Introduction to PASTA Threat Model Framework
Overview of PASTA Threat Model Framework
The PASTA Threat Model Framework (Process for Attack Simulation and Threat Analysis) is a comprehensive and scalable methodology for application threat modeling. Its goal is to enhance an application’s security posture by identifying and addressing potential threats early in the development cycle.
Key Features of PASTA:
- Risk-Centric Approach: PASTA focuses on understanding risks from an attacker’s perspective.
- Structured Seven-Step Process: Ensures thorough examination and evaluation of threats.
- Scalability: Adaptable to various applications and organizational needs.
By integrating PASTA, organizations can proactively identify vulnerabilities and develop mitigation strategies, ensuring a robust defense against security threats. This methodology aligns seamlessly with modern development practices, making it a vital tool in the cybersecurity arsenal.

Key Components of PASTA Threat Model Framework
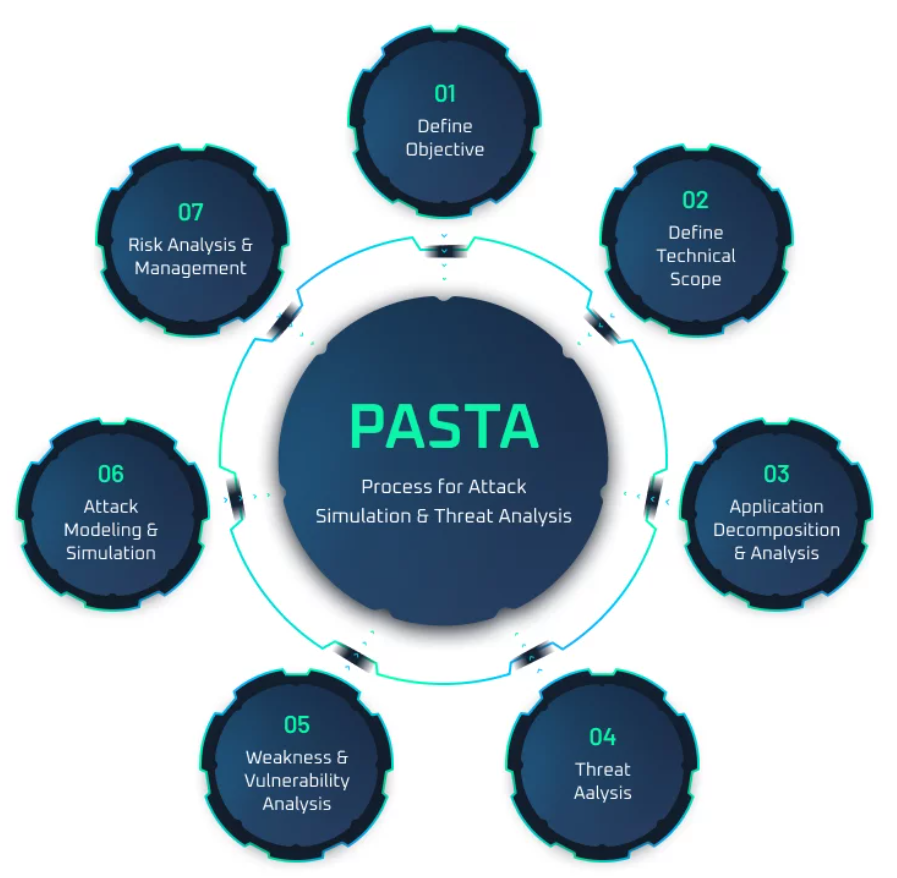
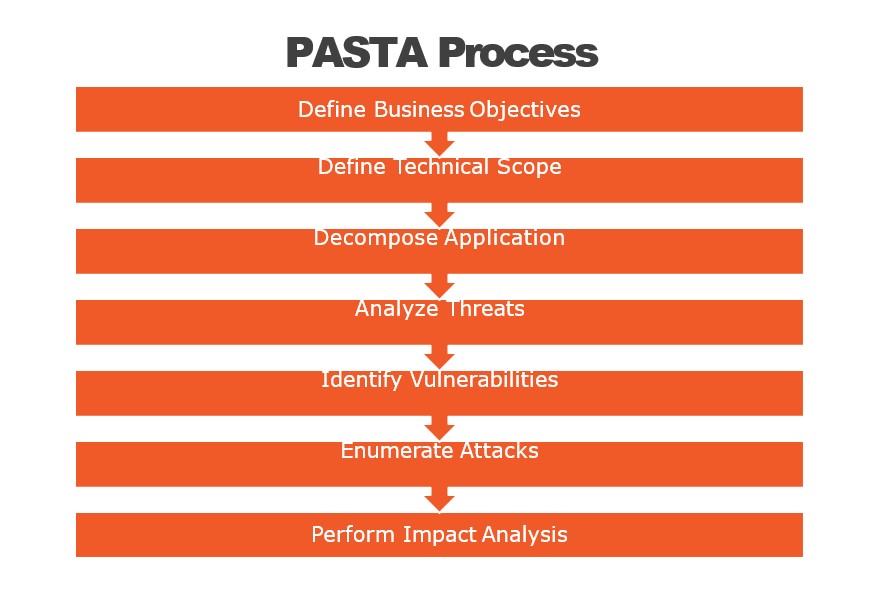
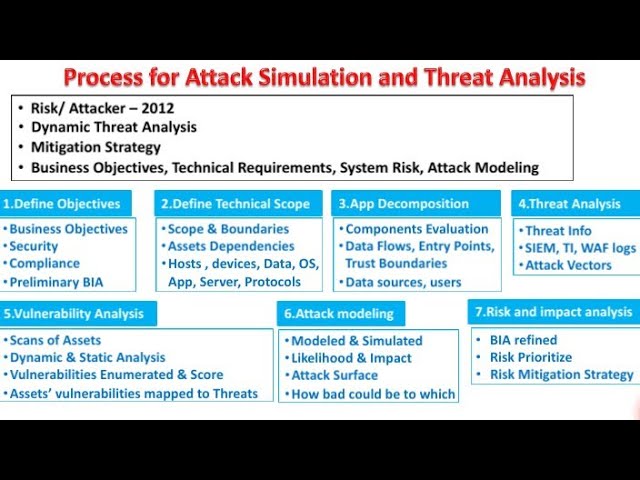
Transitioning from the overview, it’s essential to delve into the key components that make the PASTA Threat Model Framework robust and effective. This seven-step process guides teams through detailed threat identification and mitigation.
Core Components of PASTA:
- Stage 1: Definition of Business Objectives: Aligns security goals with business goals.
- Stage 2: Definition of Technical Scope: Defines the technology stack and boundaries.
- Stage 3: Application Decomposition: Breaks down applications to understand data flow and interactions.
- Stage 4: Threat Analysis: Identifies potential threats and vulnerabilities.
- Stage 5: Weakness and Vulnerability Analysis: Explores weaknesses within the system.
- Stage 6: Attack Modeling and Simulation: Emulates potential attack vectors.
- Stage 7: Risk & Impact Analysis: Assesses the risks and impact of identified threats.
