I. Introduction to SIEM
What is Security Information and Event Management (SIEM)?
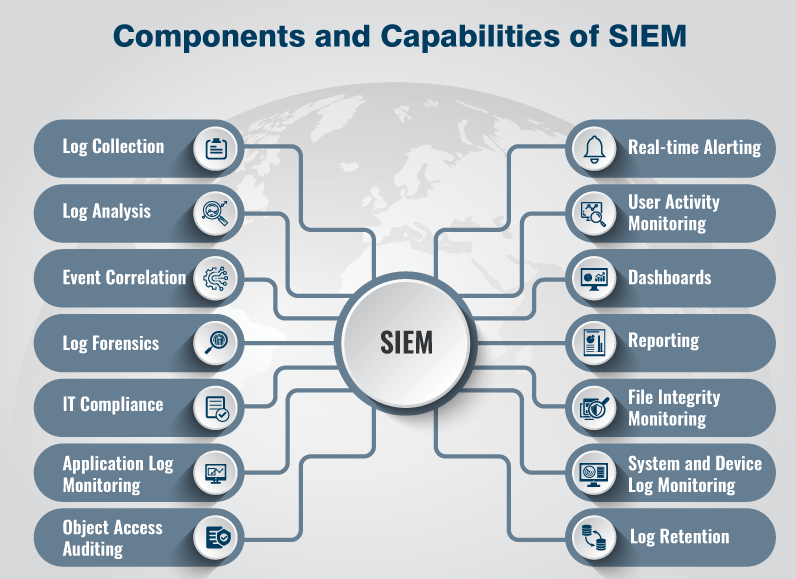
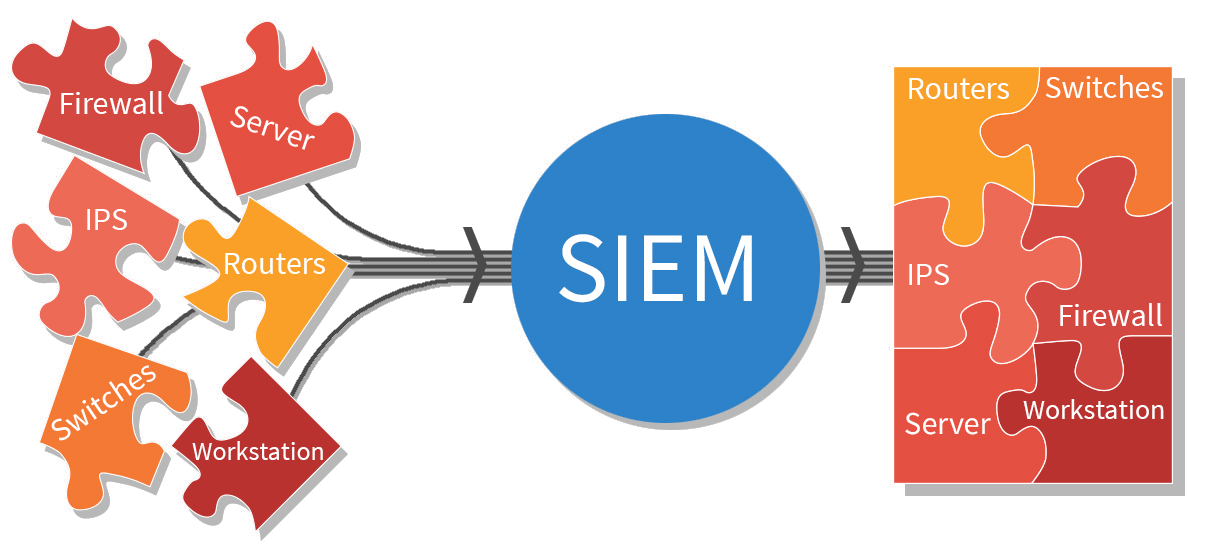
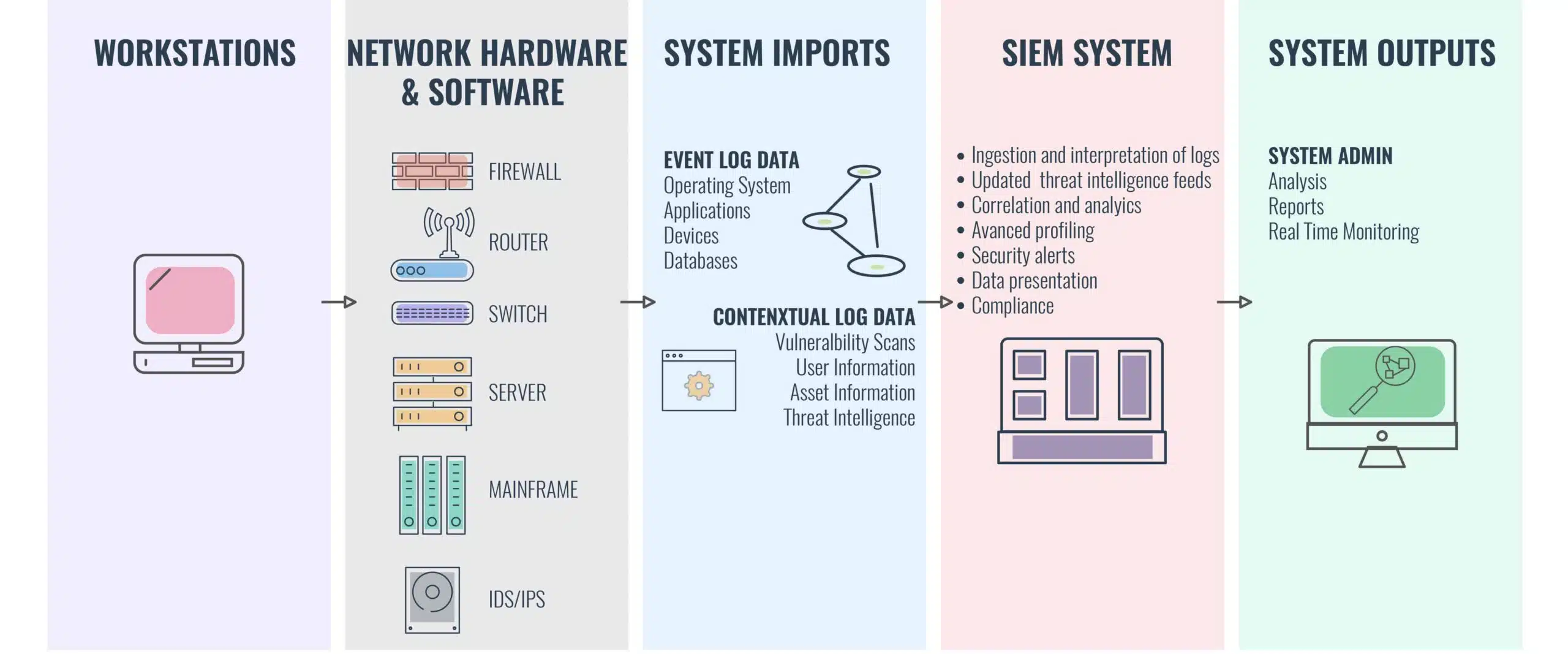
Security Information and Event Management (SIEM) is a technology that allows organizations to collect, analyze, and manage security data from various sources across their network. It provides real-time monitoring, threat detection, and response capabilities to enhance the overall security posture of an organization.
SIEM systems collect and aggregate log data from devices, applications, and network infrastructure to provide a centralized view of the organization’s security events. The collected data is analyzed using correlation rules and machine learning algorithms to identify potential security incidents and threats. SIEM helps organizations detect and respond to security breaches, insider threats, and other malicious activities.
Importance of SIEM in cybersecurity
SIEM plays a crucial role in modern cybersecurity for several reasons:
-
Threat Detection: SIEM helps organizations detect and identify security incidents in real-time by correlating events from various sources. It enables quick response and reduces the impact of cyber-attacks.
-
Log Management: SIEM systems collect and store log data from different devices and applications, allowing organizations to meet compliance and regulatory requirements. It provides a centralized repository for easy access and analysis of security events.
