Introduction
Network microsegmentation is a crucial component of any comprehensive cybersecurity strategy. In today’s digital landscape, where cyber threats are becoming increasingly sophisticated, protecting your business from potential breaches is paramount.
What is network microsegmentation?
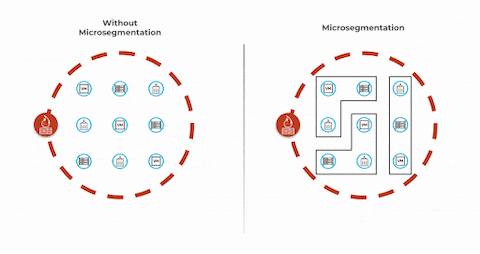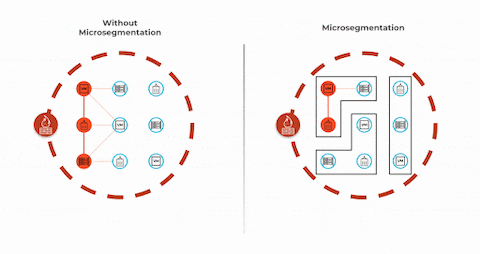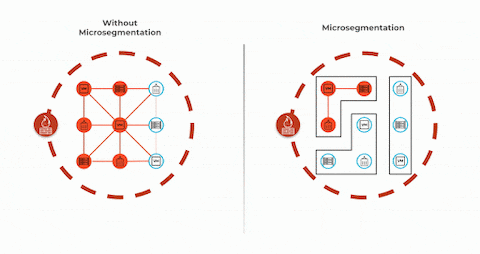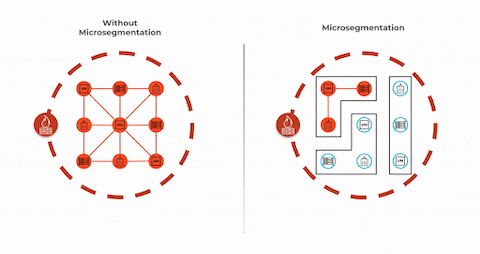
Network microsegmentation is the practice of dividing a network into smaller, isolated segments or subnetworks. Each segment is then secured individually, adding an extra layer of protection against unauthorized access. Implementing network microsegmentation helps businesses restrict lateral movement in their systems, making it difficult for attackers to navigate the network and access sensitive information.
Importance of network microsegmentation in cybersecurity
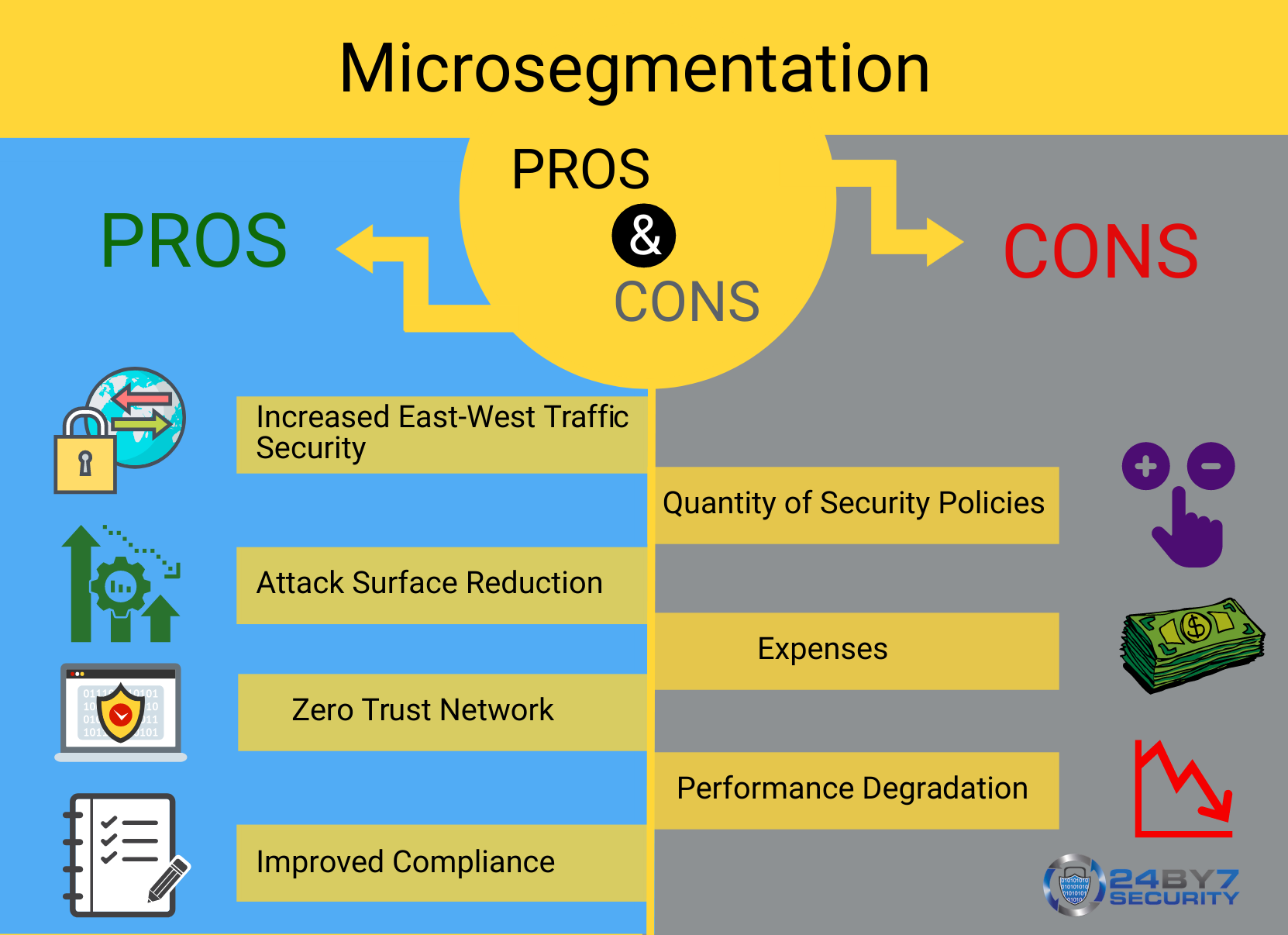
Network microsegmentation offers several key benefits in terms of cybersecurity:
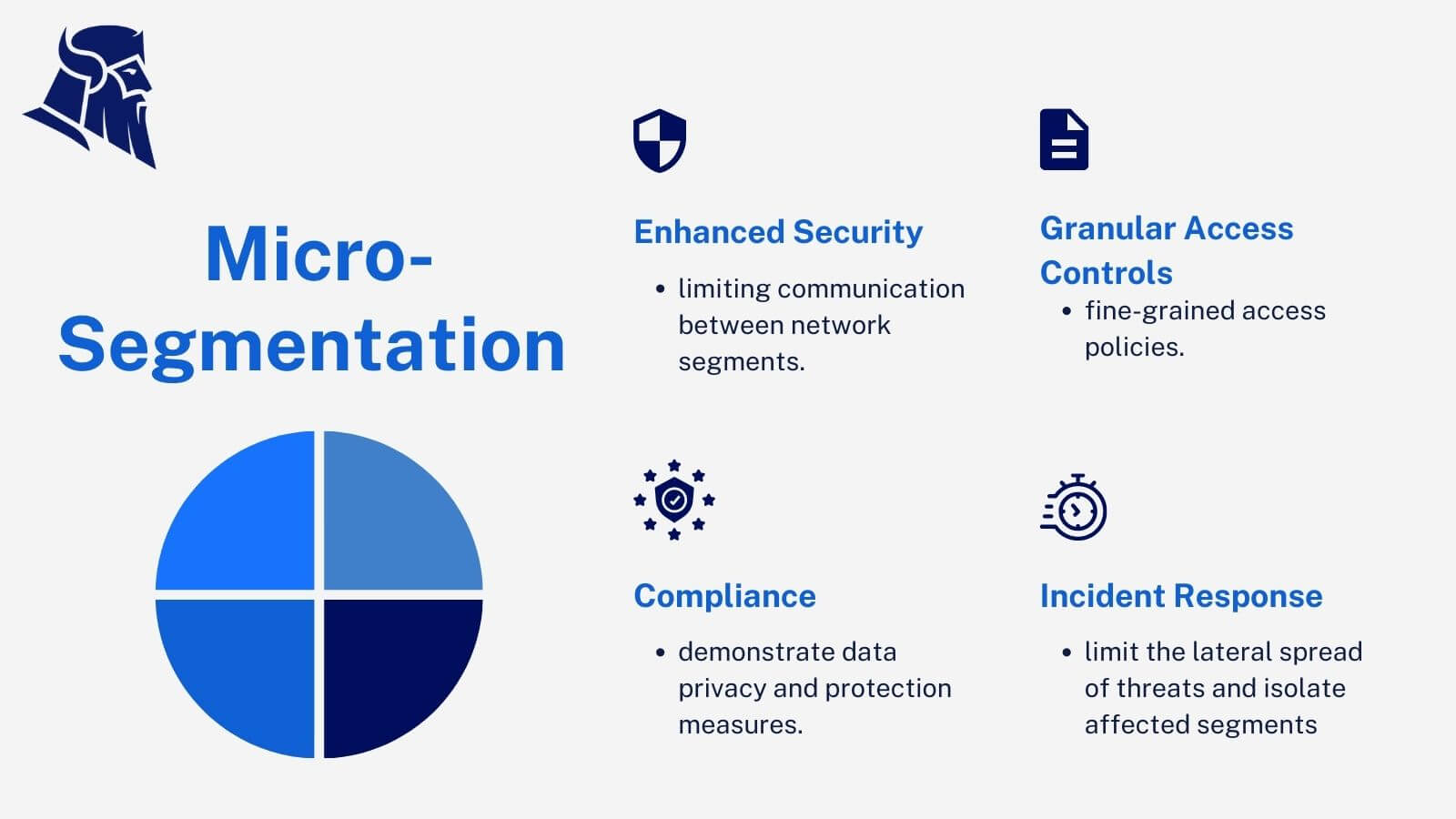