By comprehensively covering these steps, PASTA ensures a structured and thorough approach to threat modeling, preparing organizations to effectively address and mitigate a wide range of security challenges.
Understanding Threat Modeling in PASTA
Benefits of Threat Modeling in PASTA
Building on the key components, understanding the benefits of using the PASTA Threat Model Framework underscores its value in cybersecurity.
Advantages of Threat Modeling with PASTA:
- Proactive Risk Management: Identifies and addresses vulnerabilities early in the development cycle.
- Enhanced Security Posture: Ensures comprehensive coverage of potential threat vectors.
- Efficient Resource Allocation: Focuses security efforts on the most critical areas.
- Informed Decision-Making: Provides detailed insights for stakeholders to make informed security decisions.
- Compliance and Standards Alignment: Helps meet regulatory and industry standards by ensuring thorough security practices.
- Improved Communication: Facilitates better understanding and collaboration among cross-functional teams.
By leveraging these benefits, organizations can enhance their security readiness and resilience, effectively mitigating risks and safeguarding their digital assets against evolving threats. PASTA’s structured approach ensures that threat modeling is not just reactive but an integral part of the development lifecycle.
PASTA Threat Intelligence Gathering
Role of Threat Intelligence in PASTA
Transitioning from the steps involved in threat modeling with PASTA, the role of threat intelligence is paramount. Threat intelligence enriches the framework by providing actionable insights into potential and emerging threats.
Key Contributions of Threat Intelligence:
- Enhanced Threat Analysis: Offers up-to-date information on new vulnerabilities and attack techniques.
- Contextual Relevance: Helps in understanding the context of threats relevant to the specific application environment.
