Overview of the Colonial Pipeline Cyber Attack

The Colonial Pipeline cyberattack was a big event that affected the nation and raised awareness about the weaknesses of important infrastructure. In May 2021, the Colonial Pipeline, which provides almost half of the fuel used on the East Coast of the United States, was targeted in a ransomware attack. This attack disrupted the operation of the pipeline for several days, causing fuel shortages and panic among consumers. The incident showed how important cybersecurity is for protecting important systems and raised worries about the potential impact of future cybCyberattackerattacks on essential infrastructure.
What is the Colonial Pipeline?

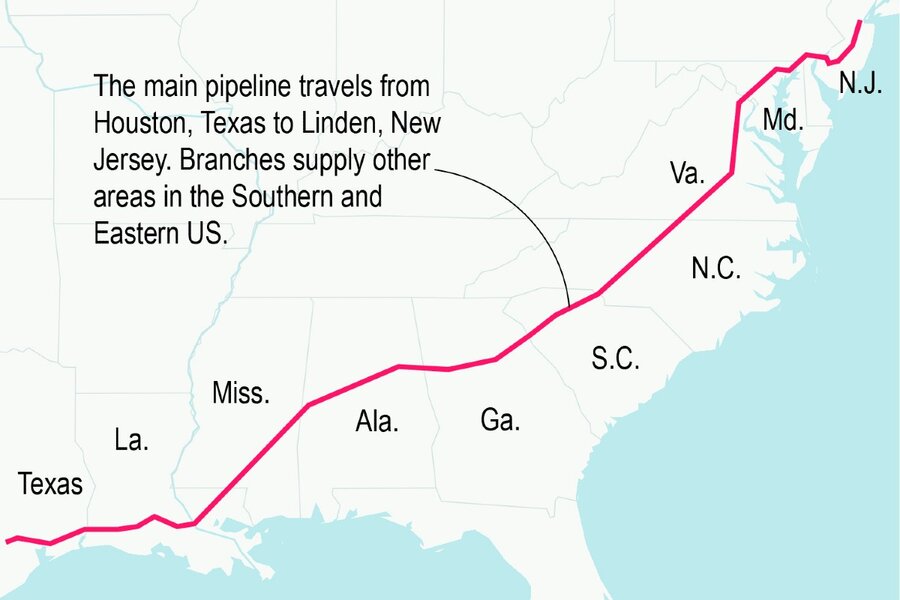
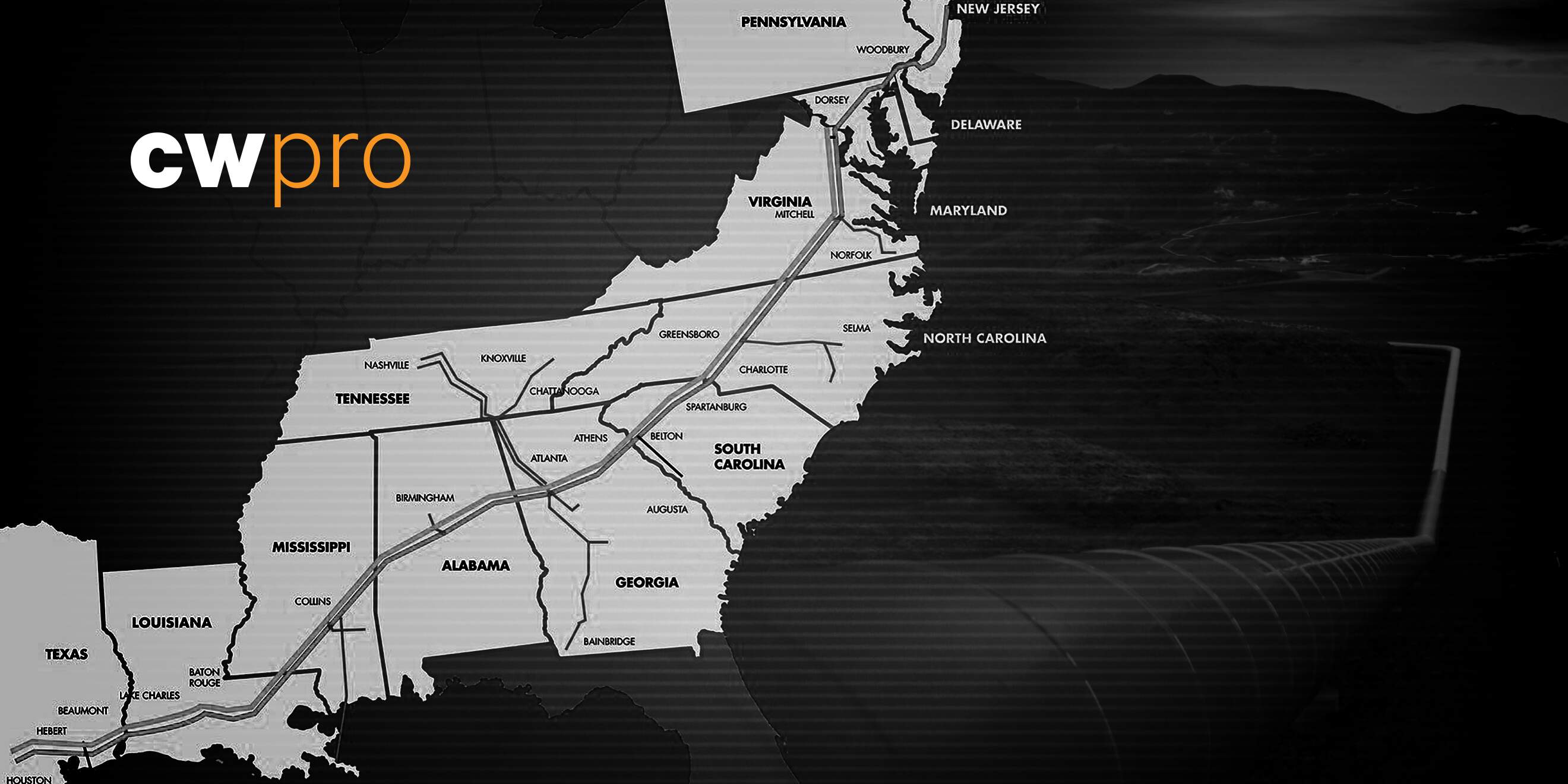
The Colonial Pipeline is one of the largest fuel pipeline systems in the United States. Stretching over 5,500 miles, it connects refineries on the Gulf Coast to major metropolitan areas along the Eastern Seaboard. The pipeline transports large amounts of gas, diesel, and jet fuel daily, providing fuel to many states and airports. It is important for providing fuel to transport, industries, and consumers in a large part of the country. The Colonial Pipeline’s vast network and critical infrastructure make it an attractive target for cyberattacks.
Introduction to the Cyberattack
