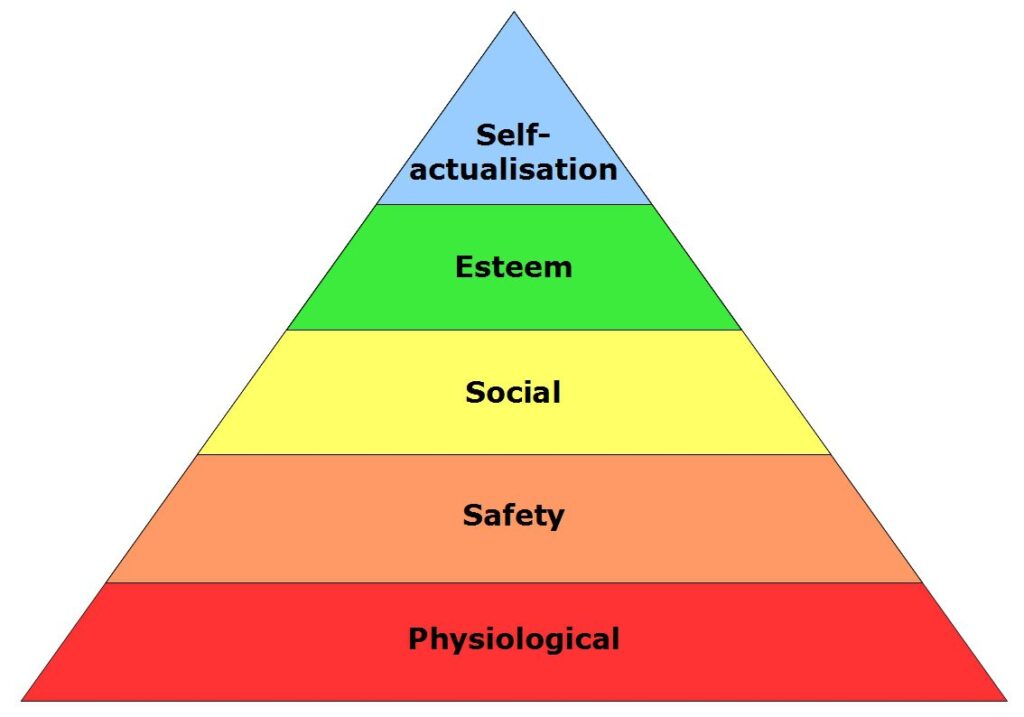
Maslow’s Hierarchy of Needs
Reading Time: 2 minutesMaslow’s Hierarchy of Needs Theory: A Foundation for Effective Management Maslow’s Hierarchy of Needs Theory is one of...