- Informed Decision-Making: Supports data-driven security decisions by providing concrete threat evidence.
- Proactive Mitigation: Enables timely development of mitigation strategies against identified threats.
- Risk Prioritization: Assists in prioritizing threats based on their significance and potential impact.
By integrating threat intelligence, PASTA strengthens its threat analysis phase, ensuring that potential risks are identified, contextualized, and promptly addressed. This leads to a proactive and dynamic security stance, helping organizations stay ahead of adversaries in an ever-evolving threat landscape.
Threat Intelligence in PASTA
Following the critical role of threat intelligence in PASTA, understanding the methods for gathering this intelligence becomes crucial. Effective threat intelligence collection ensures comprehensive threat coverage and enhances the security framework.
Essential Methods for Gathering Threat Intelligence:
- Open Source Intelligence (OSINT): Utilizes publicly available data from various online resources such as blogs, forums, and social media.
- Commercial Threat Feeds: Subscriptions to premium threat intelligence services providing curated, real-time threat data.
- Collaborative Threat Sharing: Participating in industry-specific ISACs (Information Sharing and Analysis Centers) for shared threat insights.
- Internal Monitoring: Leveraging internal logs and monitoring systems to detect anomalies and potential threats.
- Threat Hunting: Proactively searching for indicators of compromise (IoCs) within the network using advanced analytical tools.
PASTA ensures a comprehensive and robust threat intelligence framework by employing these diverse methods. Gathering intelligence from various sources enables a multi-faceted view of potential threats, leading to more effective threat identification and mitigation strategies. This well-rounded approach is vital for maintaining a proactive security posture.
Applying PASTA Threat Model Framework
The next step involves implementing PASTA in software development based on the methods for gathering threat intelligence. Integrating PASTA within the development lifecycle ensures that security is an integral part of the process, not an afterthought.
Steps to Implement PASTA in Software Development:
- Initiate Early in the Development Lifecycle: Integrate threat modeling from the initial stages to address security concerns proactively.
- Cross-Functional Collaboration: Involve diverse teams, including developers, security experts, and business stakeholders, for holistic insights.
- Regular Threat Assessments: Conduct periodic threat modeling sessions throughout the development cycle to address new threats and vulnerabilities.
- Automate Where Possible: Use automated tools to streamline threat identification and analysis, ensuring consistency and efficiency.
- Continuous Feedback Loop: Maintain a feedback mechanism to refine and enhance threat modeling practices based on new intelligence and findings.
By implementing these steps, PASTA ensures that security considerations are deeply embedded within the software development process. This proactive approach helps in building secure applications from the ground up, minimizing vulnerabilities and enhancing overall security posture.

Integration of PASTA into DevOps Practices
Extending from the implementation of PASTA in software development, it’s crucial to discuss the integration of PASTA into DevOps practices. Integrating security into DevOps—often referred to as DevSecOps—ensures continuous and comprehensive security checks.
Advantages of Integrating PASTA into DevOps:
- Continuous Security: Embeds security checks throughout the development and deployment pipeline.
- Early Detection of Threats: Identifies and mitigates vulnerabilities at each stage of the DevOps cycle.
- Seamless Collaboration: Fosters collaboration between development, operations, and security teams.
- Automation: Integrates automated threat modeling tools to streamline and enhance security processes.
- Enhanced Agility: Ensures that security measures keep pace with rapid development cycles without compromising agility.
Steps for Effective Integration:
- Embed PASTA within CI/CD Pipelines: Implement continuous integration and continuous deployment (CI/CD) mechanisms to automate threat assessments.
- Use Security as Code: Utilize Infrastructure as Code (IaC) frameworks to enforce security policies automatically.
- Training and Awareness: Provide regular training for DevOps teams on threat modeling and security practices.
- Metric Tracking: Monitor and measure security metrics to assess the effectiveness of threat modeling efforts.
By integrating PASTA into DevOps practices, organizations can achieve a balanced approach where rapid development and robust security coexist. This proactive integration ensures resilient applications capable of withstanding evolving cyber threats.
Mitigation Strategies in PASTA
Effective Strategies for Mitigating Threats in PASTA
Following the discussion on integrating PASTA into DevOps practices, it’s pivotal to delve into effective strategies for mitigating threats identified through the PASTA framework. Mitigation strategies are central to transforming threat intelligence into protective measures.