- Enhanced security: By isolating different parts of the network, even if one segment is compromised, the breach is contained and cannot spread to other areas.
- Reduced attack surface: Microsegmentation reduces the attack surface by limiting access to critical resources, making it harder for cybercriminals to find vulnerable entry points.
- Granular control: With network microsegmentation, businesses can have fine-grained control over who can access specific network resources, allowing for more robust access controls.
- Compliance: Many industry regulations and standards require businesses to have strong network security measures in place. Network microsegmentation helps meet these requirements by providing additional layers of protection.
In conclusion, network microsegmentation is an essential aspect of cybersecurity. By implementing this strategy, businesses can enhance their overall security posture, minimize the impact of potential breaches, and safeguard their critical data and assets.
Understanding Cyber Threats
Types of cyber threats businesses face
Understanding the types of cyber threats that businesses face is crucial for implementing effective security measures. Some common types of cyber threats include:
- Malware: Malicious software such as viruses, ransomware, and spyware that can harm computer systems, steal sensitive information, or hold data hostage.
- Phishing: A form of cyber attack where attackers disguise themselves as trustworthy entities to trick employees into providing sensitive information or downloading malicious files.
- Denial of Service (DoS) attacks: Overloading a system or network with excessive traffic to disrupt its normal functioning and deny access to legitimate users.
Consequences of cyber attacks on businesses
The consequences of cyber attacks on businesses can be severe and far-reaching. Some common consequences include:
- Data breaches: Unauthorized access to sensitive customer or company data, leading to financial loss, reputational damage, and potential legal repercussions.
- Financial loss: Cyber attacks can result in direct financial losses due to theft, business interruption, or the cost of recovering from the attack.
