
Introduction
In the world of cybersecurity, even a breach at a highly reputable company like Okta can serve as a wake-up call for businesses everywhere. In this article, we will take a deep dive into the Okta breach, analyzing its impact, timeline, and lessons to be learned.
Overview of the Okta Breach
Okta, a leading identity management company, experienced a security breach that compromised user information and raised concerns about the safety of sensitive data. The attack focused on the company’s authentication system, which is important for verifying user identities and granting access to different applications.
Hackers gained unauthorized access to Okta’s infrastructure, potentially exposing user login credentials and other personal information. This breach has significant repercussions for both Okta and its users, as it undermines trust in the company’s ability to protect customer data.
Timeline of the Attack
The Okta breach unfolded over a period of several weeks, as the attackers exploited vulnerabilities in the company’s systems. The timeline of events is as follows:
- Initial Compromise: The attackers gained a foothold in Okta’s network by exploiting a vulnerability in a third-party software the company was using.
- Reconnaissance: Once inside, the hackers conducted extensive reconnaissance to identify high-value targets and gather sensitive information.
- Credential Theft: The attackers targeted Okta’s authentication system, stealing user login credentials and potentially gaining access to users’ accounts.
- Data Exfiltration: As the breach went undetected, the attackers exfiltrated stolen data, including personal information and confidential business data.
- Discovery and Response: Okta’s security team eventually discovered the breach and initiated an investigation and response plan to contain the incident and mitigate further damage.
The Okta breach serves as a stark reminder of the ever-present threat of cyberattacks, even for companies with robust security measures in place. It highlights the importance of continuous monitoring, vulnerability management, and incident response capabilities. Businesses can learn from incidents like this to enhance their security and safeguard themselves and their customers against future breaches.
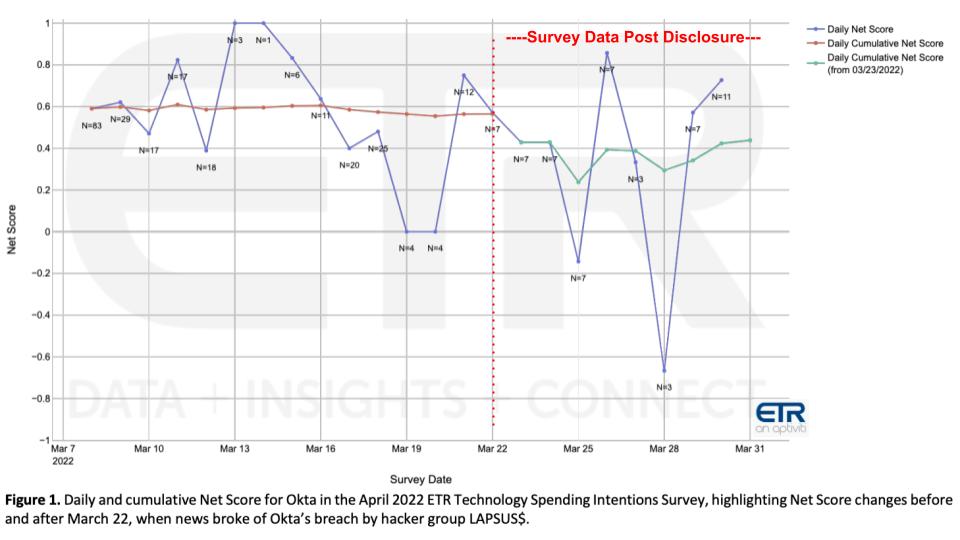
Background
Brief history of Okta
Okta, founded in 2009, is a renowned identity management company that provides businesses with secure and centralized access control solutions. It offers a cloud-based platform that helps organizations manage user authentication, authorization, and user lifecycle management across various applications and devices. Okta’s services have gained popularity due to their ability to enhance security while simplifying the user experience.
Importance of Okta’s security measures
Okta prioritizes security and invests heavily in developing robust measures to protect user information. The company values the trust placed in its platform, especially due to the sensitive nature of the data it manages. Okta’s security measures are designed to prevent unauthorized access and protect user identities.
