.jpg?width=1000&name=Palo%20Alto%20Cortex%20EDR(USE).jpg)
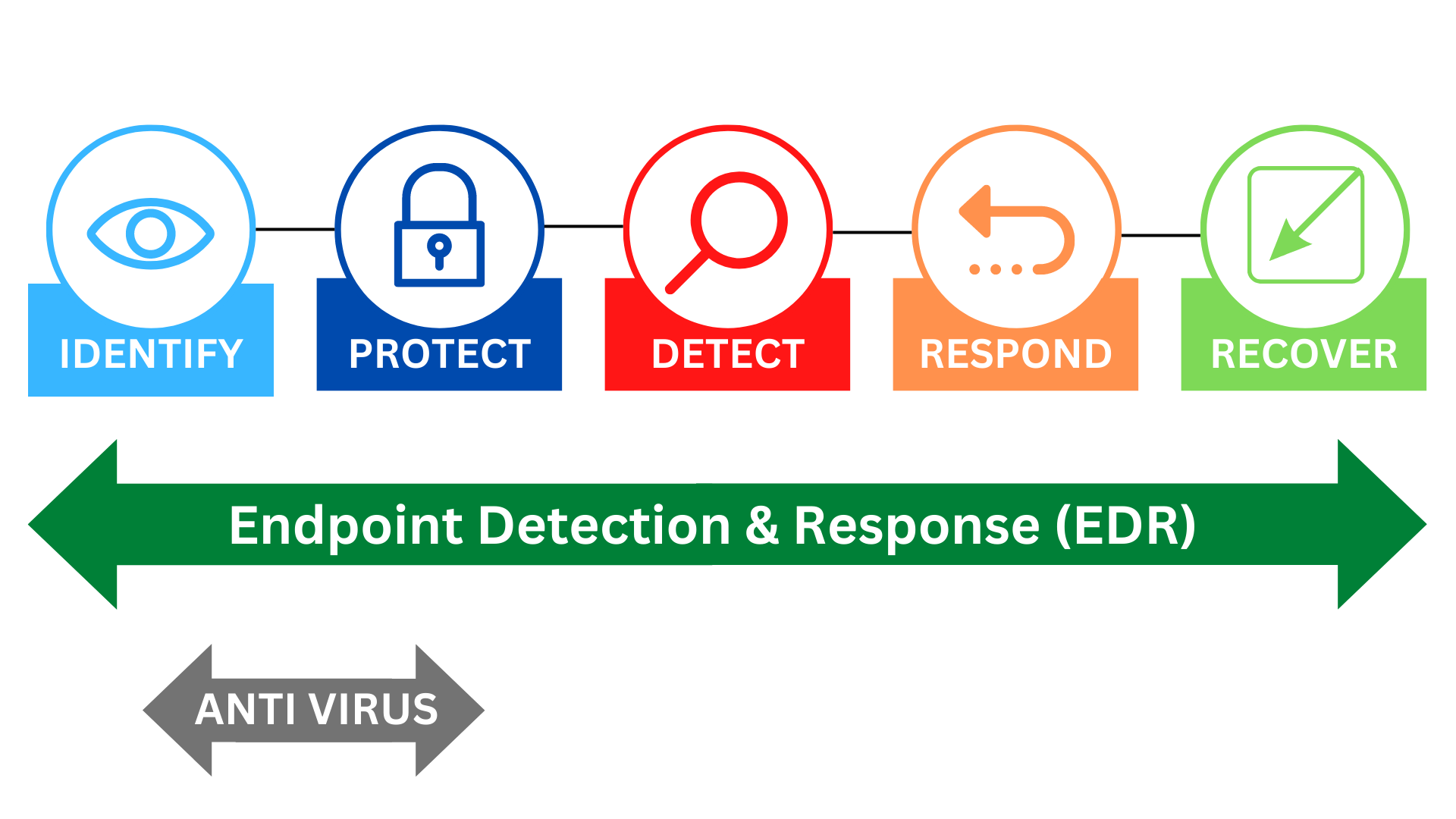
Overview of EDR Landscape
In today’s digital world, where cyber threats seem to evolve faster than our ability to combat them, understanding the Endpoint Detection and Response (EDR) landscape has never been more critical. EDR solutions function as the sentinels of cybersecurity, scouting for malicious activities within organization endpoints—desktops, laptops, or mobile devices. These systems detect potential security breaches and respond to incidents in real-time, often incorporating features like automated remediation to mitigate damage. For example, imagine a company’s employee opening a seemingly innocent email. What might seem like a minor error can lead to a significant breach if an attacker exploits that vulnerability. Here is where EDR comes into play, acting swiftly to neutralize any threats before they escalate. The EDR landscape comprises various vendors and technologies that offer unique capabilities, ranging from traditional antivirus to cutting-edge behavioral analysis. It is a diverse field that continually adapts to the landscape of threats.
