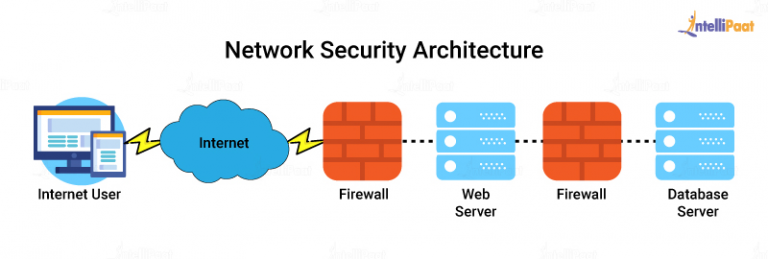
In today’s interconnected digital landscape, network attacks have become a pervasive threat that can have severe consequences for organisations of all sizes. This article will delve into the depths of cybersecurity network attacks and explore effective defence strategies to protect against them.
Understanding Cybersecurity Network Attacks
The importance of understanding how cyberattacks occur.
The different types of cyber-attacks that can target networks.
How cyberattackers exploit vulnerabilities in network systems.
The potential impact of cybersecurity network attacks on organisations.
Why organisations need to be proactive in defending against network attacks.
Types of Cybersecurity Network Attacks
There are several types of cybersecurity network attacks that organisations must be aware of to protect their networks effectively:
1. Phishing Attacks
Phishing tricks users into giving away important information by pretending to be trustworthy sources through email, instant messaging, or phone calls.
2. Malware Attacks
Malware attacks involve using malicious software to gain unauthorised access to a network, steal data, or disrupt operations. This can be done through viruses, worms, trojans, or ransomware.
3. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
DoS and DDoS attacks overwhelm a network or website with excessive traffic, rendering it inaccessible to legitimate users. DoS attacks are usually initiated from a single source, while DDoS attacks involve multiple sources.
4. Man-in-the-Middle (MitM) Attacks
MitM attacks intercept data between two parties without their knowledge. Attackers can eavesdrop on communication, modify data, or deceive both parties into believing they are still directly communicating with each other.
5. SQL Injection Attacks
SQL injection attacks exploit vulnerabilities in a web application’s database management system. Attackers insert malicious SQL code into user input fields to access, modify, or delete sensitive data.
6. Zero-Day Attacks
Zero-day attacks target unknown vulnerabilities or weaknesses in software or systems. Since organisations are unaware of these vulnerabilities, they have no time to develop patches or defences before the attack occurs.
7. Password Attacks
Password attacks involve unauthorised attempts to access a network or system by guessing or cracking passwords. This can be done through brute-force attacks, dictionary attacks, or through the use of password-stealing malware.
8. Social Engineering Attacks
Social engineering attacks exploit human vulnerabilities rather than technical ones. Attackers manipulate individuals psychologically to gain unauthorised access to networks or sensitive information.
9. Advanced Persistent Threats (APTs)
APTs are sophisticated and targeted attacks that aim to infiltrate a network and remain undetected for an extended period. They often involve a combination of social engineering, malware, and other techniques.
Organisations must remain vigilant against these attacks and implement appropriate defence strategies to protect their networks and sensitive information.
Common Vulnerabilities Exploited in Cybersecurity Attacks
Regarding cybersecurity attacks, cyberattackers often exploit common weaknesses in network systems. If left unaddressed, these vulnerabilities can leave organisations susceptible to various attacks.
Consequences of neglecting vulnerabilities
Neglecting to address vulnerabilities in networks can have severe consequences for organisations. Cyberattackers can exploit these weaknesses to gain unauthorised access, steal sensitive data, disrupt operations, or deploy malicious software.
Regular vulnerability assessments
To ensure network security, organisations must conduct regular vulnerability assessments. These assessments involve identifying and analysing network systems, applications, and configurations vulnerabilities. By identifying these weak points, organisations can take steps to address them and minimise the risk of attacks.
Role of software updates and patches
Regular software updates and patches are critical in preventing cyberattacks. Software vendors frequently release updates to fix known vulnerabilities and strengthen security defences. Organisations must regularly update their systems, applications, and firmware to stay protected.