Okta employs multiple layers of security, including multi-factor authentication, encryption, and continuous monitoring, to safeguard user accounts and data. They regularly update their software and systems to stay ahead of emerging threats and vulnerabilities. Additionally, Okta undergoes independent audits and certifications to ensure compliance with industry standards and best practices.
The Okta breach highlighted the sophistication of cyberattacks and the need for organizations to continually strengthen their security measures. While no security system is completely impervious, Okta’s incident response plan and detection capabilities helped them discover the breach and respond promptly. This incident serves as a reminder that even the most advanced security measures are not foolproof, emphasizing the importance of continual evaluation, improvement, and proactive threat intelligence in maintaining the security of user data.
Attack Methodology
How the attackers gained access
Through extensive analysis of the Okta breach, it was discovered that the attackers gained unauthorized access to the system through a sophisticated phishing campaign. The attackers utilized social engineering techniques to trick employees into revealing their credentials, providing them with a foothold within Okta’s infrastructure. This highlights the importance of employee education and awareness in preventing such attacks.
Exploited vulnerabilities in Okta’s system
Once inside the system, the attackers exploited vulnerabilities in Okta’s security measures to further their access and gain control over user accounts and data. It was found that the attackers targeted weaknesses in Okta’s multi-factor authentication system, bypassing it to gain unauthorized access to user accounts. This demonstrates the importance of regularly updating and patching security systems to mitigate the risk of exploitation.
The attackers also took advantage of misconfigurations in Okta’s systems, leveraging these vulnerabilities to navigate through the infrastructure undetected. This highlights the need for robust security monitoring and proactive threat detection to identify and respond to any anomalous activities.
Furthermore, the attackers utilized advanced malware and malicious scripts to maintain persistence within Okta’s network. These tools allowed them to move laterally across the system, escalating privileges and exfiltrating sensitive data. This emphasizes the importance of deploying effective endpoint protection and intrusion detection systems to detect and prevent such attacks.
In conclusion, the Okta breach serves as a reminder that even the most secure systems can be vulnerable to sophisticated attacks. It emphasizes the need for a proactive security strategy, which includes educating employees, updating systems regularly, monitoring effectively, and having incident response capabilities. This is crucial for safeguarding user data and maintaining the system’s integrity. Okta has since implemented enhanced security measures and learnings from the incident to strengthen their defenses and prevent future breaches.
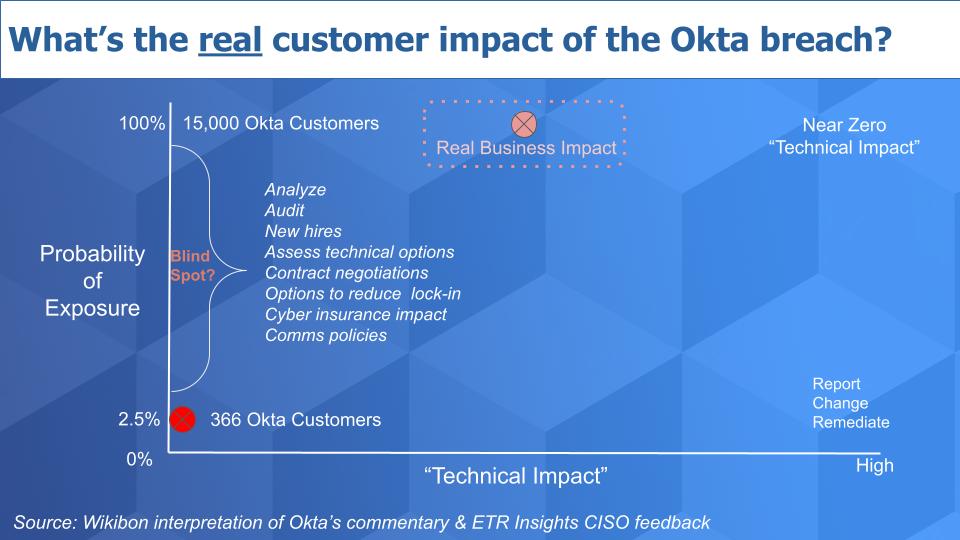
Scope of the Breach
What data was compromised
The Okta breach resulted in the compromise of a significant amount of data, posing a threat to both Okta and its customers. The attackers gained unauthorized access to user accounts and sensitive information, including usernames, passwords, and personal details. The breach could expose customers’ private information to criminals and put them at risk of identity theft and fraud. The compromised data could also be used in targeted phishing campaigns or sold on the dark web, further perpetuating the potential harm to individuals and organizations affected by the breach.