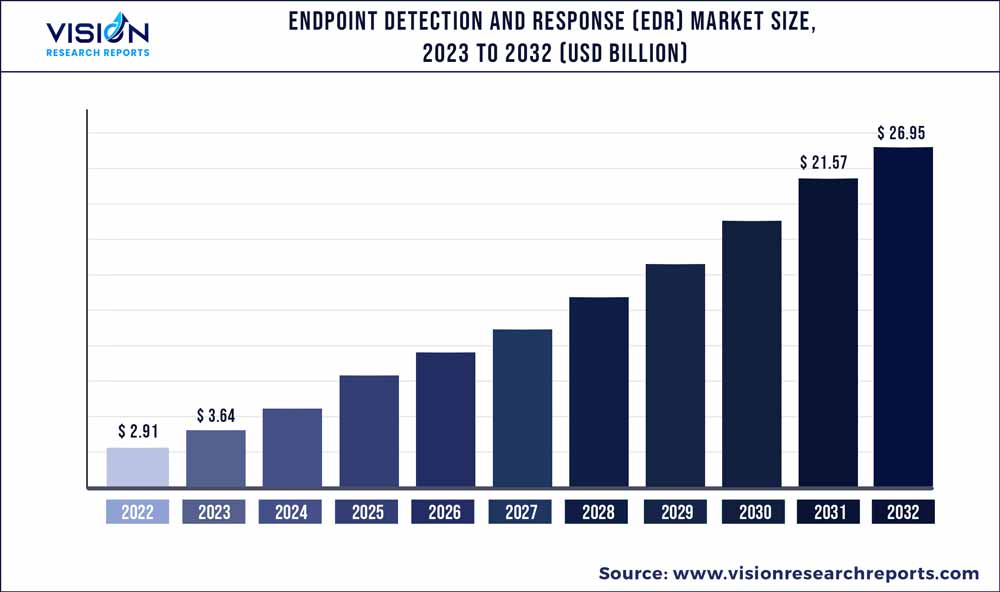
Importance of Understanding Market Trends
For organizations using EDR solutions or considering their adoption, staying updated on market trends is paramount. Here are some reasons why understanding these trends should be a priority:
- Informed Decision-Making: Businesses can choose EDR solutions aligning with their unique needs and risk profiles by knowing trending trends.
- Future-Proofing Security Posture: With rapid advancements in cybersecurity technology, understanding trends helps organizations anticipate future challenges and secure their systems accordingly.
- Competitive Edge: Companies aware of the latest threats and mitigation strategies are better positioned in their respective markets.
A personal encounter illustrates this point well: a friend’s startup recently fell victim to a ransomware attack due to inadequate endpoint protection. Had they invested time in understanding market trends and the offerings of various EDR providers, they might have been able to thwart the attack before it began. In a realm where digital assets are invaluable, understanding the EDR landscape and market trends is beneficial and essential for safeguarding an organization’s vitality and integrity.
Market Trends in EDR
Rise of Endpoint Security
As the digital landscape continues to evolve, the rise of endpoint security stands out as one of the most significant trends in the EDR market. With the increasing number of devices connected to corporate networks, each endpoint is a potential entry point for cybercriminals. These past few years have seen a remarkable shift in focus towards robust endpoint security solutions designed to protect the systems and the invaluable data they house. Consider this: a mid-sized e-commerce business recently faced a surge in cyber-attacks targeting customer data. By prioritizing endpoint security through adopting advanced EDR solutions, they successfully thwarted multiple attempts to breach their network. This shift highlights how essential endpoint protection has become in ensuring operational continuity. Key factors contributing to the rise of endpoint security include:
- Remote Work: With the shift to remote and hybrid work models, organizations have realized that endpoints are scattered across various locations, making them more vulnerable.
