Introduction
In the vast and interconnected world of the internet, computer protocols serve as the backbone that enables communication and data transfer between devices. Without these protocols, the internet as we know it would not exist. Understanding the importance of computer protocols is crucial for anyone seeking to comprehend the inner workings of this digital realm.
Why computer protocols are important in the internet
Computer protocols play a vital role in ensuring smooth and efficient communication across the internet. Here are some key reasons why these protocols matter:
- Standardization: Computer protocols establish a set of rules and standards that govern how devices communicate with each other. This standardization ensures compatibility and interoperability between different hardware and software systems, allowing them to seamlessly exchange information.
- Reliability: Protocols such as TCP/IP (Transmission Control Protocol/Internet Protocol) are designed to ensure reliable data transmission over the internet. They provide error detection, correction, and retransmission mechanisms, guaranteeing that data arrives intact and in the correct order.
- Security: Protocols like SSL/TLS (Secure Sockets Layer/Transport Layer Security) are essential for securing online transactions and protecting sensitive information. These protocols encrypt data to prevent unauthorized access, ensuring the confidentiality and integrity of data transmitted over the internet.
- Scalability: Computer protocols enable the internet to handle massive amounts of traffic by efficiently routing data packets across networks. Protocols like BGP (Border Gateway Protocol) help determine the most efficient paths for data transmission, optimizing network performance.
- Interconnectivity: By adhering to common protocols, devices from different manufacturers and operating systems can seamlessly connect and communicate with each other. This interoperability enables a wide range of applications and services to function together harmoniously on the internet.
In summary, computer protocols are the unsung heroes that make the internet work. They provide the necessary rules, reliability, security, scalability, and interconnectivity that enable seamless communication and data transfer across the digital landscape. Understanding these protocols is crucial for anyone involved in the world of technology and the internet.
TCP/IP Protocol Suite
Overview of the TCP/IP protocol suite
The TCP/IP protocol suite is the foundation of the internet, serving as the backbone for data communication between devices worldwide. TCP/IP stands for Transmission Control Protocol/Internet Protocol. It is a set of rules and protocols that allow devices to connect and communicate.
Key protocols in TCP/IP: IP, TCP, UDP
The TCP/IP protocol suite comprises several key protocols, including IP (Internet Protocol), TCP (Transmission Control Protocol), and UDP (User Datagram Protocol).
- IP is responsible for addressing and routing packets across the internet. It ensures that data packets are delivered to the correct destination by assigning unique IP addresses to devices.
- TCP provides reliable, connection-oriented communication between devices. It breaks data into smaller packets, ensures their proper sequencing, and reassembles them at the destination.
- UDP, on the other hand, offers connectionless communication. It is commonly used for real-time applications such as video streaming and online gaming, where speed is prioritized over reliability.
Functions and features of TCP/IP
TCP/IP offers several functions and features that make it essential for internet communication:
- Addressing: IP addresses uniquely identify devices on the internet, allowing for accurate packet routing.
- Reliability: TCP ensures that data is delivered without errors or loss through its error detection and correction mechanisms.
- Multiplexing: TCP/IP allows multiple applications to run simultaneously on a device by assigning unique port numbers to each application.
- Fragmentation: TCP/IP breaks large data packets into smaller fragments for efficient transmission across networks with varying maximum packet sizes.
- Interoperability: TCP/IP is a universal protocol suite that enables different types of devices and operating systems to communicate seamlessly.
The TCP/IP protocol suite is important for the internet to work. It gives rules and protocols for devices to connect, communicate, and share data.
HTTP Protocol
Introduction to HTTP protocol
The Hypertext Transfer Protocol (HTTP) is the foundation of communication on the World Wide Web. The protocol defines how data is transmitted between a client and a server. HTTP allows for the retrieval and display of web pages and the exchange of other resources such as images, videos, and files.
HTTP request and response format
When a client, such as a web browser, wants to access a web page, it sends an HTTP request to the server hosting that page. The request includes information such as the desired resource (e.g., a specific webpage), any additional parameters, and the HTTP version being used.