Martech For Marketers
Reading Time: 10 minutesWelcome to our blog post on Martech for Marketers! In today’s digital age, marketing and technology go hand...
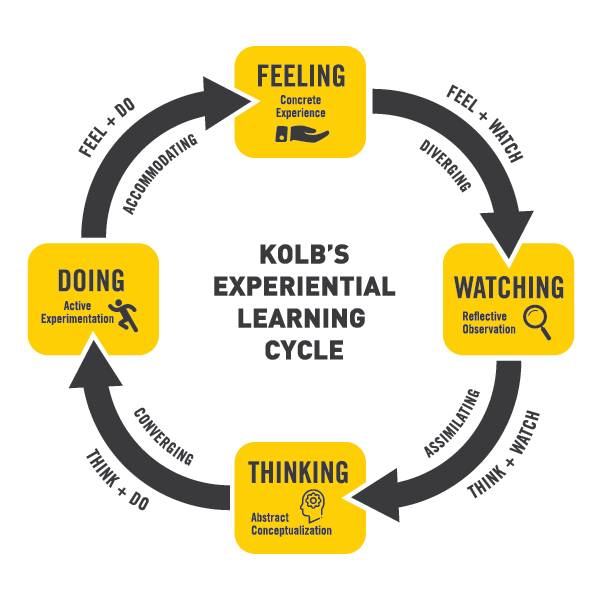
Kolb Learning Cycle
Reading Time: 2 minutesKolb Learning Cycle: A How-To Guide The Kolb Learning Cycle is a model that outlines the different stages...
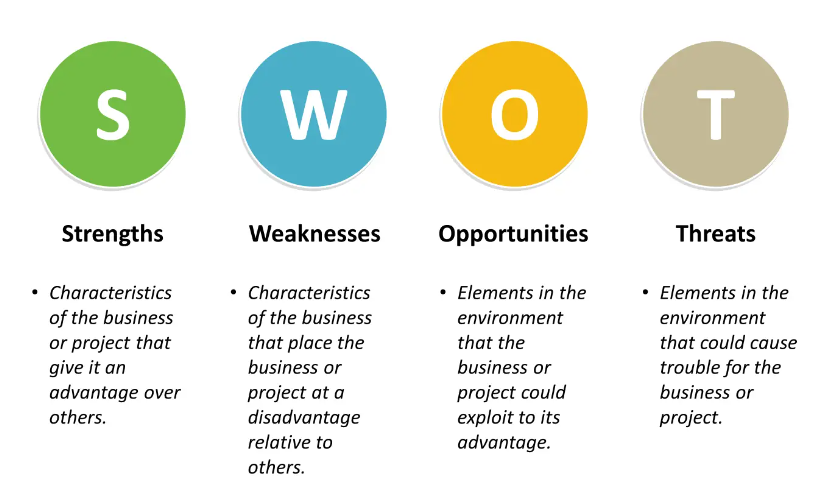
SWOT Analysis
Reading Time: 3 minutesA SWOT analysis is a strategic planning technique used to assess an organization’s strengths, weaknesses, opportunities, and threats....

Cash Flow Statements: Understanding the Basics
Reading Time: 9 minutesIntroduction Understanding cash flow statements is essential for businesses of all sizes. Cash flow statements provide valuable insights...

Okta Breach: A Deep Dive into the Attack
Reading Time: 11 minutesIntroduction In the world of cybersecurity, even a breach at a highly reputable company like Okta can serve...
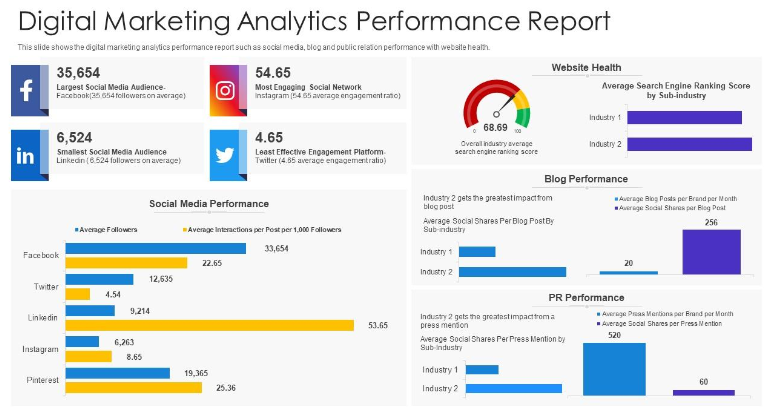
Digital Marketing Analytics
Reading Time: 3 minutesHow To Guide: Utilizing Digital Marketing Analytics for Optimal Results In the world of digital marketing, analytics play...

CNA Financial Hit by $40M Ransomware Attack: What We Need to Know
Reading Time: 8 minutesIntroduction CNA Financial, a top US insurance company, was recently targeted by a major ransomware attack. The company...
GAI: How Generative Artificial Intelligence is Changing the Game
Reading Time: 8 minutesIntroduction Generative Artificial Intelligence (GAI) is revolutionizing various industries with its ability to bring new possibilities and advancements....

