The Australian Cybersecurity Centre (ACSC) has developed a comprehensive framework, the Essential Eight Maturity Model, designed to enhance organisations’ cyber resilience. This model provides a structured approach for practitioners to assess their cybersecurity controls and maturity levels, enabling them to effectively identify and address potential vulnerabilities.
ACSC is an integrated hub within the Australian Signals Directorate (ASD) that collaborates with various industry sectors, government agencies, and academia. Its primary objective is to provide actionable advice, insights, and assistance to organisations nationwide to develop robust cybersecurity strategies.
The ACSC operates under the broader framework of the Australian Government’s Cyber Security Strategy, aiming to defend Australia’s digital landscape against cyber threats. The Essential Eight Maturity Model is a crucial component of this strategy, ensuring organisations have the necessary controls and capabilities to mitigate cyber risks.
The Essentials Eight Framework
The Essentials Eight Framework developed by the ACSC outlines eight essential cybersecurity strategies that CISOs should implement within their organisations. These strategies mitigate the most common cyber threats and enhance overall resilience.
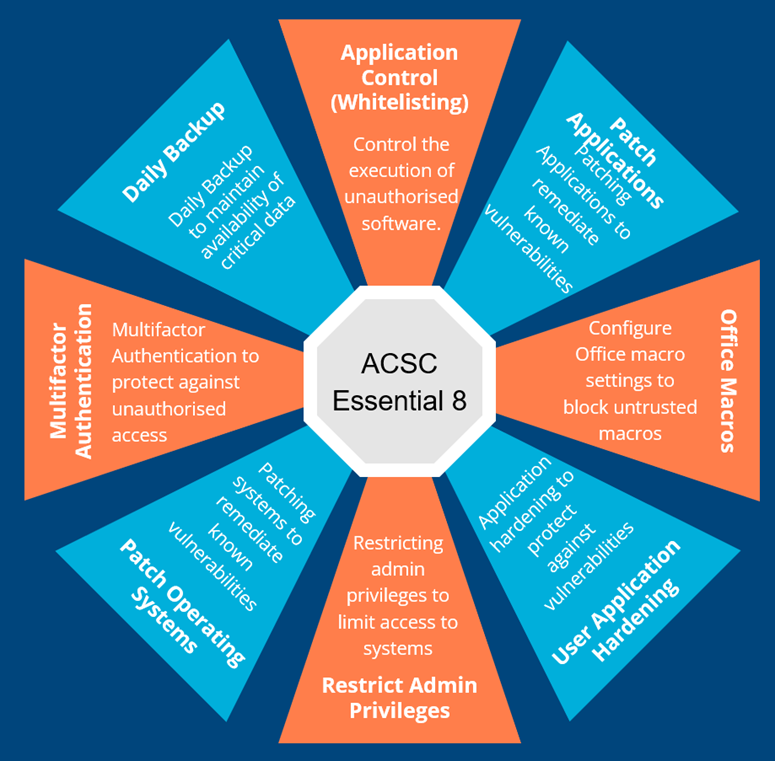
1. Application Whitelisting
Application whitelisting is a practice that allows only approved applications to run on a system, thereby preventing the execution of unauthorised and potentially malicious software. By implementing application whitelisting, organisations can significantly reduce the risk of malware infections and unauthorised code execution.
2. Patch Applications
Keeping software applications updated with the latest security patches is crucial to protect systems from known vulnerabilities. Patch management should be implemented as a routine process to ensure that all applications are patched promptly and effectively.
3. Configuring Microsoft Office Macro Settings
Microsoft Office macros can be exploited as an attack vector by hackers. Therefore, it is essential to properly configure the macro settings in Microsoft Office applications to minimise the risk of macro-based attacks. CISOs should ensure that users are cautious when enabling macros and consider disabling them by default.
4. User Application Hardening
By applying secure configuration settings to user applications, organisations can minimise the potential for unauthorised access and reduce the attack surface for cybercriminals. CISOs must identify and implement appropriate hardening measures for various applications used within their organisation.
5. Restricting Administrative Privileges
Limiting administrative privileges to authorised personnel prevents unauthorised system changes and potential exploitation. By implementing the principle of least privilege, organisations can effectively mitigate the risks associated with malicious insiders and compromised accounts.
6. Patch Operating Systems
Like patching applications, keeping operating systems updated with the latest security patches is vital for maintaining a robust security posture. CISOs should establish a systematic process for patching and regularly monitor the status of all operating systems across their organisation.
7. Multi-Factor Authentication (MFA)
Implementing multi-factor authentication is essential in mitigating the risk of unauthorised access to systems and data. Organisations can significantly enhance their authentication mechanisms by requiring additional verification forms beyond passwords, such as biometrics or tokens.
8. Daily Backups
Regularly backing up critical data is an essential aspect of cybersecurity resilience. In a cyber incident or system failure, reliable and up-to-date backups will enable organisations to quickly restore operations and minimise disruptions.
Cybersecurity Best Practices
In addition to the ACSC’s Essentials Eight, CISOs should consider implementing the following cybersecurity best practices to enhance their organisation’s security posture further:
– Continuous employee training and awareness programs to educate staff about potential cyber threats and best practices.
– Regular vulnerability assessments and penetration testing to proactively identify and address security weaknesses.
– Monitoring and analysing network traffic to detect and respond to potential threats in real-time.
– Developing an incident response plan to manage and mitigate cybersecurity incidents effectively.
Conclusion
The Essential Eight Maturity Model devised by the Australian Cybersecurity Centre offers a comprehensive framework for practitioners to strengthen their cybersecurity defences. By understanding and implementing the key components of this model, organisations can effectively mitigate cyber risks, protect sensitive data, and safeguard against potential threats. It is imperative for practitioners to regularly evaluate and enhance their cybersecurity maturity, enabling them to adapt to the ever-evolving landscape of cyber threats.