- Cloud Adoption: As more businesses move to cloud infrastructures, the need for endpoint security solutions that can effectively monitor and manage these environments has become vital.
- Regulatory Compliance: Increasing regulations in various industries mandate stringent data protection measures, thus driving businesses to invest in EDR capabilities.
Impact of Advanced Threats
Advanced threats are constantly challenging, affecting how organizations approach their cybersecurity strategies. Ransomware, sophisticated phishing attacks, and zero-day exploits are commonplace in the cyber threat landscape. The more advanced these threats become, the more imperative businesses are to implement comprehensive EDR solutions that quickly detect and respond to these attacks. For instance, a financial institution faced a terrifying scenario when attackers deployed a zero-day exploit within their system. Fortunately, their EDR solution utilized machine learning algorithms that flagged anomalous behavior, allowing the security team to respond swiftly and avert potential financial loss. The impact of advanced threats underscores the necessity for organizations to:
- Adopt Proactive Measures: Organizations should not just react to threats but anticipate and adapt to new attack vectors.
- Invest in Threat Intelligence: Utilizing threat intelligence feeds can enhance an EDR system’s ability to recognize and respond to advanced threats effectively.
- Conduct Regular Vulnerability Assessments: Frequent assessments help identify potential weaknesses before they can be exploited by cybercriminals.
In sum, the rise of endpoint security and the pervasive influence of advanced threats highlight the dynamic nature of the EDR market. As organizations navigate this evolving landscape, awareness and adaptation are crucial to maintaining a strong cybersecurity posture.
.jpg?width=1000&name=Cytomic_EDR(USE).jpg)
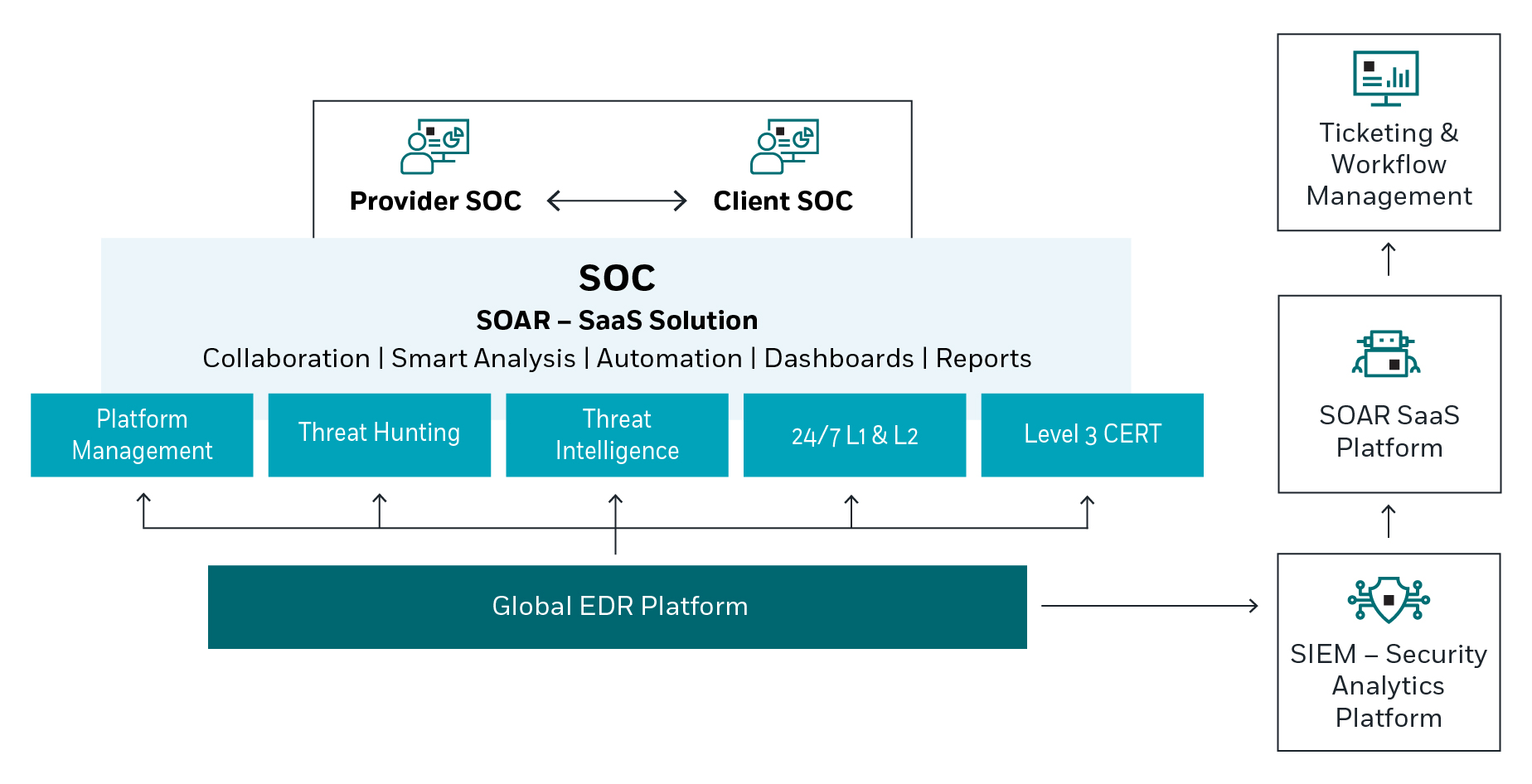
Leading Vendors in EDR
Overview of Top EDR Providers
As organizations seek to fortify their defenses against increasingly sophisticated cyber threats, the demand for robust Endpoint Detection and Response (EDR) solutions has led to the emergence of leading vendors in this space. Recognizing the effective EDR providers can be a game-changer for a company’s cybersecurity strategy. The current market features various prominent vendors, each offering unique strengths:
- CrowdStrike: Known for its cloud-native architecture, CrowdStrike Falcon is praised for its speed and efficient threat intelligence capabilities.
- Microsoft: With its Defender for Endpoint, Microsoft integrates seamlessly into existing Windows ecosystems, leveraging advanced analytics and automation to detect threats.
- SentinelOne: This provider merges EDR with AI-driven capabilities, enabling automated threat remediation without manual intervention, which can significantly reduce response times.