Key Strategies for Threat Mitigation:
- Prioritization of Threats: Focus on the most critical and high-risk threats to allocate resources efficiently.
- Defense in Depth: Implement multiple layers of security measures to protect against a variety of attack vectors.
- Secure Development Practices: Adopt secure coding guidelines and perform regular code reviews to prevent vulnerabilities.
- Regular Patching and Updates: Ensure that all software components are up-to-date with the latest security patches.
- Intrusion Detection and Prevention Systems (IDPS): Employ IDPS to monitor, detect, and respond to malicious activities in real-time.
- User Training and Awareness: Conduct regular training sessions to educate users and developers about evolving threats and security best practices.
Organizations can significantly reduce the risk of successful attacks by adopting these effective strategies. The comprehensive approach provided by PASTA ensures that vulnerabilities are not just identified but actively mitigated, thereby enhancing the organisation’s overall security posture and resilience.
Risk Assessment and Management in PASTA
Building on effective strategies for mitigating threats, risk assessment and management are critical components of the PASTA framework. Proper risk assessment ensures that potential threats are evaluated and managed to protect organizational assets.
Steps in Risk Assessment and Management:
- Identify and Categorize Risks: Recognize and classify potential risks based on severity and impact.
- Evaluate Risk Impact: Assess the potential impact of each identified risk on the organization.
- Determine Likelihood: Estimate the probability of each risk occurring.
- Prioritize Risks: Focus on high-impact, high-likelihood risks for targeted mitigation efforts.
- Implement Risk Mitigation Strategies: Develop and apply appropriate mitigation strategies to minimize potential risks.
- Continuous Monitoring: Regularly review and monitor risks to adapt and respond to emerging threats.
Benefits of Robust Risk Management:
- Proactive Threat Mitigation: Reduces the chance of security breaches and data loss.
- Resource Allocation: Directs resources toward managing the most significant risks effectively.
- Compliance: Ensures alignment with industry standards and regulatory requirements.
- Business Resilience: Enhances the organization’s ability to withstand and recover from security incidents.
By embedding risk assessment and management within the PASTA framework, organizations can systematically evaluate and address risks, ensuring a resilient and secure technological environment.
Conclusion
Advantages of Using PASTA Threat Model Framework
Following the detailed exploration of risk assessment and management, it is vital to highlight the advantages of using the PASTA Threat Model Framework. PASTA offers a myriad of benefits that enhance an organization’s security and resilience.
Key Advantages of PASTA:
- Comprehensive Analysis: Provides a structured, seven-step process for thorough threat identification and mitigation.
- Alignment with Business Goals: Ensures that security measures reflect the organization’s objectives and risk appetite.
- Proactive Threat Management: Identifies and addresses threats early in the development cycle, reducing the potential for vulnerabilities.
- Contextual Threat Understanding: Utilizes threat intelligence to offer an up-to-date and relevant understanding of potential attacks.
- Scalability: Adaptable to various environments and application scopes, making it suitable for organizations of all sizes.
- Enhanced Collaboration: Facilitates better communication and cooperation among cross-functional teams, including developers, security experts, and business stakeholders.
By integrating these advantages, organizations can leverage PASTA to build a robust defense against security threats. The comprehensive and proactive nature of the PASTA framework ensures an enhanced security posture, safeguarding digital assets and promoting business resilience.
Ensuring Security with PASTA
Building on the advantages of using the PASTA framework, adhering to best practices ensures its effective application and maximizes security benefits. Implementing these practices helps maintain a proactive and resilient security posture.
Best Practices for Ensuring Security:
- Start Early: Incorporate threat modeling from the initial stages of the development lifecycle to address security concerns proactively.
- Regular Updates: Continuously update threat models to account for new vulnerabilities and emerging threats.
- Comprehensive Training: Educate cross-functional teams on PASTA principles and threat modeling techniques.
- Collaborate Across Teams: Promote strong collaboration between developers, security practitioners, and business stakeholders.
- Utilize Automation: Leverage automated tools to streamline threat detection and analysis processes.
- Continuous Monitoring: Maintain ongoing monitoring and assessment to adapt to the evolving threat landscape.
- Feedback Loop: Implement a feedback mechanism to refine security practices based on insights gained from threat modeling.
By following these best practices, organizations can ensure the effective application of the PASTA framework, leading to robust threat identification and mitigation. This proactive approach secures the development lifecycle and enhances overall organizational security, ensuring resilience against an ever-changing array of threats.