The threat landscape in the digital world is constantly evolving, with cyber-attack organisations becoming increasingly sophisticated and pervasive. Organisations of all sizes and industries face the daunting task of defending their systems and data against these relentless threats. However, to effectively protect themselves, organisations must first understand the anatomy of cyber threats and the tactics employed by cyber adversaries.
Exploring the MITRE ATT&CK Framework
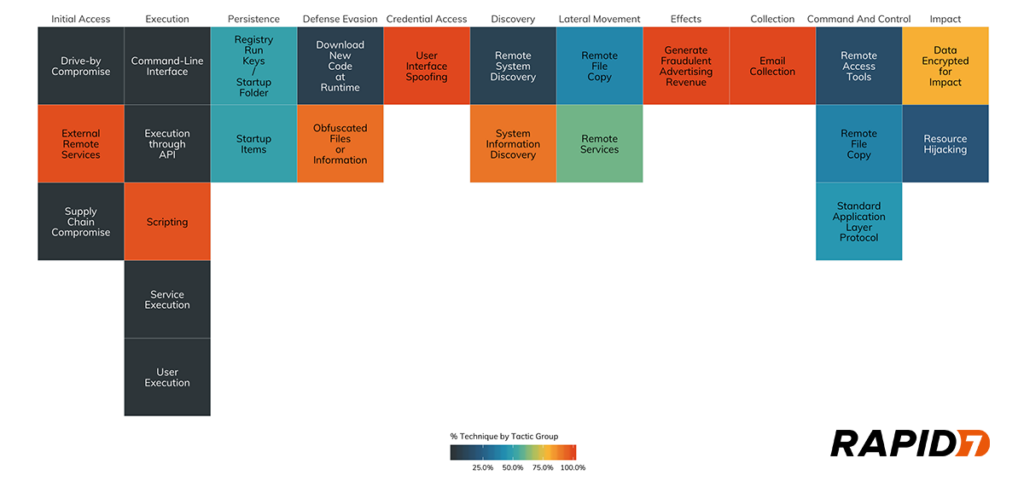
The MITRE ATT&CK Framework is a comprehensive tool that helps organisations understand cyber threats and develop effective defence strategies.
By familiarising themselves with the MITRE ATT&CK Framework, organisations can gain insights into the tactics and techniques employed by cyber adversaries.
Demystifying Cyber Threats
Cyber threats can be intimidating, but understanding their origins and motives can help organisations better protect themselves.
Demystifying cyber threats involves gaining knowledge about the various types of attacks, such as phishing, ransomware, and social engineering, and the methods used by attackers.
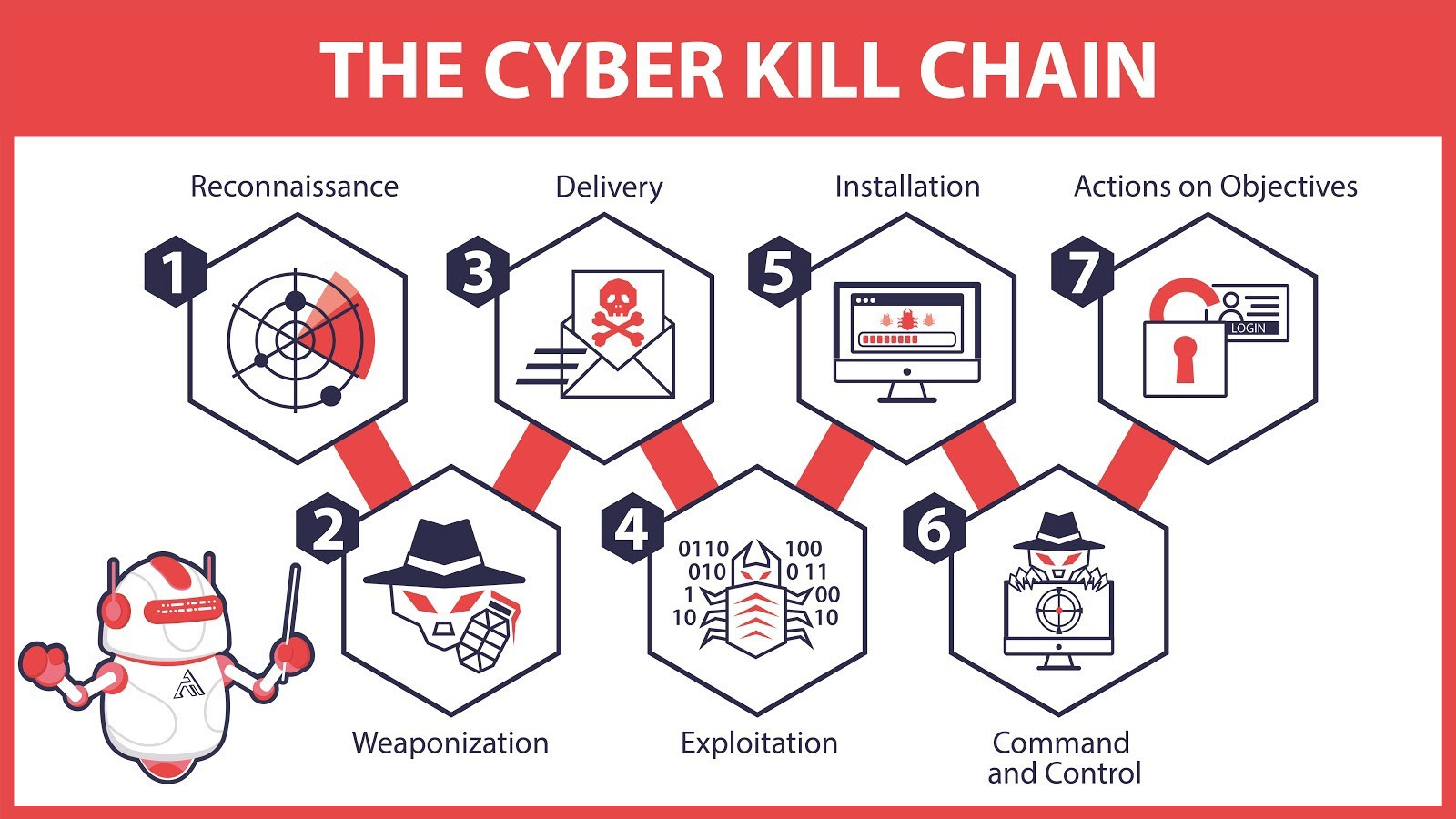
Navigating the Anatomy of Attacks
To effectively defend against cyber-attacks, organisations need to understand the different stages of an attack and how they are interconnected.
Navigating the anatomy of attacks involves examining the tactics and techniques employed by attackers, from initial access to data exfiltration to identifying potential vulnerabilities.
Understanding the Techniques and Tactics
The MITRE ATT&CK Framework provides a comprehensive overview of the techniques and tactics used by cyber adversaries. By understanding these techniques and tactics, organisations can develop robust defence strategies and stay one step ahead of attackers.
Some of the essential techniques and tactics employed by cyber adversaries include:
- Spear Phishing: This involves sending targeted emails or messages to specific individuals or organisations to deceive them into revealing sensitive information or installing malware.
- Exploiting Software Vulnerabilities: Cyber adversaries often take advantage of weaknesses in software programs or systems to gain unauthorised access or control.
- Brute Force Attacks: Attackers attempt to gain access to systems by repeatedly guessing passwords or encryption keys until they find the correct one.
- Command and Control (C2) Communication: Adversaries establish communication channels with compromised systems to control and manage them remotely.
- Data Exfiltration: Attackers attempt to steal or exfiltrate sensitive data from compromised systems for their gain.
- Credential Theft: Cyber adversaries employ various techniques to steal usernames, passwords, and other authentication credentials to gain unauthorised access to systems or accounts.