- Reputational damage: A cyber attack can damage a company’s reputation, leading to a loss of customer trust and loyalty.
- Operational disruptions: Cyber attacks can disrupt business operations, leading to downtime, loss of productivity, and delayed delivery of products or services.
By understanding the types of cyber threats businesses face and the consequences of cyber attacks, businesses can take proactive steps to protect their networks and sensitive data. Network microsegmentation is one effective strategy that can help businesses strengthen their security and mitigate the risk of cyber threat
The Basics of Network Microsegmentation
Definition and purpose of network microsegmentation
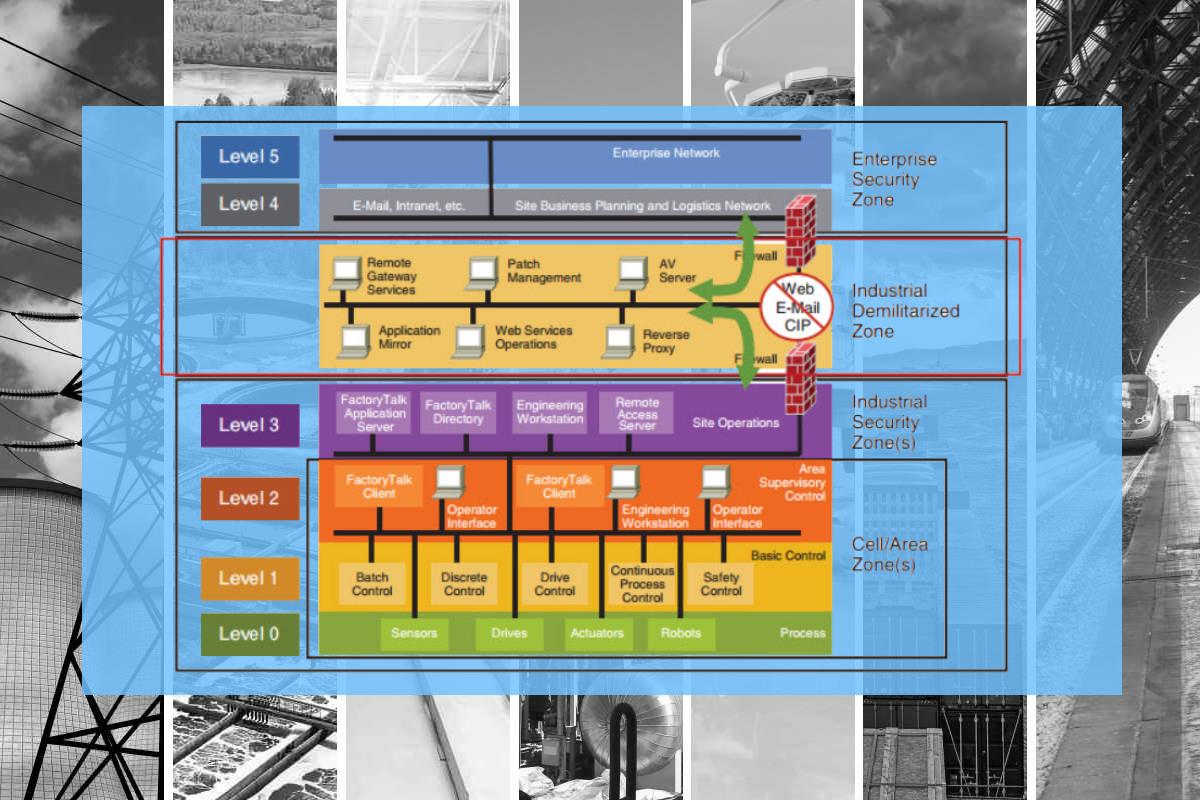
Network microsegmentation is an advanced security technique that involves dividing a network into smaller segments or subnetworks. Segments are isolated to create security zones that protect assets and data from cyber threats. The purpose of network microsegmentation is to enhance network security by minimizing the lateral movement of attackers within the network and limiting the impact of a potential breach.