Pavlov's Dog and the Power of Association: How Our Minds Learn and Adapt
Reading Time: 10 minutesIntroduction Pavlov’s Dog and the Power of Association: How Our Minds Learn and Adapt Ivan Pavlov’s experiment with...

CSPM vs DSPM
Reading Time: 9 minutesIntroduction In today’s digital landscape, ensuring the security and protection of data has become a top priority for...
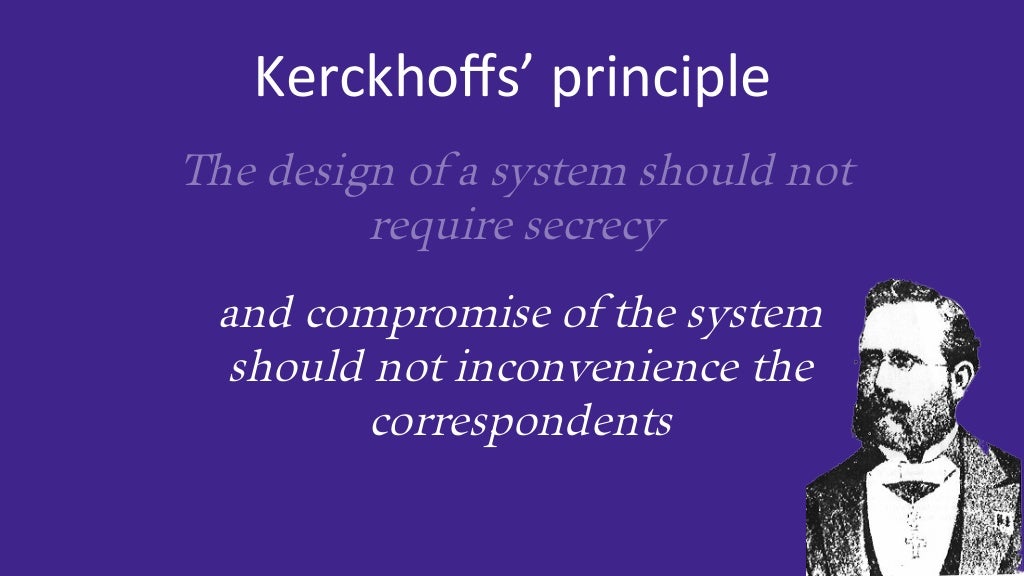
Kerckhoffs Principle vs Security Through Obscurity: Which is Better?
Reading Time: 10 minutesIntroduction to Kerckhoffs' Principle Kerckhoffs' Principle, also called the "principle of the open door," says that the security...
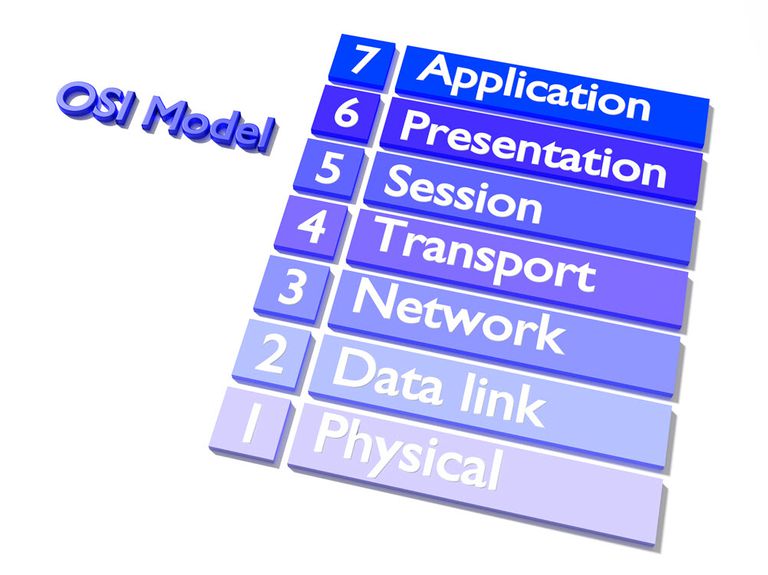
The OSI Model: How Layers Work Together
Reading Time: 7 minutesIntroduction The OSI (Open Systems Interconnection) Model is a conceptual framework that standardises the functions of a communication...