The Colonial Pipeline cyberattack was a significant event that occurred in May 2021. This attack targeted the Colonial Pipeline, which is one of the largest fuel pipeline systems in the United States. The attackers used ransomware, a harmful software that locks data and asks for payment to unlock it. The attack caused widespread disruption to the fuel supply along the East Coast, leading to fuel shortages and price increases. It highlighted the vulnerabilities of critical infrastructure and raised concerns about cybersecurity in various industries.
Timeline of Events
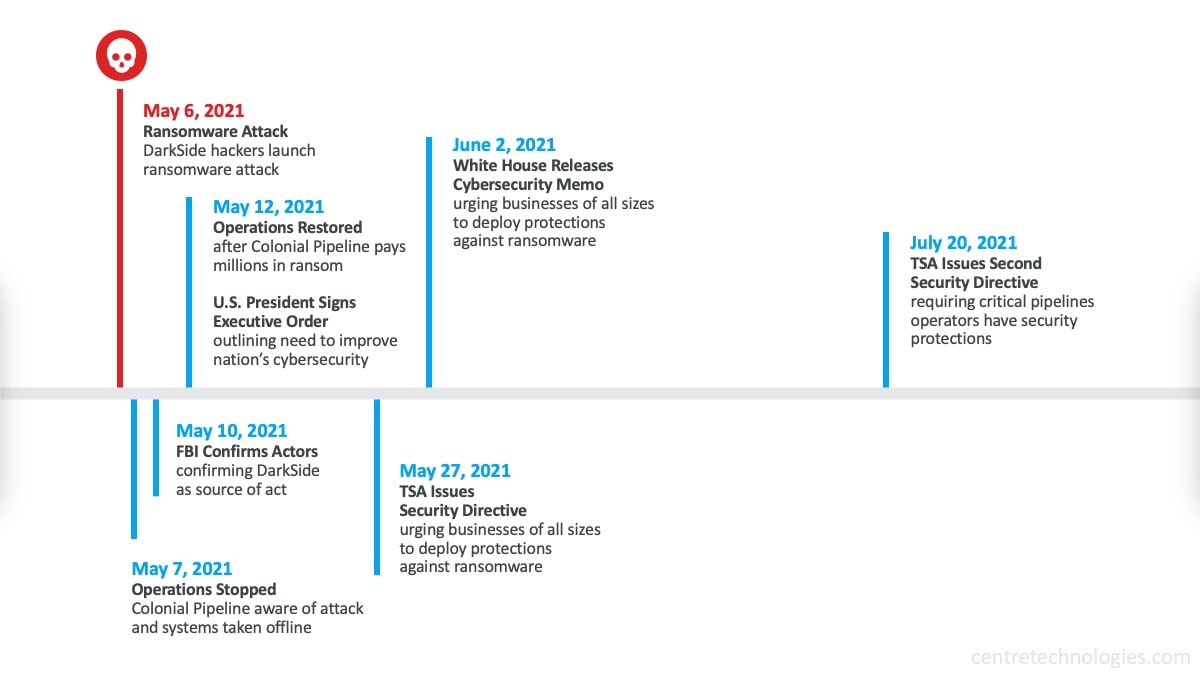
The Colonial Pipeline cyberattack had a big impact on the company and the wider community. It brought forth numerous challenges. On May 7, 2021, Colonial Pipeline found out that its network was hacked with ransomware. This immediately led to a proactive decision to shut down operations as a precautionary measure to prevent further harm. As a result, a major disruption in fuel supply occurred, leading to panic-buying and fuel shortages across several states. The crisis intensified as Colonial Pipeline worked tirelessly to restore operations and mitigate the impact on consumers. Finally, on May 12, Colonial Pipeline announced that it had resumed normal operations and started delivering fuel once again. The timely response and recovery efforts undertaken by the company were crucial in minimizing the duration of the disruption.
Discovery and Impact of the Cyberattack