How network microsegmentation works
Network microsegmentation is typically implemented through software-defined networking (SDN) technologies. By using virtualization and software-defined policies, network administrators can define specific access rules and control traffic flow between different segments. This allows them to set granular and fine-grained security policies tailored to the needs of each segment. Network microsegmentation helps contain an attack within a specific part of the network, preventing it from spreading to other areas in the event of a breach.
In summary, network microsegmentation provides added layers of security and control by creating isolated segments within a network. Implementing this technique helps businesses lower the risk of cyberattacks and better safeguard their valuable assets and data.
Benefits of Network Microsegmentation
Enhanced network security
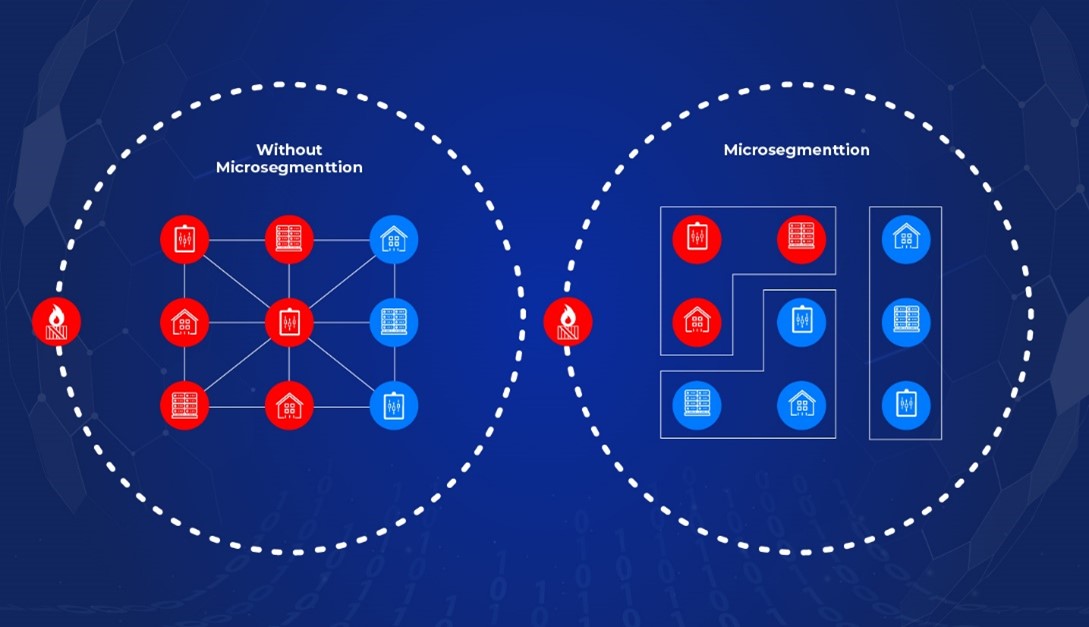
Network microsegmentation is a powerful strategy that can significantly enhance network security. By dividing a network into smaller segments, each with its own security policies and controls, organizations can strengthen their defense against cyber threats. This granular approach allows for more effective monitoring and enforcement of security measures, reducing the potential for unauthorized access or lateral movement within the network. With network microsegmentation, even if one segment is compromised, the rest of the network remains protected, minimizing the impact of a breach.
Improved visibility and control
Implementing network microsegmentation provides organizations with improved visibility and control over their network traffic. By explicitly defining communication paths within and between segments, administrators can gain a comprehensive understanding of the network’s behavior and identify any anomalies or suspicious activities more easily. This enhanced visibility empowers organizations to proactively detect and mitigate potential security threats before they escalate.
Isolation and containment of cyber threats
One of the key benefits of network microsegmentation is the ability to isolate and contain cyber threats. Dividing the network into separate segments prevents any malicious activity or breach from spreading to other areas. This containment limits the potential damage caused by cyber threats and enables organizations to quickly identify and respond to security incidents within the affected segment. This proactive approach enhances overall network resilience and minimizes the risk of widespread disruptions or data breaches.