Citrix Hack of 2023
Reading Time: 9 minutesIntroduction In 2023, the technology industry was hit by a major cybersecurity incident when Citrix, a leading software...
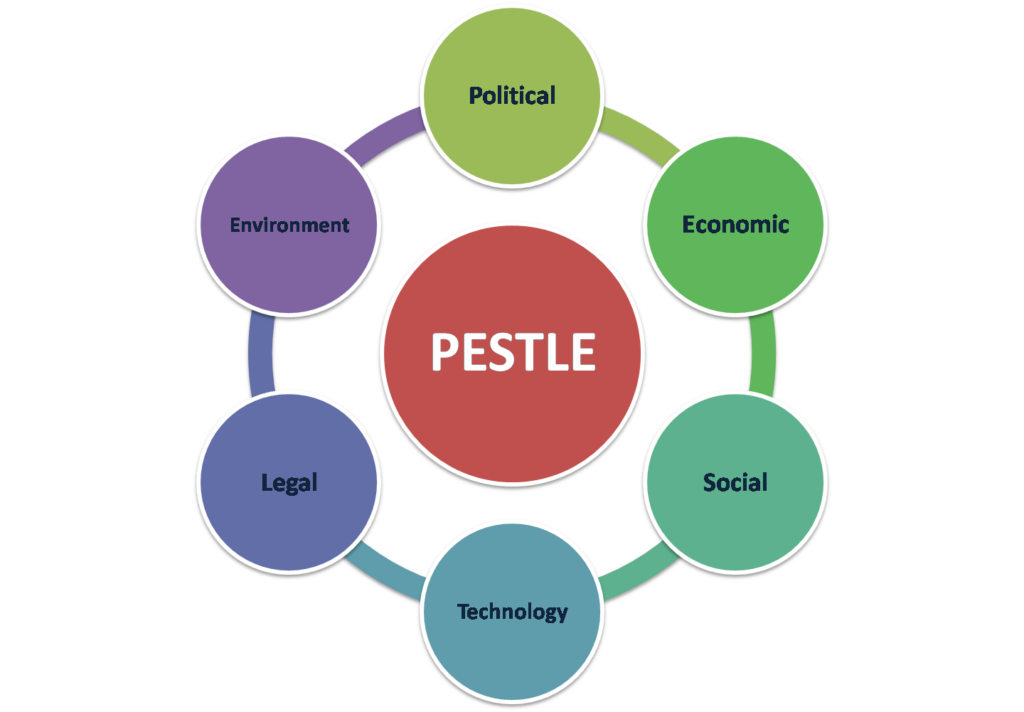
PESTLE Analysis for Business Strategy
Reading Time: 2 minutesA Pestle Analysis is a strategic tool used to assess the external macro-environmental factors that may impact an...