-
Incident Response: SIEM systems provide incident response capabilities, allowing security teams to investigate and mitigate security incidents promptly. It enables forensic analysis, threat hunting, and incident recovery.
-
Compliance and Auditing: SIEM helps organizations demonstrate compliance with industry regulations by providing log data and audit reports. It aids in monitoring and reporting on security controls, user activities, and data breaches.
-
Operational Efficiency: SIEM automates the collection, analysis, and response to security events, improving the efficiency of security operations teams. It reduces manual effort and enables proactive threat hunting.
Overall, SIEM is an essential component of a robust cybersecurity strategy. It provides organizations with the ability to detect, respond to, and mitigate security incidents effectively.
Some popular SIEM products available on the market include:
- IBM Security QRadar: A comprehensive SIEM solution that provides threat detection, incident response, and compliance management capabilities.
- Splunk Enterprise Security: A flexible SIEM platform that offers real-time monitoring, investigation, and automated response for security events.
- ArcSight: An enterprise-grade SIEM solution that provides log management, threat intelligence, and security analytics for detecting and responding to cyber threats.
- LogRhythm: A unified SIEM and SOAR (Security Orchestration, Automation, and Response) platform that combines threat detection, incident response, and compliance management.
- SolarWinds Security Event Manager: A SIEM solution that offers real-time log analysis, threat intelligence, and compliance reporting to enhance security visibility and compliance.
- McAfee Enterprise Security Manager: A scalable SIEM platform that enables real-time threat detection, incident response, and compliance reporting for comprehensive security monitoring.
These SIEM products provide organizations with a range of options to choose from based on their specific requirements and budget.
II. Key Functionality of SIEM
Security Information and Event Management (SIEM) solutions offer a range of critical functionality to help organizations effectively manage and respond to security incidents. Here are some key functionalities of SIEM:
Log Management and Correlation
Log management and correlation are fundamental features of SIEM solutions. They provide the ability to collect, analyze, and store logs from various sources, such as network devices, servers, and applications. SIEM platforms use sophisticated algorithms to correlate these logs and identify patterns and anomalies that could indicate a security incident.
Real-time Monitoring and Alerts
SIEM solutions enable organizations to monitor their IT infrastructure and security events in real-time. They continuously analyze incoming logs and events, highlighting any suspicious or malicious activities. SIEM platforms can generate alerts and notifications to notify security teams about potential threats, allowing for immediate investigation and response.
Incident Response and Forensics
When a security incident occurs, SIEM solutions play a crucial role in incident response and forensics. They provide comprehensive log data that can be used to investigate the root cause of an attack and understand the extent of the damage. SIEM tools also facilitate incident response workflows, helping security teams streamline their processes and take appropriate actions in a timely manner.
Overall, SIEM solutions offer a holistic approach to security management by providing log management and correlation, real-time monitoring and alerts, and incident response and forensics capabilities. By leveraging these functionalities, organizations can enhance their security posture and effectively protect their sensitive data and assets.
Popular SIEM products on the market include:
These SIEM solutions offer a range of features and capabilities to meet the security needs of organizations across various industries. It’s important to evaluate each product’s specific features, scalability, and integration capabilities to find the best fit for your organization’s requirements.
III. Popular SIEM Products on the Market
When it comes to Security Information and Event Management (SIEM) solutions, there are several popular products that have gained recognition in the cybersecurity industry. These products help organizations monitor and manage security events and incidents in real-time. Here are some of the leading SIEM products on the market:
Splunk Enterprise
Splunk Enterprise is a widely used SIEM solution that offers comprehensive log management, real-time threat detection, and incident response capabilities. It enables organizations to collect, analyze, and visualize security data from various sources, allowing for better detection and response to security threats.
IBM QRadar
IBM QRadar is another well-known SIEM solution that provides advanced threat intelligence, event correlation, and security incident management. It offers real-time monitoring of network traffic, system logs, and user activity, helping organizations identify and respond to potential security breaches.
LogRhythm
LogRhythm is a SIEM platform that integrates log management, security analytics, and advanced threat detection. It helps organizations streamline their security operations by providing centralized visibility into events and threats across the network infrastructure.