Impact on Okta’s customers
The Okta breach had far-reaching implications for Okta’s customers. With unauthorized access to user accounts, the attackers could impersonate legitimate users, gaining access to their systems and confidential information. This posed a significant risk to customer organizations, as sensitive data and intellectual property could be compromised.
Furthermore, the breach had negative repercussions for customer trust and confidence in Okta’s security measures. Customers, who rely on Okta’s services for secure access management, may have concerns about the effectiveness of the platform in protecting their sensitive data. Relying only on a third-party service provider for access control and user authentication can be risky, as shown by the breach.
In response to the breach, Okta implemented enhanced security measures and collaborated with affected customers to mitigate the impact. They provided guidance on password resets, urged users to enable multi-factor authentication, and offered resources for increased security awareness and education. Despite these efforts, the breach served as a wake-up call for users and organizations alike, emphasizing the need for vigilant cybersecurity practices and proactive measures to prevent future breaches.

Response and Mitigation
Okta’s immediate response to the breach
Okta took immediate action upon discovering the breach to minimize the impact on its customers and protect their sensitive data. The company quickly started investigating the breach to find out how big it was and what weaknesses the attackers took advantage of. They worked closely with cybersecurity experts to analyze the attack and gather valuable insights to enhance their security measures.
As part of their response, Okta notified affected customers about the breach and provided transparent updates on the situation. They provided information about the stolen data, such as usernames, passwords, and personal details, and advised users to change their passwords as a precaution. Okta also provided guidance on enabling multi-factor authentication to add an extra layer of security to user accounts.
Steps taken to prevent future attacks
To prevent future attacks and enhance their security posture, Okta implemented several measures following the breach. They conducted a comprehensive security audit, identifying and addressing any vulnerabilities or weaknesses in their systems. Okta also enhanced their monitoring capabilities to detect and respond to potential threats more effectively.
Additionally, Okta collaborated closely with affected customers to assist with their security measures. They provided resources and guidance on improving security awareness and education. Okta emphasized the importance of regular password changes, strong password complexity, and recommended the use of password managers to mitigate the risk of compromised accounts. They also advised customers to update their security policies, enforce strict access controls, and regularly review and monitor user access permissions.
Okta recognized that cybersecurity is an ongoing effort and committed to continuously investing in the improvement of their security protocols. By bolstering their defenses and fostering a proactive security culture, they aim to prevent future breaches and maintain the trust and confidence of their customers.
Investigation and Attribution
Efforts to identify the perpetrators
Following the breach, Okta immediately launched an extensive investigation to identify the perpetrators behind the attack. The company employed a team of cybersecurity experts who diligently analyzed the breach and its associated vulnerabilities. By thoroughly scrutinizing the findings, Okta aimed to gain a better understanding of the attack methodology and the potential motives of the attackers.
Okta’s investigative team worked diligently to trace the origin of the breach and gather evidence that could aid in the attribution process. They analyzed different signs of wrongdoing, like IP addresses, samples of malware, and attack patterns to create a complete profile of the people responsible. By combining digital forensics and threat intelligence techniques, Okta aimed to uncover the individuals or groups responsible for the breach.
Collaboration with law enforcement agencies
Apart from their internal investigation, Okta recognized the significance of involving law enforcement agencies to hold the perpetrators accountable. The company worked closely with law enforcement agencies at local, national, and international levels to share important information and cooperate in the pursuit of justice.
By partnering with law enforcement, Okta aimed to leverage their expertise and resources to identify, track, and apprehend the attackers. The collaboration was not only to punish the wrongdoers but also to prevent future attacks.