Following the cyberattack on the Colonial Pipeline, the incident was discovered on May 7th, 2021. The company immediately took action by temporarily shutting down its operations to contain the damage and prevent further infiltration. This attack on one of the biggest fuel pipelines in the United States caused a big impact on fuel supply and distribution in several states. It resulted in panic buying and fuel shortages. The disruption resulted in increased gas prices and affected various industries reliant on transportation, such as airlines and trucking companies. However, despite the initial shock, an optimistic outlook emerged as efforts were made to address the situation promptly and ensure a swift recovery.
Response and Recovery Efforts
In the wake of the Colonial Pipeline cyberattack, swift response and recovery efforts were set into motion. Upon discovering the breach, Colonial Pipeline took immediate steps to halt operations and mitigate further damage. The company worked with federal agencies like the Department of Energy and the FBI to evaluate the attack and create a recovery plan. Colonial Pipeline quickly restored operations, ensuring fuel flow without interruption. The incident made critical infrastructure providers pay more attention to cybersecurity and emergency response to prevent future attacks.
The Hackers and Their Methods

The hackers behind the Colonial Pipeline cyberattack employed sophisticated methods to breach the company’s systems and disrupt its operations. Although their exact identities are still under investigation, experts believe they were part of a professional cybercriminal group. These hackers utilized a combination of social engineering, phishing emails, and network scanning to gain unauthorized access to Colonial Pipeline’s network. Once inside, they deployed ransomware to encrypt the company’s data and demand a hefty ransom for its release. Their methods highlight the growing capabilities and adaptability of cybercriminals, emphasizing the need for robust cybersecurity measures.
Identification of the Hackers
As the investigation into the Colonial Pipeline cyberattack unfolded, efforts were made to identify the hackers responsible for the breach. Experts in cybersecurity and law enforcement agencies collaborated to trace the attack’s source and collect evidence of the individuals responsible. Through extensive forensic analysis and digital surveillance, patterns and indicators pointed towards a cybercriminal group known as DarkSide. This group is believed to operate in Eastern European countries and has a history of targeting organizations for ransomware attacks. The identification of the hackers was a significant step towards holding them accountable for their actions.
Techniques and Tools Used in the Attack