The server then processes the request and sends back an HTTP response. The response has the status code, headers with metadata, and the content of the requested resource.
Role of HTTP in Web Browsing
HTTP plays a crucial role in web browsing by enabling web content’s seamless retrieval and display. When you type a URL into your browser’s address bar or click on a link, your browser sends an HTTP request to the server hosting that webpage. The server responds with an HTTP response containing the HTML, CSS, JavaScript, and other resources needed to render and display the webpage.
HTTP also facilitates interactions between web applications and servers. For example, when you submit a form on a website or make an online purchase, your browser sends an HTTP request to the server handling those actions.
In conclusion, understanding the HTTP protocol is essential for anyone involved in web development or digital marketing. It forms the backbone of communication on the internet and enables seamless browsing experiences for users around the world.
DNS Protocol
What is DNS and its purpose
The Domain Name System (DNS) is a crucial protocol that plays a fundamental role in the functioning of the internet. DNS translates domain names like www.example.com into IP addresses that computers use to communicate. In simpler terms, DNS acts as the internet’s phonebook, enabling users to access websites by typing in familiar domain names instead of complex IP addresses.
Domain name resolution process
The DNS resolution process begins when a user enters a domain name into their web browser. It involves multiple steps, including querying DNS servers to find the IP address associated with the requested domain name. This process ensures that users are directed to the correct website and allows for efficient internet communication.
Importance of DNS in internet communication
The DNS protocol is essential for reliable and efficient internet communication for several reasons. Firstly, it simplifies the user experience by allowing them to access websites using easy-to-remember domain names. Secondly, it enables load balancing and fault tolerance by distributing network traffic across multiple servers. Additionally, DNS caching improves performance by storing frequently accessed domain name information locally.
In conclusion, the DNS protocol is a critical component of the internet infrastructure. Its ability to translate domain names into IP addresses ensures seamless communication between devices and allows users to navigate the web effortlessly. Understanding how DNS works and its importance in internet communication is vital for anyone involved in managing or using online services.
FTP Protocol
Understanding FTP (File Transfer Protocol)
FTP, or File Transfer Protocol, is a standard network protocol used for transferring files between a client and a server on a computer network. It is one of the oldest protocols still in use today and plays a crucial role in the transfer of files over the internet.
FTP allows users to upload, download, and manage files on remote servers. It provides a simple and efficient way to transfer large files or multiple files at once. With FTP, users can authenticate themselves using a username and password, ensuring secure access to their files.
Secure FTP (SFTP) and FTPS
To address security concerns associated with FTP, two secure alternatives have been developed: SFTP (SSH File Transfer Protocol) and FTPS (FTP over SSL/TLS).
SFTP uses the Secure Shell (SSH) protocol to encrypt data during file transfers, providing a high level of security. It is widely supported and offers features like file compression and remote file management.
FTPS, on the other hand, adds an extra layer of security by using SSL/TLS encryption. This protocol ensures that data is protected from unauthorized access during transmission.
Both SFTP and FTPS provide secure alternatives to traditional FTP, making them suitable for businesses that handle sensitive data or require enhanced security measures.
In conclusion, understanding computer protocols like FTP is essential for anyone working with file transfers over the internet. Whether you choose FTP, SFTP, or FTPS depends on your specific needs for security and functionality. By utilizing these protocols effectively, you can ensure efficient and secure file transfers within your network.