- Sophos: Renowned for its user-friendly interface, Sophos Intercept X offers preemptive security measures and adequate endpoint protection at a competitive price.
These vendors have adapted their offerings to address contemporary security challenges, ensuring businesses can receive tailored solutions.
Key Features of Leading EDR Solutions
When evaluating EDR solutions, organizations must consider key features that differentiate the leading products from the rest. Here are some standout functionalities that should be at the forefront of any EDR consideration:
- Real-time Threat Detection: Effective EDR tools provide continuous monitoring, instantly identifying and responding to potential threats as they appear.
- Automated Response Capabilities: Many top solutions feature automation that detects threats and takes immediate actions to contain them, saving valuable time during an incident.
- Threat Hunting Tools: Leading EDR platforms offer comprehensive threat-hunting features, enabling security teams to proactively search for hidden threats and vulnerabilities within their networks.
- Detailed Forensics and Reporting: After an incident, detailed analysis helps organizations understand the nature of the breach, making it easier to strengthen defences against future attacks.
A personal encounter highlights this: a colleague’s organization recently implemented an EDR solution with enhanced automated response capabilities. The swift action taken by the technology successfully neutralized an attack before it could escalate, demonstrating the importance of having the right features in place. In summary, as organizations navigate the EDR landscape, partnering with leading vendors with comprehensive features can significantly bolster their overall security posture.
.jpg?width=1000&name=Malwarebytes_EDR(USE).jpg)
Cutting-Edge Technology in EDR
Artificial Intelligence and Machine Learning
In the ever-evolving world of cybersecurity, the integration of Artificial Intelligence (AI) and Machine Learning (ML) into Endpoint Detection and Response (EDR) systems has proven to be a game-changer. These technologies empower EDR solutions to process vast amounts of data at lightning speed and identify anomalies that a human analyst might overlook. For instance, an organization faced a significant challenge when a previously undetected malware strain infiltrated their network. Traditional methods of detection fell short, but the implementation of AI-driven EDR tools allowed them to analyze patterns and recognize the unusual behavior of the malware instantly. Not only did it activate alerts, but it also initiated immediate containment measures. Critical advantages of AI and ML in EDR include:
- Predictive Capabilities: By learning from historical datasets, AI models can predict potential threats before they manifest, allowing for preemptive actions.
