
The Target Data Breach: How Hackers Stole Millions of Customer Records
Reading Time: 9 minutesIntroduction The Target data breach in 2013 sent shockwaves through the retail industry and raised concerns about the...

Infosec and Cybersecurity
Reading Time: 2 minutesUnderstanding Infosec and Cybersecurity Information security, often referred to as infosec, is the practice of protecting digital information...

CIS Controls V8
Reading Time: 2 minutesCIS Controls Version 8 is a cybersecurity framework that provides a recommended set of prioritized cyber defense best...
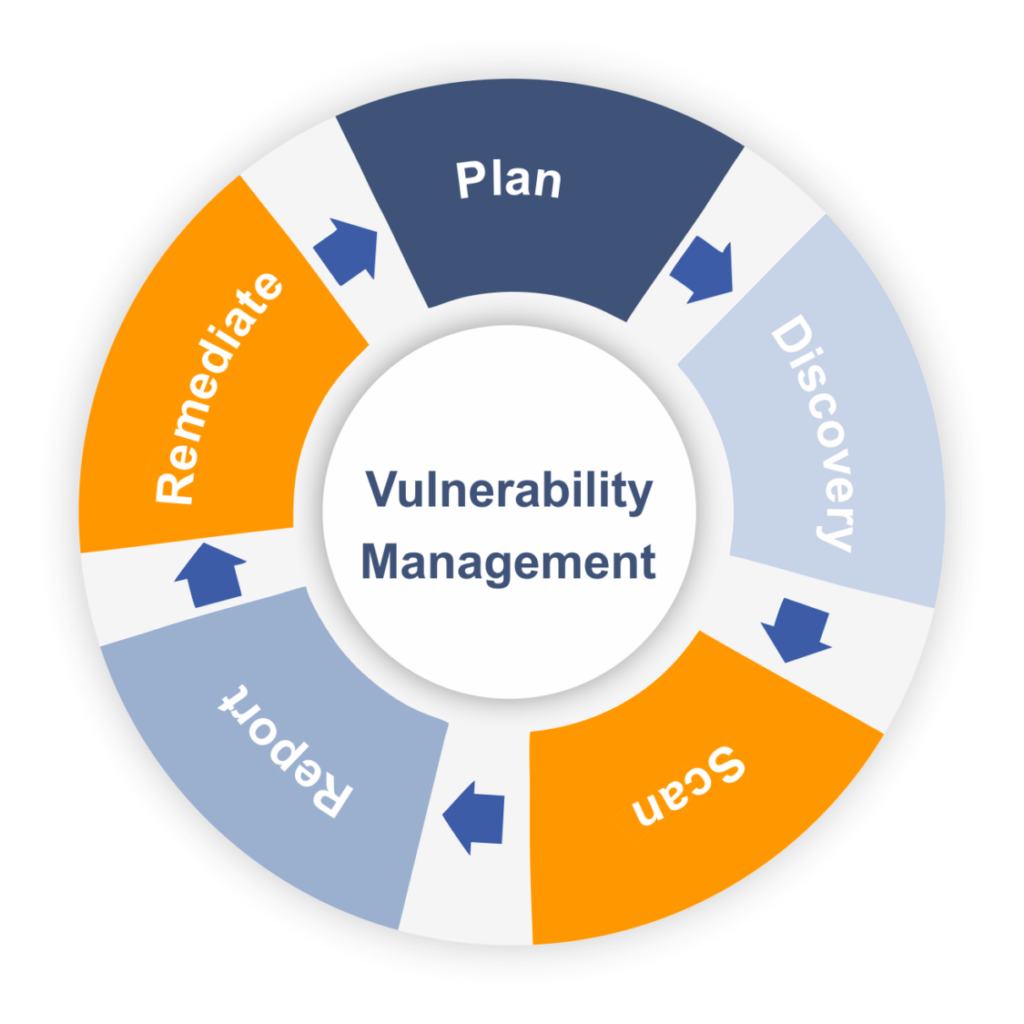
Vulnerability Management
Reading Time: 2 minutes Vulnerability Management is the process of identifying, evaluating, and addressing security vulnerabilities in a system. It encompasses...