Source: media.geeksforgeeks.org
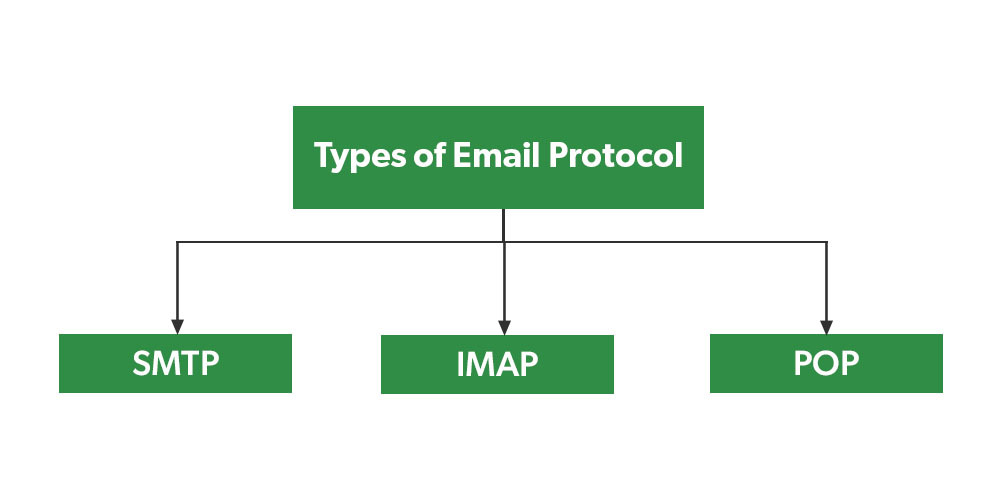
SMTP and POP3 Protocols
How SMTP and POP3 enable email communication
In the digital age, email has become an essential means of communication for individuals and businesses alike. But have you ever wondered how emails are sent and received? Enter SMTP and POP3 protocols, the backbone of email communication.
SMTP, or Simple Mail Transfer Protocol, is responsible for sending emails. When you hit that “send” button, SMTP takes over and ensures that your message is delivered to the recipient’s email server. It works by establishing a connection between your email client and the server, verifying the recipient’s address, and transmitting the email across the internet.
On the other end, POP3, or Post Office Protocol version 3, handles the receiving of emails. When you check your inbox, POP3 retrieves your emails from the server and delivers them to your email client. It allows you to download and store messages locally on your device, giving you offline access to your emails.
SMTP and POP3 form a seamless system that enables efficient email communication. They work hand in hand to ensure that messages are sent and received reliably across different devices and platforms.
It’s worth noting that there are other protocols involved in email communication, such as IMAP (Internet Message Access Protocol), which offers more advanced features like synchronizing folders across multiple devices. However, SMTP and POP3 remain fundamental components of the email infrastructure.
Next time you send or receive an email, take a moment to appreciate the behind-the-scenes work of SMTP and POP3 protocols. They play a crucial role in keeping our digital conversations flowing smoothly, connecting people around the world with just a few clicks.
Source: info-savvy.com
DHCP Protocol
DHCP (Dynamic Host Configuration Protocol)