AlienVault USM
AlienVault USM is a comprehensive SIEM solution that combines threat intelligence, log management, and behavioral monitoring. It offers built-in compliance management and incident response capabilities, making it suitable for organizations with regulatory requirements.
These SIEM products provide organizations with the tools they need to effectively monitor and respond to security threats. Each product has its own unique features and capabilities, so organizations should carefully assess their specific needs and requirements before selecting a SIEM solution.
IV. Features and Capabilities of Splunk Enterprise
Log collection and analysis
Splunk Enterprise is a popular SIEM product that offers advanced log collection and analysis capabilities. It can collect and index logs from various sources, such as servers, network devices, and applications, providing a centralized view of all your log data. Splunk’s powerful search and analysis capabilities allow you to easily search and correlate logs to identify security events and potential threats.
Threat intelligence integration
Splunk Enterprise also integrates with various threat intelligence sources, including open-source feeds and commercial threat intelligence platforms. This enables you to enrich your log data with contextual information about known threats, IP addresses, domains, and more. By incorporating threat intelligence into your security monitoring, you can better detect and respond to malicious activities.
Machine learning and analytics
Splunk Enterprise leverages machine learning and advanced analytics to detect anomalies and patterns in your log data. It uses algorithms to identify unusual behaviors, such as repeated failed login attempts, abnormal network traffic, or suspicious user activities. By automatically analyzing large volumes of log data, Splunk can help prioritize security incidents and reduce response times.
With its comprehensive log collection and analysis capabilities, seamless threat intelligence integration, and advanced machine learning and analytics, Splunk Enterprise is a powerful SIEM solution for organizations looking to enhance their security posture.
Other popular SIEM products on the market include:
- ArcSight: Offers real-time correlation and analysis of security events, as well as compliance monitoring and reporting.
- LogRhythm: Provides real-time visibility into network and endpoint activity, as well as advanced correlation and threat detection capabilities.
- IBM QRadar: Offers advanced threat detection and analytics, as well as integration with IBM’s extensive security ecosystem.
- AlienVault USM: Combines SIEM, intrusion detection, and vulnerability assessment capabilities in a unified platform.
- Securonix: Utilizes behavior analytics and machine learning to detect insider threats and advanced attacks.
These are just a few examples of the diverse SIEM products available on the market, each with its unique features and capabilities. It’s important to evaluate your organization’s specific security requirements and budget before selecting a SIEM solution.
IX. Benefits and Challenges of Implementing SIEM
Implementing a Security Information and Event Management (SIEM) solution can bring several benefits to an organization’s cybersecurity infrastructure. However, it also comes with its own set of challenges. Here are some of the main benefits and challenges of implementing SIEM:
Improved threat detection and response
- SIEM solutions collect and analyze data from various sources, such as network devices, servers, and applications, providing real-time visibility into potential security incidents.
- By correlating events and applying advanced analytics, SIEM tools can detect patterns and anomalies that may indicate malicious activity.
- Automated alerts and notifications enable organizations to respond quickly and mitigate threats, preventing potential data breaches.
Regulatory compliance and reporting
- SIEM solutions help organizations meet regulatory requirements by providing centralized event log management and reporting capabilities.
- By automating compliance processes, SIEM tools save time and effort in maintaining audit logs and generating required reports.
- Compliance frameworks, such as PCI DSS and HIPAA, often require log monitoring and analysis, making SIEM an essential component for organizations operating in regulated industries.
Integration and deployment complexities
- Implementing a SIEM solution involves the integration of various data sources, which can be challenging due to the diversity of systems and applications in an organization’s infrastructure.
- SIEM deployment requires careful planning and coordination with IT teams to ensure compatibility and minimize disruptions.
- Configuring and fine-tuning a SIEM solution to meet the specific needs of an organization requires a deep understanding of both the technology and the organization’s security objectives.
Despite the challenges, implementing a SIEM solution can significantly enhance an organization’s ability to detect and respond to security threats effectively. It provides the necessary visibility into the environment, supports compliance requirements, and strengthens overall cybersecurity posture.
