
Building a Culture of Cybersecurity: Strategies for Employee Adoption
Reading Time: 7 minutesImportance of Building a Culture of Cybersecurity In today's digital age, building a culture of cybersecurity is of...

The Colonial Pipeline Cyberattack
Reading Time: 12 minutesOverview of the Colonial Pipeline Cyber Attack The Colonial Pipeline cyberattack was a big event that affected the...

CNA Financial Hit by $40M Ransomware Attack: What We Need to Know
Reading Time: 8 minutesIntroduction CNA Financial, a top US insurance company, was recently targeted by a major ransomware attack. The company...

Wannacry: The Cyber Attack That Shook the World
Reading Time: 10 minutesOverview of the Wannacry Cyberattack The Wannacry cyberattack occurred in May 2017 and targeted computers running the Microsoft...

Infosec and Cybersecurity
Reading Time: 2 minutesUnderstanding Infosec and Cybersecurity Information security, often referred to as infosec, is the practice of protecting digital information...

CIS Controls V8
Reading Time: 2 minutesCIS Controls Version 8 is a cybersecurity framework that provides a recommended set of prioritized cyber defense best...
Ransomware
Reading Time: 11 minutesRansomware attacks have become increasingly prevalent in today’s digital landscape, posing a significant threat to individuals and businesses....
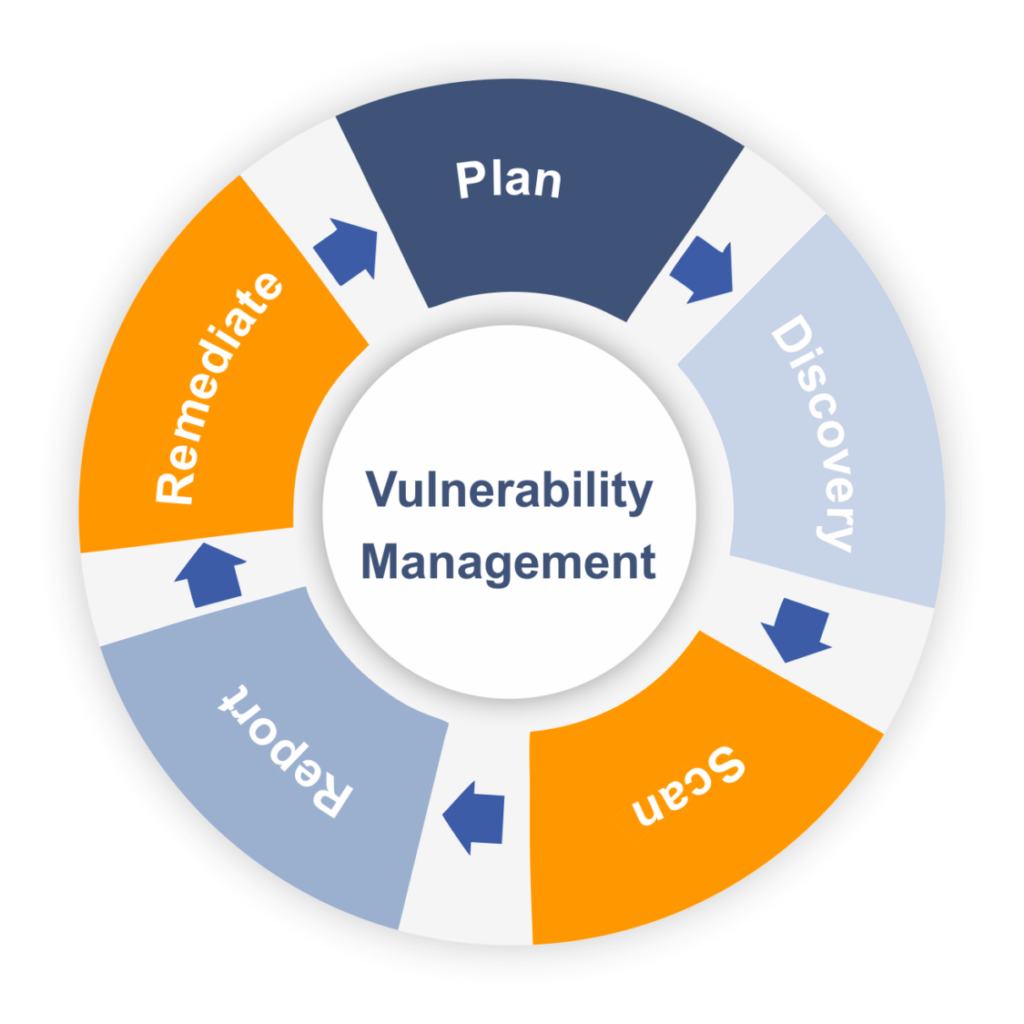
Vulnerability Management
Reading Time: 2 minutes Vulnerability Management is the process of identifying, evaluating, and addressing security vulnerabilities in a system. It encompasses...

Password Managers
Reading Time: 8 minutesA password manager is a tool that helps users securely store and manage their passwords. It is designed...