Exploitation through social engineering techniques
Cyberattackers often leverage social engineering techniques to exploit vulnerabilities. These techniques involve manipulating individuals into divulging sensitive information or granting unauthorised access. Employee education and training on recognising and mitigating social engineering attacks are crucial in preventing successful exploitation.
Techniques for Detecting and Analysing Cybersecurity Network Attacks
The importance of real-time network monitoring for detecting attacks.
Standard techniques and tools used for network traffic analysis.
The role of intrusion detection systems in identifying network attacks.
The challenges faced in analysing and attributing network attacks.
The benefits of leveraging machine learning algorithms for attack detection.
Developing Effective Defence Strategies against Cybersecurity Network Attacks
Implementing a robust defence strategy is crucial to safeguard your organisation against cyber-attacks on its network. Here are some key components to consider:
1. Employee Education and Training
One of the most critical aspects of defence is ensuring that all employees are educated and trained in cybersecurity best practices. Regular training sessions should be conducted to raise awareness about the latest attack techniques and how to identify and report potential threats.
2. Threat Intelligence Sharing
Collaboration with other organisations and sharing threat intelligence can significantly enhance defence against network attacks. Your organisation can proactively implement preventive measures by staying informed about the latest attack trends and tactics.
3. Incident Response Plans
Having well-defined incident response plans is crucial for mitigating the impact of network attacks. These plans should outline the steps to be taken when an attack occurs, including communication channels, roles and responsibilities, and recovery strategies.
4. Network Segmentation
Implementing network segmentation can significantly enhance security by dividing networks into smaller, isolated segments. This makes it more difficult for attackers to move laterally within the network, decreasing the potential damage caused by an attack.
By incorporating these strategies into your organisation’s security framework, you can significantly reduce the risk of cyber-attacks and protect sensitive data and systems.
Best Practices for Preventing Cybersecurity Network Attacks
When protecting your network from cyberattacks, implementing best practices is crucial. Here are some key strategies to consider:
1. Strong Passwords and Access Controls
Using strong, unique passwords and employing access controls can significantly reduce the risk of unauthorised access to your network.
2. Regular System and Software Updates
Keeping your systems and software up to date is essential for addressing known vulnerabilities and patching any security flaws.
3. Encryption of Sensitive Network Data
Implementing encryption protocols ensures that sensitive data transmitted over your network remains secure and protected from interception.
4. Implement Multi-Factor Authentication
Enforcing multifactor authentication adds an extra layer of security by requiring users to verify their identity through multiple verification methods.
5. Network Configuration and Firewall Management
Proper network configuration and firewall management are vital in preventing unauthorised access and blocking malicious traffic.
Following these best practices can significantly enhance your network’s security and reduce the risk of cybersecurity network attacks.
Emerging Trends in Cybersecurity Network Attack Prevention
The field of cybersecurity is constantly evolving, and as new technologies emerge, so do new threats. Organisations must stay informed about the latest trends in network attack prevention to defend against cyber threats effectively. Here are some of the emerging trends in cybersecurity network attack prevention:
Advancements in Artificial Intelligence and Machine Learning for Attack Prevention
Artificial intelligence (AI) and machine learning (ML) technologies have proven effective in detecting and preventing network attacks. These technologies enable systems to continuously learn and adapt, allowing for the identification of abnormal network behaviour and the mitigation of potential threats. AI and ML can assist in analysing vast network traffic data, identifying patterns, and predicting future attacks.
The Impact of IoT Devices on Network Attack Surface and Prevention Strategies
The proliferation of Internet of Things (IoT) devices has significantly expanded the network attack surface. These devices often have limited security measures, making them vulnerable to cyberattack exploitation. Organisations must implement robust security protocols for IoT devices, including strong authentication, encryption, and regular firmware updates to mitigate potential risks.
The Rise of Ransomware Attacks and Strategies for Prevention
Ransomware attacks have become increasingly prevalent and damaging. Cybercriminals encrypt valuable data and demand a ransom for its release, causing organisations significant financial and reputation harm. To prevent ransomware attacks, organisations should implement regular data backups, educate employees about phishing techniques, and maintain up-to-date anti-malware software.