The SolarWinds Cybersecurity Breach: What We Need to Know
Reading Time: 11 minutesIntroduction In recent years, cybersecurity breaches have become a growing concern for businesses and individuals alike. The SolarWinds...
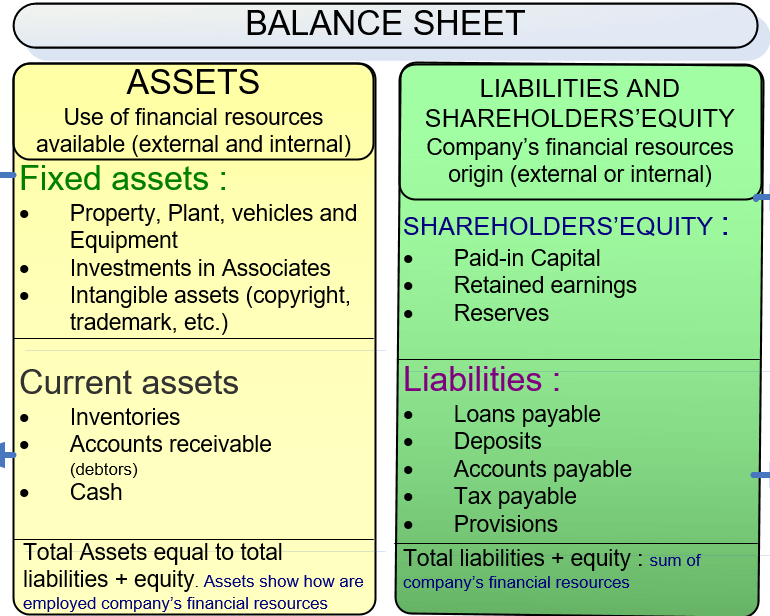
The Balance Sheet: A Guide For Managers
Reading Time: 11 minutesIntroduction to the Balance Sheet Understanding the purpose and importance of the balance sheet The balance sheet shows...

Wannacry: The Cyber Attack That Shook the World
Reading Time: 10 minutesOverview of the Wannacry Cyberattack The Wannacry cyberattack occurred in May 2017 and targeted computers running the Microsoft...

The Optus Cybersecurity Incident
Reading Time: 8 minutesIntroduction In today’s digital landscape, cybersecurity is of utmost importance to protect sensitive information and maintain the trust...

Incident Response: Its Role in Cybersecurity
Reading Time: 10 minutesIntroduction Incident response refers to the process of effectively and efficiently addressing and managing cybersecurity incidents within an...

Voice of the Customer: Crucial for Business Success
Reading Time: 8 minutesIntroduction In the competitive business landscape, understanding and meeting the needs of customers is crucial for success. One...

Profit Loss Statements: A Guide for Managers
Reading Time: 9 minutesIntroduction to Profit Loss Statements A Profit Loss statement, also called an income statement or earnings statement, is...
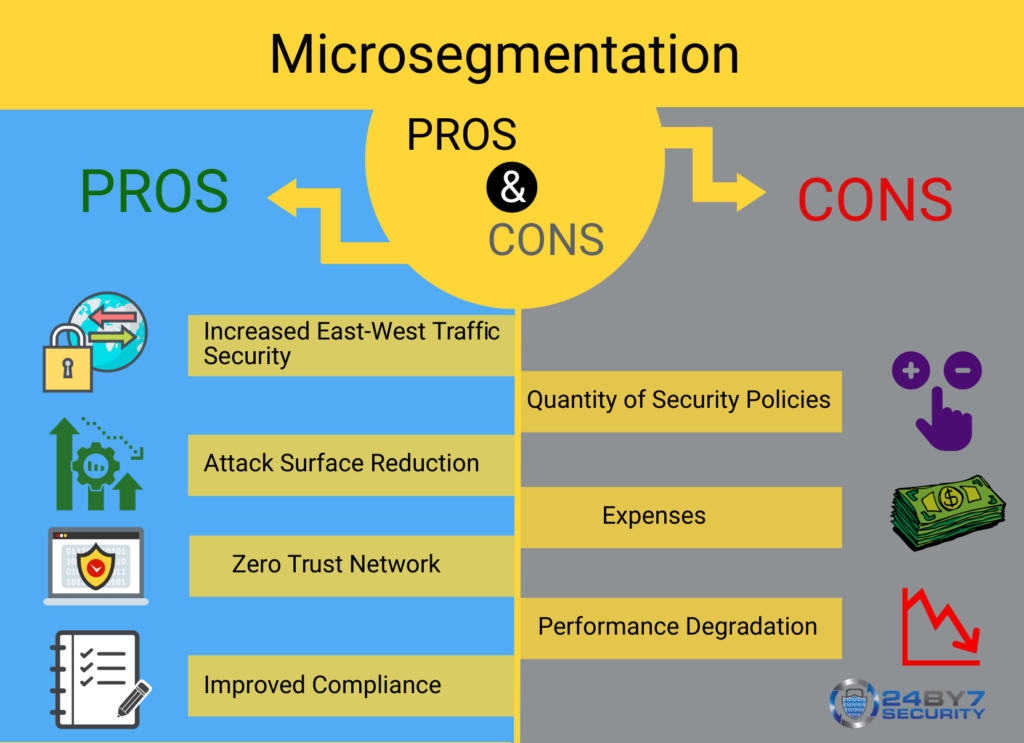
Network Microsegmentation: Protecting Your Business from Cyber Threats
Reading Time: 10 minutesIntroduction Network microsegmentation is a crucial component of any comprehensive cybersecurity strategy. In today’s digital landscape, where cyber...