Network microsegmentation enhances network security, improves visibility and control, and isolates and contains cyber threats. By implementing this strategy, organizations can ensure a more robust and resilient network infrastructure in the face of evolving cybersecurity challenges.
Implementing Network Microsegmentation
Microsegmentation is a cybersecurity technique that divides a network into smaller segments and applies strict access control policies to enhance security and protect sensitive data. In today’s digital landscape, businesses need a strategy to protect against constantly evolving cyber threats.
Identifying network segments
The first step in implementing network microsegmentation is to identify and categorize different network segments based on their functions, dependencies, and security requirements. This process involves analyzing network traffic patterns, mapping network infrastructure, and determining the critical assets that need to be protected.
Setting up access control policies
Once the network segments have been identified, the next step is to establish access control policies for each segment. This involves defining and enforcing strict rules and permissions that dictate who can access specific network resources and from where. Designing policies with a defense-in-depth approach is crucial. Consider user roles, IP addresses, and protocols to ensure maximum security.
Monitoring and maintaining network microsegmentation
Network microsegmentation is not a one-time setup but an ongoing process that requires continuous monitoring and maintenance. Regular audits should be conducted to ensure that access control policies are being followed and to identify any unauthorized access attempts or potential security breaches. Additionally, network administrators should stay updated with the latest cybersecurity threats and best practices to adapt their microsegmentation strategy accordingly.
Network microsegmentation can help businesses reduce their attack surface, manage cyber threats, and improve network security. It provides granular control over network resources, minimizes lateral movement within the network, and strengthens the overall resilience of the organization’s cybersecurity infrastructure.

Best Practices for Network Microsegmentation
Defining security zones and policies
One of the key best practices for network microsegmentation is to define security zones and policies. This involves dividing your network into segments based on specific criteria such as department, function, or level of sensitivity. Each segment should have its own set of security policies that are tailored to its unique requirements. This allows you to have granular control over access and security within each segment, minimizing the risk of lateral movement within your network in the event of a breach.
Regularly updating access control lists
Another important best practice is to regularly update access control lists (ACLs). ACLs define the permissions and restrictions for network traffic within each segment. By keeping these ACLs up to date, you can ensure that only authorized traffic is allowed and that any changes in network access requirements are properly accounted for. Regularly reviewing and updating ACLs helps to detect and prevent possible vulnerabilities or misconfigurations that cyber threats could exploit.
Conducting security audits and assessments
Regular security audits and assessments are crucial for maintaining the effectiveness of network microsegmentation. These audits help to identify any gaps or weaknesses in your segmentation strategy and allow you to take corrective actions. To make sure your microsegmentation measures align with your security goals, assess your network security controls and configurations thoroughly.
Implementing these best practices for network microsegmentation can greatly enhance your organization’s ability to protect against cyber threats. By defining security zones and policies, regularly updating ACLs, and conducting security audits, you can significantly reduce the risk of unauthorized access and lateral movement within your network.
Challenges and Considerations
Network performance impact
When implementing network microsegmentation for your business, it is important to consider the potential impact on network performance. Microsegmentation enhances network security by dividing it into smaller segments, isolating sensitive data and minimizing the impact of a breach. However, it can also introduce additional latency and increase network complexity.
To minimize performance impact, it is essential to carefully plan your microsegmentation strategy. Consider the following factors:
- Traffic patterns: Analyze your network traffic to identify critical applications and communication patterns. This will help you determine the optimal placement of security controls and minimize disruptions to performance.
- Network architecture: Design your network architecture with scalability and performance in mind. Ensure your network infrastructure can handle increased traffic and security controls by mapping out segmentation boundaries.
- Monitoring and optimization: Implement monitoring tools to continuously assess network performance and identify any bottlenecks or issues. Regularly optimize your microsegmentation policies based on network usage and security requirements.
By addressing these considerations, you can achieve effective network microsegmentation while minimizing the impact on performance. This will help protect your business against cyber threats without compromising the efficiency and reliability of your network infrastructure.