X. Case Studies: Real-world Examples of Successful SIEM Implementations
Company A: Detecting and mitigating a sophisticated cyber attack
Company A, a global financial institution, faced a significant cyber attack that threatened the security of their sensitive customer data. With the help of a Security Information and Event Management (SIEM) system, they were able to quickly detect and mitigate the attack, minimizing the impact on their operations and reputation. Here’s how their SIEM implementation played a crucial role:
-
Real-time monitoring: The SIEM system continuously monitored the network for any suspicious activity, alerting the security team to potential threats in real-time.
-
Advanced threat detection: The SIEM system used machine learning algorithms to analyze log data from various sources, including firewalls, servers, and intrusion detection systems. This allowed the system to detect patterns and anomalies indicative of a cyber attack.
-
Automated response: Once the system detected the attack, it automatically triggered pre-defined response mechanisms, such as blocking the attacker’s IP address, isolating compromised systems, or initiating incident response procedures.
-
Forensic analysis: The SIEM system provided detailed logs and event data, enabling the security team to conduct thorough forensic analysis after the attack. This analysis helped identify the attack’s origin and modus operandi, assisting in the implementation of additional security measures.
Company B: Proactively identifying insider threats
Company B, a technology firm, implemented a SIEM system to proactively identify and monitor for insider threats. They recognized that the risk of internal data breaches posed a significant concern. Here’s how their SIEM implementation helped mitigate this risk:
-
User behavior analytics: The SIEM system analyzed user activity logs to establish baseline behavior patterns of employees and contractors. It then monitored deviations from these patterns to detect potential insider threats, such as unauthorized access or abnormal data transfers.
-
Contextual analysis: By correlating various data sources, including HR records and network logs, the SIEM system contextualized user behavior, identifying suspicious patterns that might indicate malicious intent.
-
Policy enforcement: The SIEM system enforced security policies, such as access controls and privileged user monitoring, ensuring that employees followed defined security protocols. Violations were flagged and investigated promptly.
-
Data leakage prevention: The SIEM system helped prevent data leakage by monitoring outbound traffic and tracking sensitive data transfers or unauthorized sharing of confidential information.
These case studies highlight the effectiveness of SIEM systems in enhancing cybersecurity and mitigating risks for organizations across various industries.
For more information on SIEM and the popular SIEM products on the market, please refer to this Wikipedia article.

XI. Conclusion
The evolving role of SIEM in cybersecurity
In conclusion, SIEM (Security Information and Event Management) plays a crucial role in modern cybersecurity. It helps organizations monitor and analyze security events and incidents in real-time, allowing them to detect and respond to threats more effectively. Through the use of advanced log management, correlation, and analytics tools, SIEM solutions provide valuable insights into potential security breaches, helping organizations stay one step ahead of cybercriminals.
Choosing the right SIEM solution for your organization
When selecting a SIEM solution for your organization, it’s important to consider the following factors:
1. Scalability: Ensure that the SIEM solution can scale and accommodate the growing needs of your organization.
2. Compatibility: Make sure the SIEM solution can integrate with your existing security infrastructure and tools.
3. Flexibility: Look for a SIEM solution that can be tailored to your organization’s specific requirements and compliance needs.
4. User-friendly interface: Choose a SIEM solution that is intuitive and easy to navigate, enabling efficient management and analysis of security events.
Key considerations when implementing SIEM
When implementing SIEM in your organization, keep the following considerations in mind:
1. Determine your goals: Clearly define your security objectives and align them with the capabilities of the SIEM solution.
2. Plan for integration: Ensure that the SIEM solution can integrate with your existing security tools and systems to provide a comprehensive view of your organization’s security posture.
3. Define your log sources: Identify the critical log sources to be monitored, including network devices, servers, applications, and databases.
4. Establish proper log management practices: Implement log retention policies and ensure that logs are properly collected, stored, and protected.
By carefully considering these factors and implementing a robust SIEM solution, organizations can strengthen their cyber defenses and better protect their valuable assets from increasingly sophisticated threats.