Cybersecurity Adoption in the Workplace
Reading Time: 10 minutesImportance of Cybersecurity for Organizations 1. Understanding the significance of cybersecurity Cybersecurity has become a critical aspect of...

Social Media Marketing Strategy: How To Create One
Reading Time: 10 minutesIntroduction In today's digital age, social media has become anintegral tony successful marketing strategy. But how do you...

The MGM Cyberattack: A Closer Look at What Happened
Reading Time: 5 minutesIntroduction The MGM cyberattack is one of the most notable instances of a company falling victim to a...
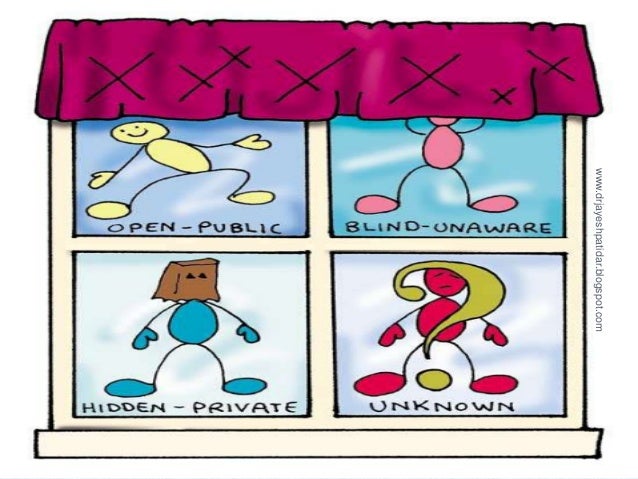
The Johari Window and its benefits to communication
Reading Time: 7 minutesIntroduction The Johari Window is a valuable tool in communication that can enhance self-awareness, create openness, and improve...
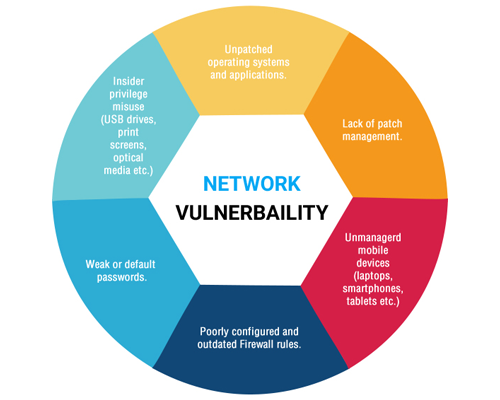
Effective IT Network Security Vulnerability Management Program
Reading Time: 8 minutesIntroduction An effective IT network security vulnerability management program is essential for businesses to protect their sensitive data...