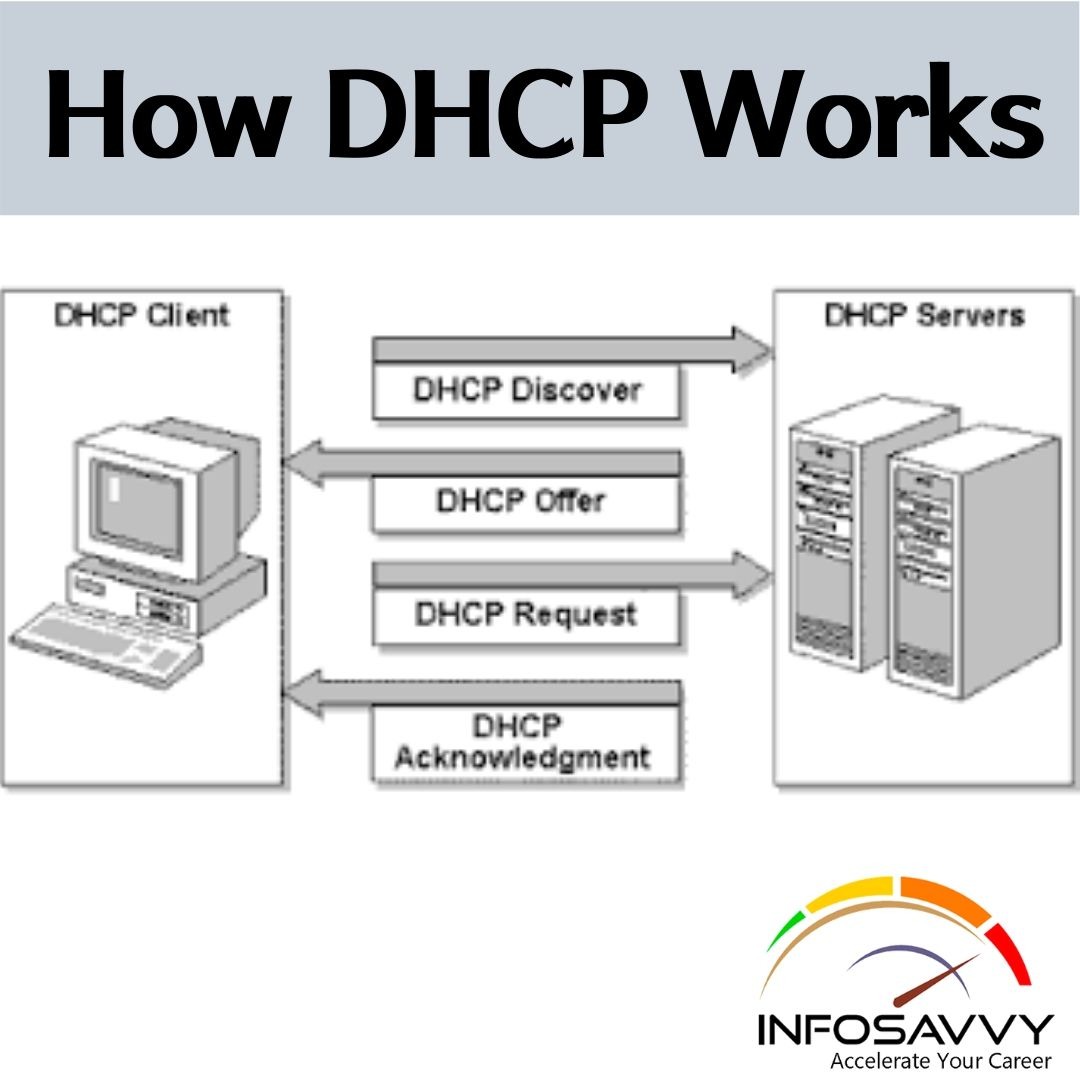
The DHCP protocol plays a crucial role in the functioning of computer networks and the internet. It is responsible for automatically assigning IP addresses and configuring network settings for devices connected to a network. This protocol simplifies network management and ensures efficient communication between devices.
Allocation of IP addresses and network configuration
DHCP eliminates the need for manual IP address assignment, which can be time-consuming and prone to errors. With DHCP, devices can obtain an IP address dynamically from a central server, ensuring that each device on the network has a unique identifier. DHCP configures network settings like subnet mask, default gateway, and DNS server addresses, helping devices connect and communicate.
Benefits of DHCP for network management
The use of DHCP offers several benefits for network management:
- Efficiency: DHCP automates the process of assigning IP addresses, saving time and effort for network administrators. It also allows for quick reconfiguration of IP addresses when devices are added or removed from the network.
- Centralized Control: By using a central DHCP server, administrators can easily manage and monitor IP address allocation and network configurations. This centralized control simplifies troubleshooting and ensures consistency across the network.
- Scalability: DHCP is scalable, making it suitable for networks of all sizes. Whether it’s a small office or a large enterprise, DHCP can handle the dynamic allocation of IP addresses efficiently.
In conclusion, the DHCP protocol is a vital component of computer networks as it automates the allocation of IP addresses and simplifies network configuration. Its benefits include increased efficiency, centralized control, and scalability, making it an essential tool for effective network management.