The cyberattack on the Colonial Pipeline utilized a combination of sophisticated techniques and tools to gain unauthorized access to the company’s systems. The hackers employed a blend of social engineering, phishing emails, and malware to breach the pipeline’s network defenses. They leveraged various attack vectors, including compromised accounts and vulnerable software, to exploit weaknesses in the system. Additionally, reports suggest that ransomware was used to encrypt data and demand a ransom payment. This attack highlights the importance of constantly updating security measures and staying vigilant against evolving cyber threats.
Implications and Consequences
The cyberattack on Colonial Pipeline had significant implications and consequences for various stakeholders. Fuel supply disruption caused gasoline shortages, affecting fuel availability and pricing in affected regions. Secondly, the attack had economic ramifications, causing financial losses for Colonial Pipeline and other businesses reliant on their services. Additionally, there were environmental consequences as users turned to alternative fuels with potentially higher carbon emissions. However, this incident serves as a wake-up call for improving cybersecurity measures and strengthening resilience in critical infrastructure.
Disruption of Fuel Supply

The Colonial Pipeline cyberattack had a significant impact on the fuel supply across several states in the United States. As a critical infrastructure, the pipeline provided gasoline, diesel, and jet fuel to a large portion of the East Coast. The attack caused the pipeline to shut down for days, leading to fuel shortages and panic buying in many areas. There were long lines at gas stations, limited fuel for important services like hospitals and emergency vehicles, and people felt uncertain. Efforts were made to alleviate the situation by implementing emergency measures and seeking alternative methods of fuel transportation, but it took time for the situation to fully stabilize.
Economic and Environmental Impact

The cyberattack on the Colonial Pipeline resulted in substantial economic and environmental consequences. The pipeline shutdown caused fuel transportation issues, resulting in shortages across the United States. This resulted in increased prices at the pump, causing financial strain on individuals and businesses alike.
Furthermore, the disruption in fuel supply had ripple effects on other industries, such as transportation and manufacturing. Delivery delays and production slowdowns occurred as a result, further exacerbating the economic impact.
In terms of the environment, the shutdown of the pipeline had unintended positive consequences. With reduced fuel consumption during the outage, there was a temporary decrease in greenhouse gas emissions and air pollution. This unexpected silver lining showcased the impact that decreased fossil fuel consumption can have on environmental sustainability.
The cyberattack on the Colonial Pipeline has led to significant economic difficulties for a large number of people. However, it also emphasized the need to shift to cleaner energy sources to address climate change and reduce our dependence on vulnerable infrastructure systems.
Investigation and Attribution
The Colonial Pipeline cyberattack triggered an extensive investigation by both law enforcement agencies and government entities. Numerous experts from cybersecurity firms were also involved in identifying the perpetrators. The investigation sought to find out where the attack came from, why it happened, and if it was connected to other cybercriminal networks. Through advanced forensic techniques and intelligence gathering, investigators were able to attribute the attack to a specific group or individuals. Successful attribution of the cyberattack is crucial for holding the responsible parties accountable and preventing future incidents.
Law Enforcement and Government Involvement

Law enforcement agencies and the government played a crucial role in responding to the Colonial Pipeline cyberattack. Once the attack was found, the FBI and the Department of Homeland Security were notified and started an investigation. The government declared a state of emergency to provide resources and support to lessen the effects of the fuel supply attack. Working together was crucial in finding the hackers and responding to prevent more damage. Their involvement demonstrated a commitment to protecting critical infrastructure and ensuring the safety and security of the nation’s energy system.
Attribution of the Cyberattack