URL Filtering versus DNS Filtering
Reading Time: 9 minutesIntroduction URL filtering and DNS filtering are two popular methods used to control and manage internet access within...
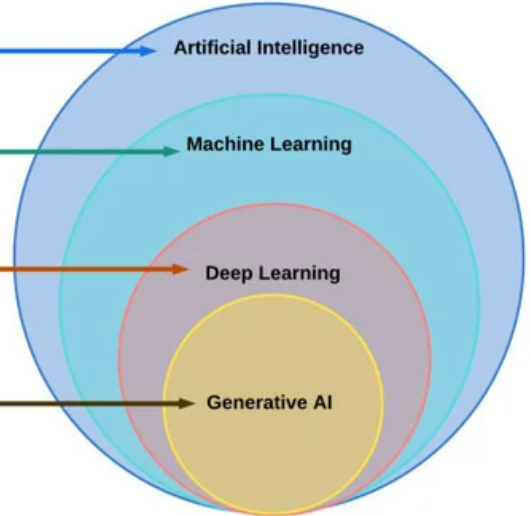
AI, Generative AI, and Machine Learning: What’s the Difference?
Reading Time: 10 minutesIntroduction Artificial Intelligence (AI), Generative AI, and Machine Learning are three intersecting fields that have gained significant attention...
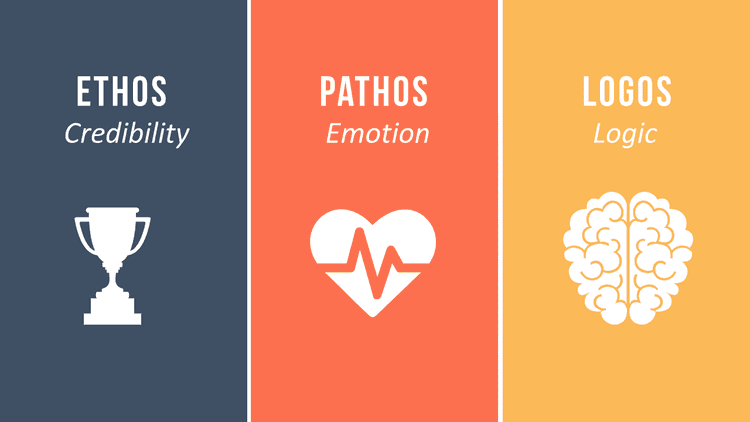
Ethos, Pathos, and Logos: The Ultimate Guide to Persuasive Writing
Reading Time: 11 minutesIntroduction In the realm of effective writing, mastering the concepts of ethos, pathos, and logos is essential for...
Computer Protocols: Exploring the Backbone of the Internet
Reading Time: 10 minutesIntroduction In the vast and interconnected world of the internet, computer protocols serve as the backbone that enables...

Vulnerability Measuring and Scoring
Reading Time: 11 minutesIntroduction to Vulnerabilities and Exploits In the world of cybersecurity, vulnerabilities and exploits play a critical role in...

The Target Data Breach: How Hackers Stole Millions of Customer Records
Reading Time: 9 minutesIntroduction The Target data breach in 2013 sent shockwaves through the retail industry and raised concerns about the...

Management Theories
Reading Time: 3 minutesOrganization management is the process of planning, organizing, and controlling resources to achieve specific goals. Over time, management...

Strategic Planning for Businesses
Reading Time: 2 minutesStrategic planning is a process of defining, developing, and implementing a company’s long-term goals and objectives. In simple...