Through their joint efforts, Okta and law enforcement agencies demonstrated their commitment to combating cybercrime and protecting the integrity of online platforms. By working hand in hand, they aimed to restore trust, instill confidence, and create a safer digital environment for individuals and organizations alike.

Lessons Learned
Key takeaways from the Okta breach
The Okta breach serves as a wake-up call for organizations across the globe, highlighting the importance of robust cybersecurity measures and incident response protocols. The following are key takeaways from the Okta breach that can help organizations enhance their security posture:
- Swift and comprehensive investigation: Okta’s immediate response, launching an extensive investigation, showcases the significance of quick action in identifying the perpetrators of a breach. Organizations need to have a dedicated team of cybersecurity experts who can analyze the breach and its vulnerabilities to gain a better understanding of the attack methodology.
- Collaboration with law enforcement: Okta’s proactive involvement with law enforcement agencies demonstrates the importance of partnering with external entities to bring the perpetrators of cybercrime to justice. Organizations should actively share information and cooperate with law enforcement agencies to hold attackers accountable.
- Enhanced incident response: The Okta breach highlights the value of a well-prepared incident response plan. Organizations must have clear protocols in place to detect and respond to breaches effectively. This includes utilizing digital forensics and threat intelligence techniques, as well as having a strong partnership with cybersecurity experts.
- Prioritizing cybersecurity: The Okta breach underscores the importance of prioritizing cybersecurity in organizations. It is crucial to invest in robust security measures, including multi-factor authentication, encryption, and regular security audits. Additionally, ongoing employee training and awareness programs can help prevent and mitigate potential breaches.
Prioritizing cybersecurity in organizations
The Okta breach highlights the critical need for organizations of all sizes to prioritize cybersecurity. With the increasing frequency and sophistication of cyberattacks, organizations must take proactive measures to protect their sensitive data and maintain the trust and confidence of their stakeholders.
To prioritize cybersecurity, organizations can:
- Invest in advanced security solutions: Deploying robust security solutions, such as firewalls, intrusion detection systems, and endpoint protection, can help safeguard against potential breaches and detect any suspicious activities.
- Implement multi-factor authentication: Enforcing the use of multi-factor authentication adds an additional layer of security to protect user accounts from unauthorized access.
- Regularly update and patch systems: Keeping software, applications, and operating systems up to date with the latest security patches helps close any vulnerabilities that cybercriminals may exploit.
- Create a culture of cybersecurity: It is important to educate employees about cybersecurity best practices and encourage a culture of vigilance when it comes to protecting sensitive information. Regular training sessions and awareness programs can help employees identify and respond to potential threats effectively.
- Regularly assess and monitor the security posture: Conducting regular security audits and assessments can help identify potential vulnerabilities and gaps in the security infrastructure. Continuous monitoring allows organizations to detect and respond to any suspicious activities promptly.
By prioritizing cybersecurity and implementing these measures, organizations can strengthen their defenses against cyberattacks and minimize the risk of breaches like the Okta incident.

Industry Implications
Impact of the Okta breach on the cybersecurity landscape
The Okta breach sent shockwaves through the cybersecurity landscape, highlighting the ever-present threat of cyberattacks and the need for organizations to continually strengthen their defenses. This attack provided valuable insights into the tactics and techniques deployed by cybercriminals, leading to important lessons for the industry.
One of the significant implications of the Okta breach is the recognition that even organizations known for their robust security measures can fall victim to sophisticated attacks. It serves as a reminder that no company is immune to cyber threats, regardless of their size or reputation. This event underscores the critical importance of remaining vigilant and continuously improving security practices.
The breach also exposed the potential vulnerability of authentication systems. Okta, a leader in identity and access management, experienced a breach that compromised user credentials. This highlights the need for organizations to adopt multi-faceted authentication methods, such as biometrics or hardware tokens, to enhance security.
Relevant regulations and compliance measures
The Okta breach has several implications for regulatory compliance. Organizations may face consequences if they fail to protect sensitive customer data adequately. Regulations like GDPR and CCPA are extremely important after a major breach.
