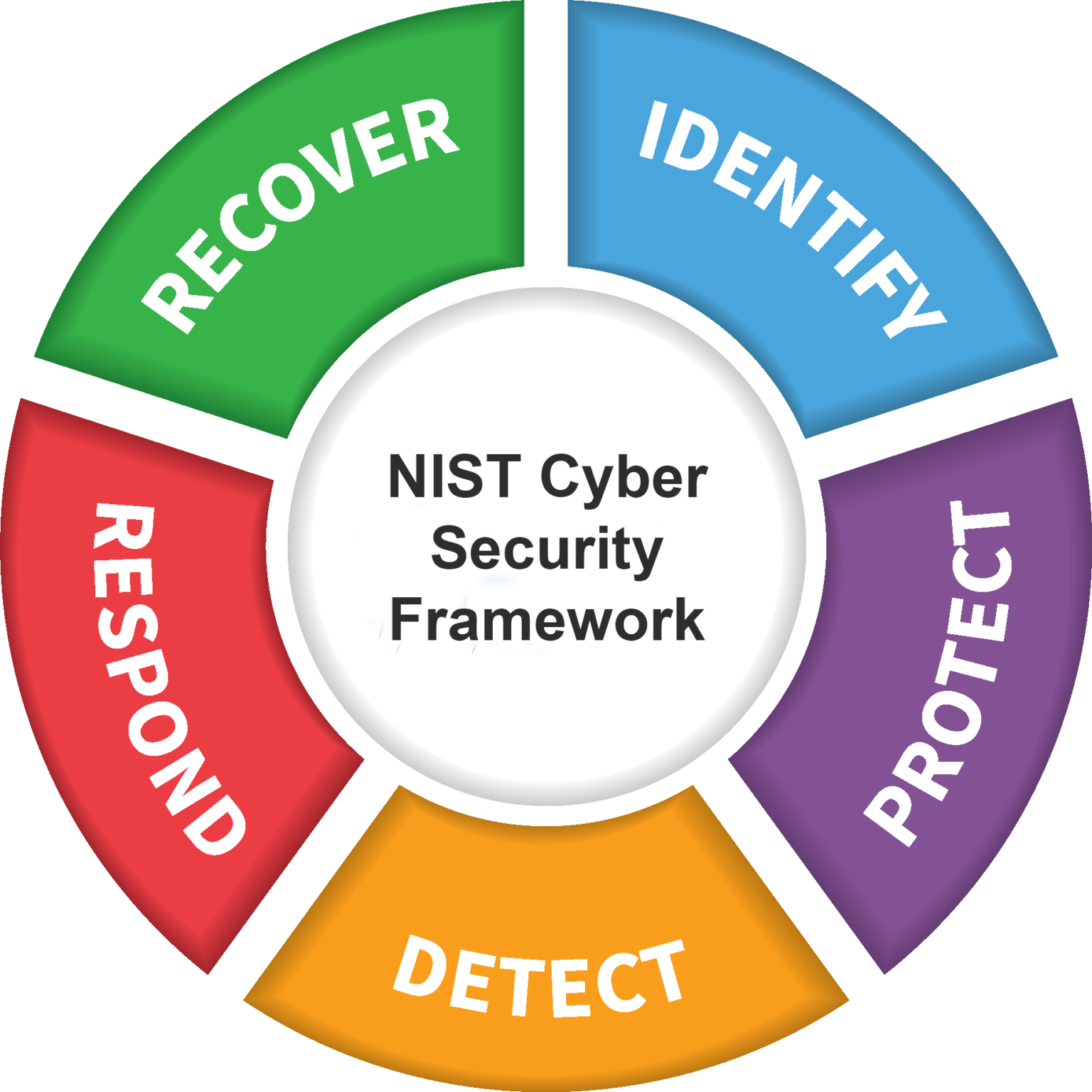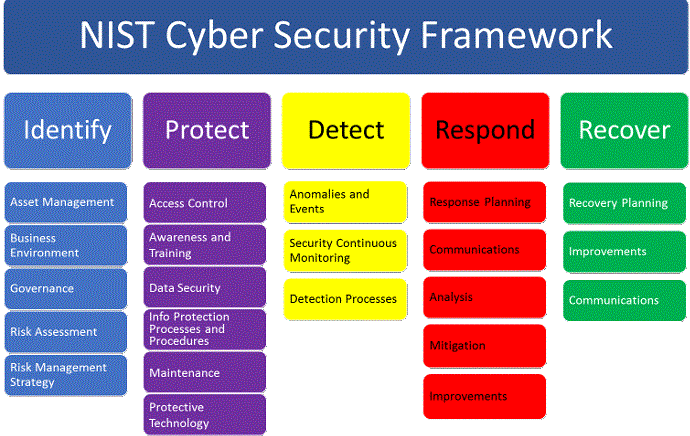
The NIST framework is a widely used cybersecurity framework designed by the National Institute of Standards and Technology (NIST) in the USA. It is a comprehensive guide that helps organizations to assess and manage cybersecurity risks. The framework aims to provide a set of guidelines, standards, and best practices for organizations to strengthen their cybersecurity posture. In this guide, we will discuss what exactly is the NIST framework and how to use it to secure your systems.
The NIST framework consists of five core functions: Identify, Protect, Detect, Respond, and Recover. These functions represent the key elements of a cybersecurity program.
Identify:
This function is aimed at understanding the organization’s risk level and potential threats. It requires the organizations to conduct an inventory of all their assets and information, including hardware, software, data, and personnel. Once the assets and information have been identified, organizations should determine the level of confidentiality, integrity, and availability required for each asset.
Protect:
The protect function aims to safeguard the assets and information identified in the previous step. This function includes the implementation of security policies, procedures, and mechanisms to prevent or reduce the impact of a security event. The goal is to ensure the confidentiality, integrity, and availability of the assets and information.
Detect:
This function aims to detect security events as early as possible. It requires organizations to implement the necessary tools and techniques to identify anomalies or suspicious behavior on their systems. By detecting these events early, organizations can reduce the impact and prevent further damage.
Respond:
This function focuses on the response to a security event. It includes the development of an incident response plan and the necessary procedures to contain and mitigate the impact of a security event. Organizations must have a well-defined plan in place to quickly respond to security incidents.
Recover:
The recover function is aimed at restoring information and systems back to normal operating conditions after a security event. This includes restoring data from backups, repairing damaged systems, and resuming operations as quickly as possible.
To use the NIST framework effectively, organizations must follow a systematic approach. First, they need to identify the assets and information that need to be protected. Once this is done, they can use the framework’s functions to develop a comprehensive cybersecurity program. This program should include the following:
– Security policies and procedures to protect the assets and information
– Configuration management practices to ensure the security of hardware and software
– Continuous monitoring of systems to detect security events early
– An incident response plan to respond to security events
– Regular testing and evaluation to ensure that the cybersecurity program is effective and up to date
By following this approach, organizations can enhance their cybersecurity posture and reduce the risk of a security event. In conclusion, the NIST framework provides a practical and holistic approach to managing cybersecurity risks. Organizations that implement this framework can better protect their assets and information, detect security events early, respond effectively to security incidents, and recover quickly from an event.