Microsoft Clarity
Reading Time: 2 minutesMicrosoft Clarity is a web analytics tool that helps website owners understand their visitors’ behaviour. It allows website...
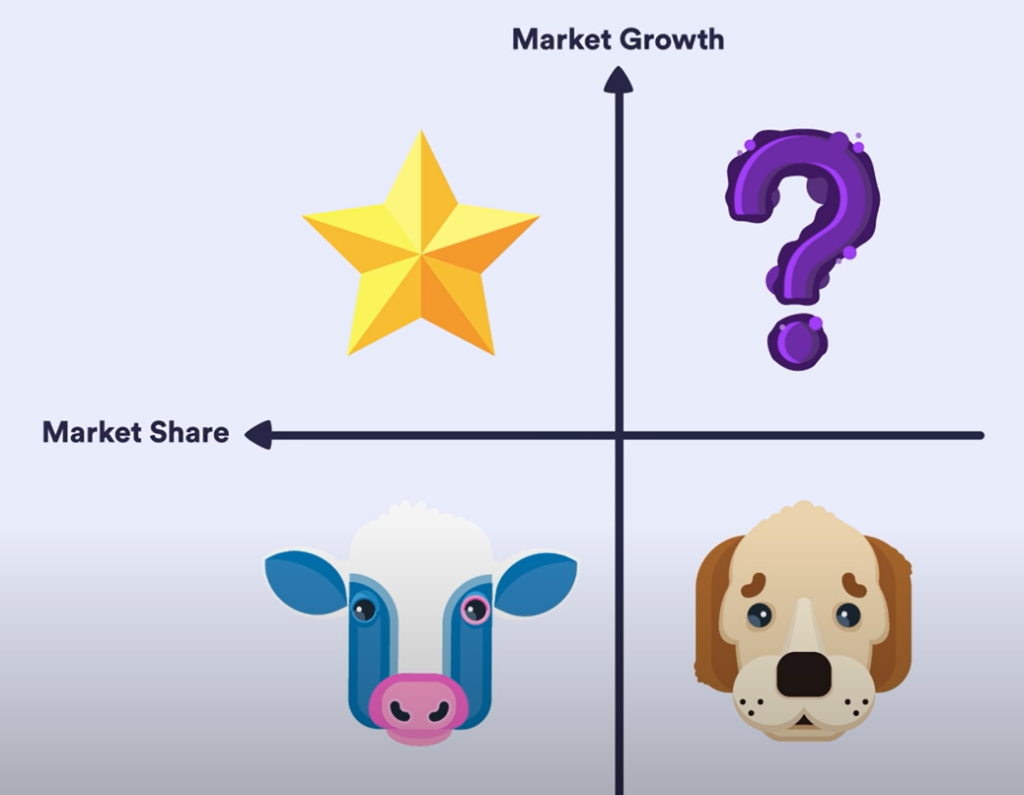
The BCG Matrix for Business Strategy
Reading Time: 2 minutesThe Boston Consulting Group (BCG) matrix is a tool that helps organizations determine the positioning of their products...
Digital Marketing and the AI Revolution
Reading Time: 10 minutesIntroduction to Digital Marketing and the AI Revolution In today’s digital age, businesses must adapt to new marketing...
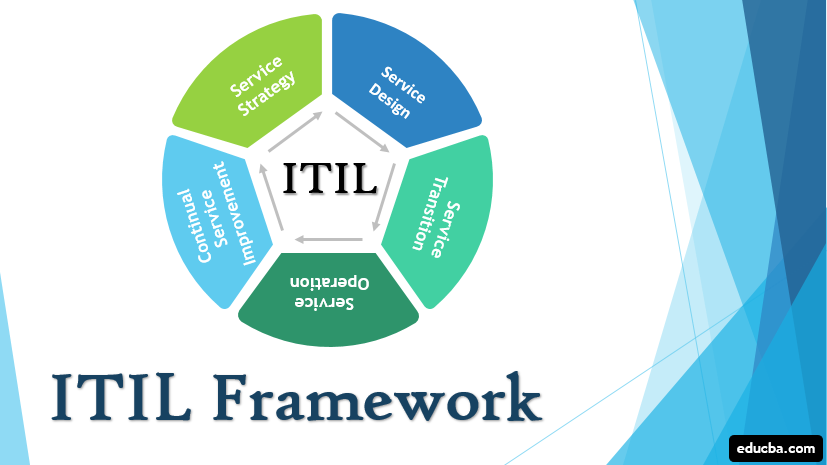
ITIL: A Comprehensive Guide to IT Service Management
Reading Time: 11 minutesIntroduction to ITIL What is ITIL? ITIL stands for Information Technology Infrastructure Library and it is a comprehensive...
Confirmation Bias: Why You Need to Challenge Your Assumptions
Reading Time: 8 minutesIntroduction Confirmation bias is a cognitive bias that affects our decision-making process and influences our perception of reality....