To mitigate the risk of regulatory penalties and reputational damage, organizations must adhere to industry-specific regulations and implement robust cybersecurity measures. Regularly check security and ensure data protection rules are followed. Report any breaches to the relevant authorities and affected individuals.
Furthermore, the Okta breach serves as a wake-up call for organizations to reassess their incident response plans and capabilities. By aligning their strategies with recognized frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework, organizations can better prepare for and respond to potential breaches.
In conclusion, the Okta breach has significant industry implications, highlighting the need for continuous improvement in cybersecurity practices and compliance measures. By learning from this incident, organizations can bolster their defenses and protect themselves and their customers from future cyber threats.
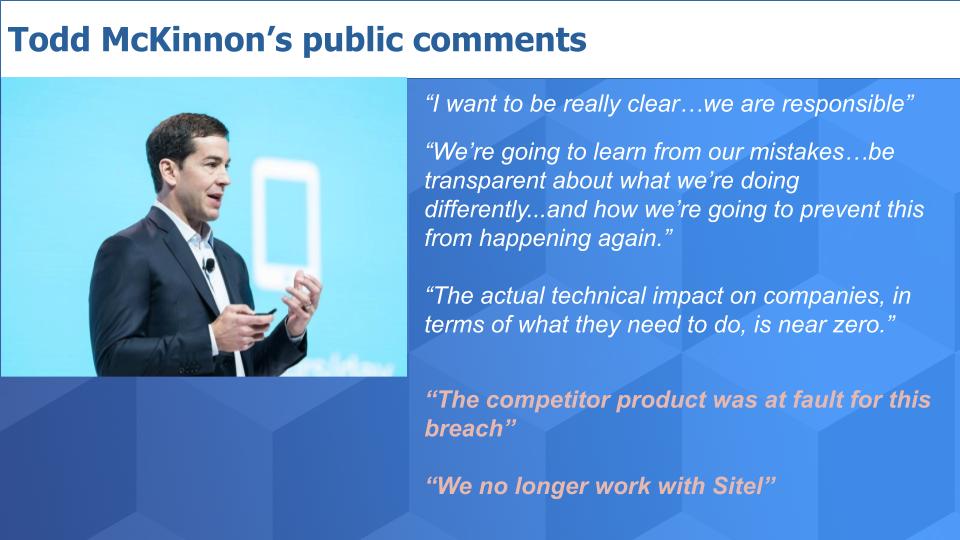
Conclusion
The Okta breach has left a lasting impact on the cybersecurity landscape, revealing vulnerabilities in even well-established security systems and emphasizing the importance of continuous improvement in security practices. Organizations must take heed of the lessons learned from this attack to enhance their defenses and ensure compliance with relevant regulations.
Summary of the Okta Breach and Its Aftermath
The Okta breach highlighted the ever-present threat of cyberattacks, showcasing that even organizations known for their robust security measures can fall victim to sophisticated attacks. The breach compromised user credentials, underscoring the vulnerability of authentication systems. In the aftermath, organizations must reassess their incident response plans and capabilities.
Relevant regulations and compliance measures become even more crucial post-breach. Failure to adequately protect sensitive customer data may result in severe consequences, emphasizing the need for adherence to regulations such as GDPR and CCPA. Organizations must conduct regular security audits, implement data protection policies, and promptly disclose breaches to authorities and affected individuals.
Recommendations for Organizations to Enhance Security Measures
To enhance security measures and prevent future breaches, organizations should consider adopting multi-faceted authentication methods, such as biometrics or hardware tokens, to mitigate the risk of credential compromise. Additionally, aligning incident response plans with recognized frameworks like NIST Cybersecurity Framework can help organizations better prepare for and respond to potential breaches.
Regular training and education for employees on cybersecurity best practices are crucial, as human error is often a weak point in security defenses. By investing in employee awareness and providing continuous education, organizations can improve their overall security posture.
In conclusion, the Okta breach serves as a wake-up call for organizations to prioritize cybersecurity and compliance measures. By implementing the recommended enhancements and learning from this incident, organizations can fortify their defenses and protect both themselves and their customers from future cyber threats.