ICMP Protocol
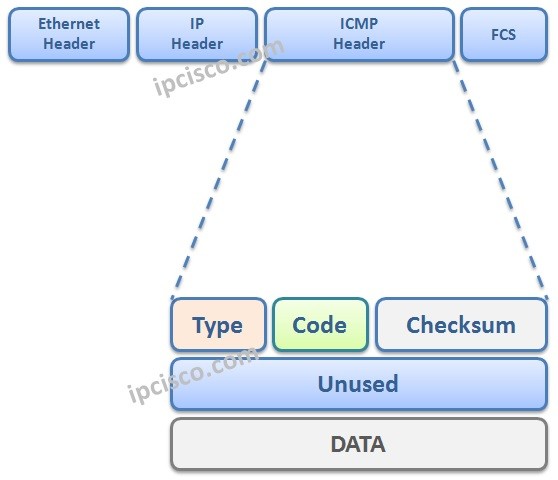
ICMP (Internet Control Message Protocol)
The ICMP protocol is an integral part of the internet’s infrastructure. It is a network layer protocol that enables communication between network devices, providing error reporting, diagnostics, and management functionalities. ICMP messages are typically encapsulated within IP packets and are used to exchange control information between devices.
Role of ICMP in network troubleshooting
ICMP plays a crucial role in network troubleshooting by providing valuable information about network connectivity and identifying potential issues. When a network problem occurs, ICMP messages are generated and sent back to the source device, allowing it to determine the cause of the problem.
Some common uses of ICMP in network troubleshooting include:
- Ping: The ping utility uses ICMP Echo Request and Echo Reply messages to test the reachability and round-trip time of a target device or IP address. It helps identify if a device is online and responsive.
- Traceroute: Traceroute utilizes ICMP Time Exceeded messages to determine the path taken by packets from the source device to a destination. It helps identify network delays or routing issues along the path.
Ping and traceroute utilities
Ping and traceroute are powerful command-line utilities that leverage ICMP to diagnose network connectivity problems. Ping sends ICMP Echo Request messages to a target device and waits for an Echo Reply, measuring the round-trip time. Traceroute sends a series of ICMP Time Exceeded messages with incrementing TTL values to trace the path taken by packets.
By utilizing these utilities, network administrators can identify connectivity issues, measure latency, and pinpoint potential bottlenecks or misconfigurations within their network infrastructure.
In conclusion, the ICMP protocol plays a vital role in network troubleshooting by providing essential tools like ping and traceroute. These utilities help diagnose connectivity problems, measure network performance, and ensure the smooth functioning of the internet.
Conclusion
In conclusion, computer protocols are the backbone of the internet, playing a crucial role in its functioning. They enable communication between devices and ensure that data is transmitted efficiently and securely. Without protocols, the internet as we know it would not exist.
Importance of computer protocols in the functioning of the internet
Computer protocols are essential for the smooth operation of the internet. Here are some key reasons why they matter:
- Standardization: Protocols provide a set of rules and standards that allow different devices and networks to communicate effectively. They ensure compatibility and interoperability across various platforms and technologies.
- Data Transmission: Protocols facilitate the transmission of data packets over networks, ensuring that information reaches its intended destination accurately and efficiently. They handle tasks such as error detection, data segmentation, and reassembly.
- Security: Protocols like SSL/TLS (Secure Sockets Layer/Transport Layer Security) play a vital role in securing online transactions and protecting sensitive information. They encrypt data to prevent unauthorized access and ensure privacy.
- Routing: Internet protocols, such as IP (Internet Protocol), enable routing data packets across multiple networks. They determine the best path for data transmission, ensuring efficient delivery.
- Reliability: Protocols like TCP (Transmission Control Protocol) provide reliable communication by establishing connections, managing data flow, and ensuring error-free delivery.
Overall, computer protocols are fundamental to the functioning of the internet. They enable seamless communication, secure transactions, efficient data transmission, and reliable network operations. Understanding and implementing these protocols is crucial for businesses, organizations, and individuals to maximize internet’s vast potential.