The identification of those responsible for the Colonial Pipeline cyberattack was crucial in holding them accountable. Authorities and experts have been working hard to track down the source of the attack and identify the responsible party. This involved analyzing technical indicators, patterns of behavior, and gathering intelligence from various sources. The collaborative efforts eventually led to the identification of the hacker group known as DarkSide as the primary perpetrators of the attack. Their identity was confirmed using digital forensics and intelligence analysis, uncovering more about their motivations and methods. With this information, law enforcement agencies can take appropriate action and prevent further attacks from occurring in the future.
Cybersecurity Measures and Vulnerabilities
Colonial Pipeline, like many other organizations, had implemented cybersecurity measures to protect its systems and data. These measures included firewalls, intrusion detection systems, and employee training programs on cybersecurity best practices. However, despite these efforts, vulnerabilities still existed within the company’s network. This attack highlighted the need for constant monitoring and updating of security systems to stay ahead of evolving threats. It also emphasized the importance of regularly reviewing and patching any vulnerabilities to prevent unauthorized access to critical infrastructure. The incident served as a wakeup call for both Colonial Pipeline and other organizations to prioritize cybersecurity as a fundamental aspect of their operations.
Colonial Pipeline’s Security Measures
Colonial Pipeline has strong security measures to protect its fuel pipeline network from cyber threats in the US. The company invested in advanced cybersecurity technology and has a dedicated team of experts to monitor and respond to potential breaches. They have implemented firewalls, intrusion detection systems, and encryption protocols to safeguard their systems and data. Regular assessments and audits are conducted to ensure compliance with industry standards and identify any vulnerabilities. Colonial Pipeline is committed to security and takes a proactive approach to protect critical infrastructure and ensure a steady fuel supply for the nation.
Lessons Learned and Recommendations

The Colonial Pipeline cyberattack served as a wake-up call for critical infrastructure operators and cybersecurity professionals worldwide. It highlighted the need for improved security measures and proactive defense strategies.
Regularly updating and patching software systems is important to prevent vulnerabilities that hackers can exploit. Additionally, organizations should implement multi-factor authentication and strong password policies to safeguard their networks.
Furthermore, it is crucial for all stakeholders to prioritize cybersecurity awareness training for employees and maintain effective incident response plans. Regular audits and penetration testing can help identify any weaknesses in the system, allowing for timely remediation.
In light of the Colonial Pipeline cyber attack, it is essential that both private companies and government agencies collaborate closely to share threat intelligence and best practices. This level of collaboration can strengthen defenses against future attacks.
Ultimately, the lessons learned from this incident should serve as a catalyst for organizations to invest in robust cybersecurity measures and stay ahead of evolving cyber threats. By implementing these recommendations, we can collectively build a more resilient and secure digital landscape.
The Role of Ransomware
Ransomware has become an increasingly prevalent and destructive tool in the hands of cybercriminals. The Colonial Pipeline cyberattack highlights the role of ransomware as a primary method of extortion and disruption. IThe hackers in this attack used ransomware to lock the company’s data and asked for a large payment to unlock it. Ransomware not only denies access to critical systems and information, but it also instigates fear, financial loss, and reputation damage. This event serves as a stark reminder of the urgent need to fortify cybersecurity defenses against this malicious software.
Definition and Types of Ransomware