- Reduced False Positives: Advanced algorithms improve accuracy, minimizing the likelihood of alerts that don’t represent real threats, thus freeing valuable analyst time.
- Continuous Learning: As new threats emerge, AI-driven systems adapt by continuously improving their detection capabilities without manual reprogramming.
Behavioral Analysis and Threat Detection
Complementing AI and ML, behavioral analysis has become a cornerstone of effective threat detection in EDR. Organizations can identify threats that may otherwise remain hidden by focusing on the actions of users and devices rather than relying solely on known malicious signatures. Consider a scenario where an employee’s account is compromised. Instead of simply alerting on known malware signatures, behavioral analysis observes unusual login times, irregular file access, and atypical data downloads, providing a more comprehensive view of the situation. Critical features of behavioral analysis in EDR systems include:
- Anomaly Detection: Identifying deviations from established user or system behaviors helps recognize potential security breaches in real time.
- User and Entity Behavior Analytics (UEBA): This approach adds an extra layer of analysis, considering the context of actions to differentiate between legitimate users and malicious actors.
- Dynamic Response: Organizations can tailor their responses based on user behavior; for instance, temporarily restricting access if unusual activity is detected.
As organizations embrace cutting-edge technologies like AI, ML, and behavioral analysis in their EDR strategies, they arm themselves with sophisticated tools that detect and effectively respond to modern cyber threats. The proactive capabilities offered by these technologies are essential for maintaining a robust security posture in today’s digital environment.
EDR Adoption Challenges
Integration with Existing Security Infrastructure
While Endpoint Detection and Response (EDR) solutions have numerous benefits, organizations often face significant challenges during the adoption phase—particularly when integrating these systems into their existing security infrastructure. Many organizations have developed a patchwork of security tools over time, making incorporating a new EDR solution a daunting task. For instance, a financial services company recently attempted to roll out an EDR tool but found that its legacy antivirus systems and firewalls were incompatible. This led to prolonged integration delays and ultimately hindered their security posture during a critical period. Key integration challenges include:
- Compatibility Issues: Older systems may not easily communicate with newer EDR tools, leading to gaps in security coverage.
- Increased Complexity: Implementing EDR can add layers of complexity to an existing security setup, making management and monitoring more challenging for security teams.
- Resource Strain: Organizations must allocate time and personnel to effectively implement and integrate the EDR system—resources that may already be stretched thin.
To ease this transition, organizations can:
- Conduct thorough compatibility assessments before selection.
- Prioritize EDR solutions that offer robust APIs and integration capabilities.
- Engage with vendors who provide support during the integration phase.
Skills Gap and Training Requirements
Another considerable hurdle in EDR adoption is the skills gap prevalent in many organizations. Even with the latest technologies, companies cannot effectively leverage these tools due to a lack of trained personnel. Many security teams are overwhelmed and faced with the challenge of upskilling to make the most of EDR capabilities. For instance, when a colleague’s organization implemented a sophisticated EDR solution, they quickly realized that their team lacked the necessary skills to perform nuanced threat analysis, leading to underutilising the tool’s potential. Some factors contributing to the skills gap include:
- Rapid Technology Evolution: Cybersecurity tools evolve quickly, and teams can struggle to keep up without continuous learning.
- Limited Training Resources: Many organizations lack formal training programs focused on advanced EDR functionalities.
- High Demand for Cybersecurity Professionals: The cybersecurity landscape is highly competitive, making it challenging to recruit skilled individuals.
To bridge the skills gap, organizations can:
- Invest in continuous education and training programs tailored to their adopted EDR tools.
- Foster a culture of knowledge sharing among team members to enhance collective expertise.
- Consider partnerships with specialized training providers or platforms to ensure staff receive quality education on the latest EDR technologies.
In conclusion, while adopting EDR solutions is essential for a robust security posture, organizations must navigate integration challenges and address skills gaps to maximize the effectiveness of their cybersecurity strategies. By proactively addressing these hurdles, businesses can empower their security teams and create a more resilient security framework.