By understanding these techniques and tactics, organisations can develop proactive defence strategies to detect and mitigate potential cyber threats. This may involve implementing strong access controls, training employees about safe online behaviour, and deploying effective monitoring and detection systems.
It’s essential for organisations to continuously update their knowledge of new techniques and tactics employed by cyber adversaries and stay informed about emerging threats. Doing so can improve their overall cybersecurity posture and reduce the likelihood and impact of cyber attacks.
Identifying Common Vulnerabilities
Cyber attackers often exploit common vulnerabilities to gain unauthorised access to systems and networks.
By identifying common vulnerabilities, organisations can take proactive measures to patch or mitigate them, reducing the risk of successful attacks.
Analysing Advanced Persistent Threats
Advanced Persistent Threats (APTs) are sophisticated and stealthy cyber-attacks that well-funded and resourceful adversaries often carry out.
APTs use advanced techniques to gain unauthorised access to systems and networks, remain undetected for long periods, and exfiltrate sensitive data.
When analysing APTs, examining the tactics, techniques, and procedures employed by these adversaries and their motivations and goals is essential.
APTs often target specific organisations or industries seeking to steal intellectual property and sensitive data or gain a competitive advantage.
To uncover APTs, security professionals employ a combination of network monitoring, threat intelligence analysis, and forensic investigation techniques.
Understanding the infrastructure, tools, and communication channels APT actors use can provide valuable insights for developing effective defence strategies.
Organisations should also consider the geopolitical context, as APTs are often tied to nation-states or state-sponsored groups with specific political or economic motivations.
Uncovering Nation-State Attacks
Nation-state attacks pose a significant threat to governments and organisations, as they are often well-funded, highly skilled, and politically motivated.
Uncovering nation-state attacks requires extensive analysis of the tools, techniques, and infrastructure these attackers use and the geopolitical context.
Detecting Insider Threats
Insider threats involve individuals within an organisation who misuse their privileges or access to intentionally or unintentionally harm the organisation.
Detecting insider threats requires monitoring user activities, implementing access controls, and training employees to recognise and report suspicious behaviour.
Countering Malware and Exploits
Cyber attackers commonly use Malware and exploits to gain unauthorised access, compromise systems, and steal sensitive information. Organisations must have effective countermeasures in place to protect against these threats.
Implement Robust Antivirus and Antimalware Solutions: Installing and regularly updating antivirus and antimalware software on all devices can help detect and remove malicious programs hiding in the system.
Regularly Patch Software Vulnerabilities: Keeping software up to date with the latest patches and security updates is essential to prevent exploiting known vulnerabilities by attackers.
Educate Users about Safe Online Behavior: Training employees and users to recognise and avoid suspicious emails, websites, and downloads can significantly reduce the chances of malware infections and exploits.
Implement Strong Access Controls: Limiting user privileges and enforcing the principle of least privilege can help mitigate the risk of malware and exploit propagation throughout the network.
Monitor Network Traffic: Implementing network monitoring tools can help identify and block suspicious traffic patterns associated with malware and exploit activities.
Enable Firewall Protection: Firewalls can be a barrier between the organisation’s internal network and external threats, blocking unauthorised access attempts.
By adopting these countermeasures and regularly updating them, organisations can significantly reduce the risk of falling victim to malware and exploit attacks.
Mitigating Risks and Strengthening Defences
Mitigating risks and strengthening defences is an ongoing process requiring a proactive cybersecurity approach. By implementing a layered security approach, organisations can create multiple hurdles for cyber attackers to overcome, reducing the likelihood of successful breaches.
Conduct Regular Security Assessments
Regular security assessments are crucial in identifying vulnerabilities and potential weak points in an organisation’s systems and networks. Organisations can proactively address any security gaps and implement necessary measures to strengthen their defences by conducting these assessments.
Stay Updated on Emerging Threats
The cybersecurity landscape constantly evolves, with new threats and attack techniques emerging regularly. Organisations need to stay updated on the latest threat intelligence and security trends to stay ahead of cyber attackers. This includes monitoring industry reports, attending security conferences, and engaging with information-sharing communities.