Ransomware is a harmful program that locks files or systems until a ransom is paid.It works by exploiting vulnerabilities in computer systems, often through phishing emails or malicious downloads. There are different types of ransomware, including encrypting ransomware and locker ransomware. Encrypting ransomware encrypts the victim’s files, making them inaccessible until a decryption key is provided upon payment. Locker ransomware, on the other hand, locks the victim out of their system completely. It is important to understand these types of ransomware to better protect against such cyberattacks.
Ransomware’s Connection to the Cyberattack
Ransomware played a pivotal role in the Colonial Pipeline cyberattack. This malicious software infiltrated the company’s systems, encrypting critical data and demanding a ransom payment in exchange for its release. The hackers behind the attack utilized a specific strain of ransomware known as DarkSide, which is designed to target large organizations and extort money from them. The connection between the cyberattack and ransomware highlights the increasing sophistication of these types of attacks and the need for organizations to prioritize cybersecurity measures to mitigate such threats in the future.
Similar Cyberattacks and their Significance
The Colonial Pipeline cyberattack is not an isolated incident in the world of cybersecurity. Over the years, there have been several similar cyberattacks targeting critical infrastructure, highlighting the vulnerability of these systems. The 2015 Ukraine power grid attack and the 2017 NotPetya malware outbreak were reminders of the possible consequences. These attacks disrupted essential services and caused significant financial losses. The significance lies in understanding the lessons learned from these incidents and implementing measures to strengthen cybersecurity defenses across all critical infrastructure sectors.
Other Major Cyberattacks on Critical Infrastructure
Other major cyberattacks on critical infrastructure have highlighted the vulnerability of key systems and industries. For instance, in 2015, Ukraine experienced a sophisticated attack on its power grid, leaving thousands without electricity. The attack demonstrated the potential consequences of targeting critical infrastructure. In 2017, the NotPetya malware spread globally, impacting various sectors, including shipping and logistics. These incidents serve as cautionary tales and emphasize the need for robust cybersecurity measures to protect critical infrastructure from similar attacks in the future.
Lessons Learned and Future Preparedness

Looking back on the Colonial Pipeline cyberattack, several crucial lessons have been learned that can help improve future preparedness and resilience. The incident highlighted the critical need for robust cybersecurity measures, regular vulnerability assessments, and comprehensive incident response plans. It also emphasized the importance of effective communication and collaboration among industry stakeholders, government agencies, and law enforcement. Moving forward, organizations must prioritize investing in advanced technologies and training to stay ahead of emerging threats. By learning from this experience, we can proactively strengthen our defenses and minimize the impact of future cyber attacks on critical infrastructure.
Conclusion

In conclusion, the Colonial Pipeline cyberattack serves as a wake-up call for the critical infrastructure sector and organizations worldwide. It highlights the vulnerabilities and potential consequences of a successful cyberattack on vital systems. The incident underscores the need for robust cybersecurity measures, proactive threat intelligence, and effective incident response plans. While the response to the attack was swift, there is still much work to be done to prevent future breaches. By investing in cybersecurity measures and staying vigilant, organizations can mitigate the risks posed by cyber threats and ensure the resilience of their operations.
Recap of the Colonial Pipeline Cyber Attack
The Colonial Pipeline cyberattack was a significant event that shook the United States in 2021. There was a ransomware attack on the largest fuel pipeline in the country, which caused a lot of disruption and fuel shortages on the East Coast. The attack highlighted the vulnerability of critical infrastructure to cyber threats and raised concerns about the growing sophistication of hackers. The incident ultimately prompted increased scrutiny of cybersecurity measures and emphasized the need for organizations to prioritize robust defenses against such attacks in order to protect essential services and ensure public safety.
Key Takeaways and Recommendations for Prevention
The Colonial Pipeline cyberattack serves as a stark reminder of the vulnerabilities present in critical infrastructure systems. This incident highlighted the need for organizations to prioritize cybersecurity measures and develop robust defense mechanisms against potential threats.
The key takeaway from this cyberattack is the significance of implementing proactive security measures. It is imperative for organizations to regularly update and patch their software, conduct thorough vulnerability assessments, and employ multi-factor authentication to protect sensitive data. Additionally, fostering a culture of cybersecurity awareness among employees through training programs can mitigate the risk of successful attacks.
Furthermore, collaborating with industry experts and sharing threat intelligence can enhance the collective defense against cyber threats. Organizations should also have an incident response plan in place to effectively respond to and recover from potential cyberattacks.
To prevent similar incidents in the future, continuous monitoring of networks and systems is crucial. Employing technologies such as intrusion detection systems (IDS) and security information and event management (SIEM) solutions can help in early detection of any suspicious activities.
It is also important for organizations to conduct regular backups of critical data and maintain offline copies to mitigate the impact of ransomware attacks. Implementing effective backup strategies can aid in restoring systems quickly without yielding to attackers’ demands.
Overall, while incidents like the Colonial Pipeline cyberattack may be alarming, they provide valuable insights for improving cybersecurity practices. By establishing a proactive approach towards prevention and response, organizations can better protect themselves against ever-evolving cyber threats.