The Importance of Threat Hunting and Proactive Defence Measures
Reactive defence strategies are often the main focus of traditional security measures. However, proactive steps like threat hunting are crucial in identifying and mitigating network threats before they cause damage. Threat hunting involves actively searching for signs of compromise or suspicious activities within the network. It requires specialised skills and tools to identify and respond to threats effectively.
The Challenges and Opportunities of Cloud-Based Network Security
As more organisations adopt cloud computing, ensuring the security of cloud-based networks has become paramount. While cloud providers offer robust security measures, organisations must also be responsible for network security. This includes configuring appropriate security settings, monitoring network traffic, and conducting regular audits of cloud infrastructure.
Organisations can enhance their defence strategies and protect their networks from evolving threats by staying informed about the latest cybersecurity network attack prevention trends.
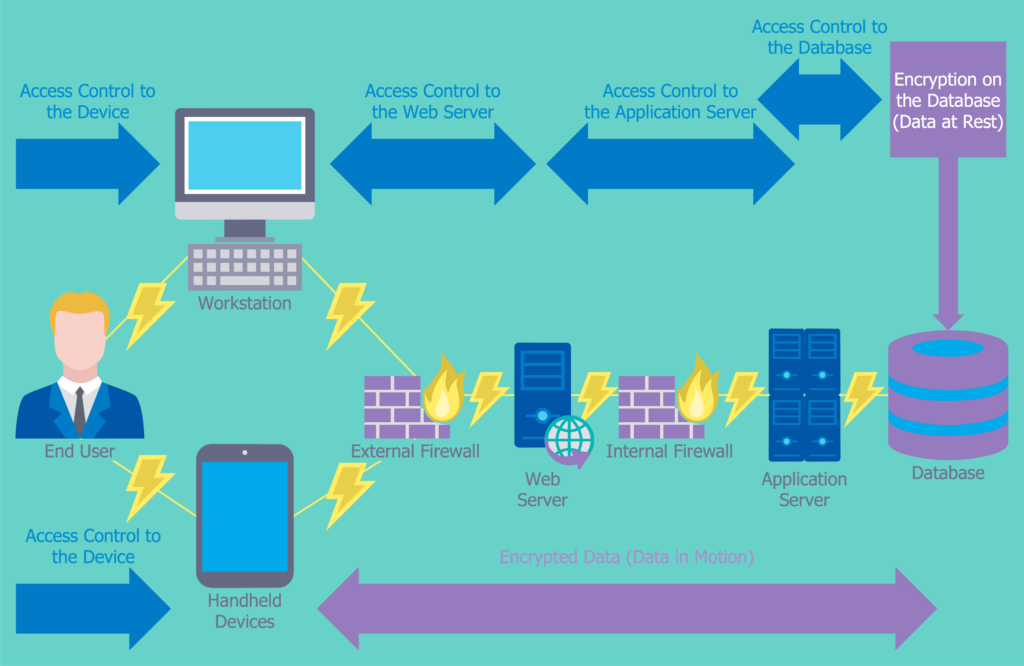
Conclusion
In today’s increasingly digital world, cybersecurity network attacks pose a significant threat to organisations. Understanding how cyber-attacks occur and the different types that can target networks is crucial for organisations to take proactive measures in defending against them.
We have explored common types of cybersecurity network attacks and the methods cyberattackers use to exploit vulnerabilities in network systems. These attacks can lead to severe consequences, including data breaches that significantly impact organisations.
Real-time network monitoring and intrusion detection systems are essential to detect and analyse network attacks effectively. Additionally, leveraging machine learning algorithms can enhance attack detection capabilities.
Organizations should focus on comprehensive network defence strategies, including educating and training employees, sharing threat intelligence, and having incident response plans, to effectively defend against cybersecurity network attacks. Implementing network segmentation can also enhance security measures.
To prevent network attacks, use strong passwords and access controls, update software regularly, encrypt sensitive data, and utilize multifactor authentication.Proper network configuration and firewall management are also essential.
Cybersecurity will use AI and machine learning to stop network attacks, focus on the effects of IoT devices, handle ransomware, and prioritize proactive defence and threat hunting.Cloud-based network security presents both challenges and opportunities.
In conclusion, by staying informed about the threat landscape and implementing robust defence strategies, organisations can better protect their networks against cybersecurity attacks. It is a collective effort to ensure the security of our digital infrastructure and safeguard sensitive information.