Implement a Layered Security Approach
A layered security approach involves implementing multiple security controls within an organisation’s infrastructure at different levels. This includes firewalls, intrusion detection systems, secure email gateways, endpoint protection, and user access controls. By layering these defences, organisations can significantly enhance their ability to detect and prevent cyber threats.
Educate Users about Safe Online Behavior
Employees are often the first line of defence against cyber attacks. By providing regular cybersecurity awareness training, organisations can educate their employees about safe online practices, such as identifying phishing emails, using strong passwords, and avoiding suspicious downloads. This helps to minimise the risk of human error, leading to successful attacks.
Overall, by continuously improving their cybersecurity defences, organisations can effectively mitigate risks and protect their sensitive information, ensuring their operations’ long-term security and success.
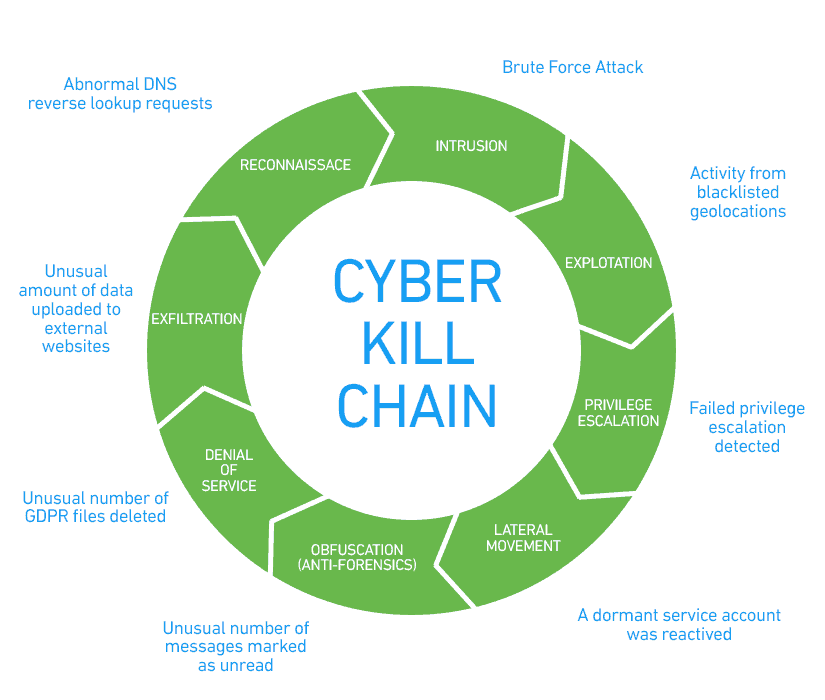
Conclusion
The MITRE ATT&CK Framework is a valuable tool for organisations to understand and navigate the complex world of cyber threats. By familiarising themselves with the framework and gaining insights into the tactics and techniques used by cyber adversaries, organisations can develop effective defence strategies and stay one step ahead of attackers.
Demystifying cyber threats and understanding the anatomy of attacks are essential steps in strengthening cybersecurity defences. Organisations can proactively mitigate risks and protect their systems and networks by identifying common vulnerabilities, analysing advanced persistent threats, uncovering nation-state attacks, and detecting insider threats.
Countering malware and exploits is crucial for safeguarding sensitive information, and implementing robust antivirus and antimalware solutions, regularly patching software vulnerabilities, and educating users about safe online behaviour are effective measures to counteract these threats.
Mitigating risks and strengthening defences is an ongoing process that requires a layered security approach, regular security assessments, and staying up-to-date on emerging threats. By continuously improving their reasons, organisations can enhance their overall cybersecurity posture and reduce the likelihood and impact of cyber attacks.
Overall, the MITRE ATT&CK Framework provides valuable insights into the anatomy of cyber threats and equips organisations with the knowledge they need to protect themselves against these evolving risks. By understanding the techniques and tactics employed by cyber adversaries, organisations can develop effective defence strategies and ensure the security of their systems and networks.