Network Microsegmentation Solutions
Leading network microsegmentation tools and software
In today’s rapidly evolving cyber threat landscape, it has become increasingly crucial for businesses to implement effective security measures. Network microsegmentation is a way to protect your business from cyber threats. It works by dividing your network into smaller segments and putting security controls in place for each segment.
There are several leading network microsegmentation tools and software available in the market. These solutions provide advanced features and functionalities to safeguard your network infrastructure. Some of the top solutions include:
- VMware NSX: VMware NSX offers network virtualization and microsegmentation capabilities, allowing organizations to create granular security policies and control network traffic.
- Cisco ACI: Cisco’s Application Centric Infrastructure (ACI) provides end-to-end network automation and microsegmentation capabilities to enhance security and simplify network management.
- Guardicore Centra: Guardicore Centra offers comprehensive microsegmentation capabilities, enabling businesses to protect critical assets, detect and respond to threats, and comply with regulatory requirements.
Comparison of different network microsegmentation solutions
Consider ease of deployment, scalability, integration with existing security tools, and vendor support when choosing a network microsegmentation solution. Here’s a comparison table of the aforementioned solutions:
| Solution | Key Features |
|---|---|
| VMware NSX | – Granular security policies – Network virtualization – Automation and orchestration capabilities |
| Cisco ACI | – End-to-end network automation- Microsegmentation capabilities- Centralized management and policy enforcement |
| Guardicore Centra | – Comprehensive microsegmentation- Threat detection and response- Compliance management- Integration with existing security and IT tools |
By implementing network microsegmentation solutions, businesses can significantly enhance their security posture and protect their valuable assets from cyber threats.

Case Studies
Real-world examples of businesses benefiting from network microsegmentation
Network microsegmentation has proven to be an effective strategy for protecting businesses from cyber threats. Here are some real-world examples that demonstrate its benefits.
- Company A: A multinational corporation that operates in various industries implemented network microsegmentation to enhance its security posture. By dividing its network into smaller segments and implementing strict access controls, they were able to contain the spread of cyberattacks and prevent unauthorized access to critical systems.
- Company B: A financial institution experienced a data breach that resulted in significant financial loss and reputational damage. To prevent future incidents, they implemented network microsegmentation to isolate their sensitive data and critical infrastructure. This allowed them to monitor and control access to these assets more effectively, minimizing the impact of potential cyber threats.
- Company C: An e-commerce company faced constant threats from hackers attempting to breach their systems and steal customer data. By implementing network microsegmentation, they were able to create separate segments for their web servers, databases, and payment gateways. This not only improved security but also ensured that any compromise in one area would not affect the entire network.
These case studies demonstrate how network microsegmentation can provide businesses with the necessary security measures to protect against cyber threats. By effectively controlling access and segmenting their networks, organizations can mitigate risks and safeguard their critical assets.

Conclusion
Summary of the benefits and importance of network microsegmentation
Network microsegmentation is a powerful security strategy that can protect your business from cyber threats. To prevent a single cyberattack from compromising your entire system, divide your network into smaller segments and enforce strict controls and policies. Some of the key benefits and importance of network microsegmentation include:
- Enhanced Security: Network microsegmentation provides an additional layer of security by limiting the exposure of sensitive data and systems. It allows you to control and monitor traffic between segments, reducing the chances of unauthorized access or data breaches.
- Containment: In the event of a cyberattack, microsegmentation helps contain the impact by isolating compromised segments and preventing the spread of the attack to other parts of the network. This limits the potential damage and allows for faster incident response and recovery.
- Compliance: Microsegmentation helps organizations meet regulatory compliance requirements by providing granular control over data access and ensuring segregation of duties. It enables better visibility and auditability, making it easier to demonstrate compliance with industry standards.
- Scalability: Network microsegmentation is scalable, allowing organizations to easily adapt and expand their security infrastructure as their business grows. It provides a flexible framework that can be adjusted to accommodate changing security requirements and network architectures.
Using network microsegmentation in your cybersecurity strategy can greatly improve your security and protect your business from cyber threats. By implementing this proactive approach, you can ensure the confidentiality, integrity, and availability of your critical resources and data.