
Understanding the Essentials 8 Cybersecurity Framework
Overview of the Essentials 8 Cybersecurity Framework
In the digital age, cybersecurity is a pivotal aspect of any organization’s defense mechanism. The Essentials 8 Cybersecurity Framework emerges as a strategic model designed to bolster an organization’s resilience against cyber threats. Developed by cybersecurity experts, this comprehensive framework outlines a series of tactical measures and protocols aimed at mitigating cyber risks. It provides a structured approach for organizations to assess and enhance their security posture, ensuring they are better prepared to face the evolving landscape of cyber threats. Adoption of this framework signifies an organization’s commitment to maintaining strong cybersecurity defenses and showcases their proactive stance in securing information assets.
Key objectives and principles of the Essentials 8 Cybersecurity Framework
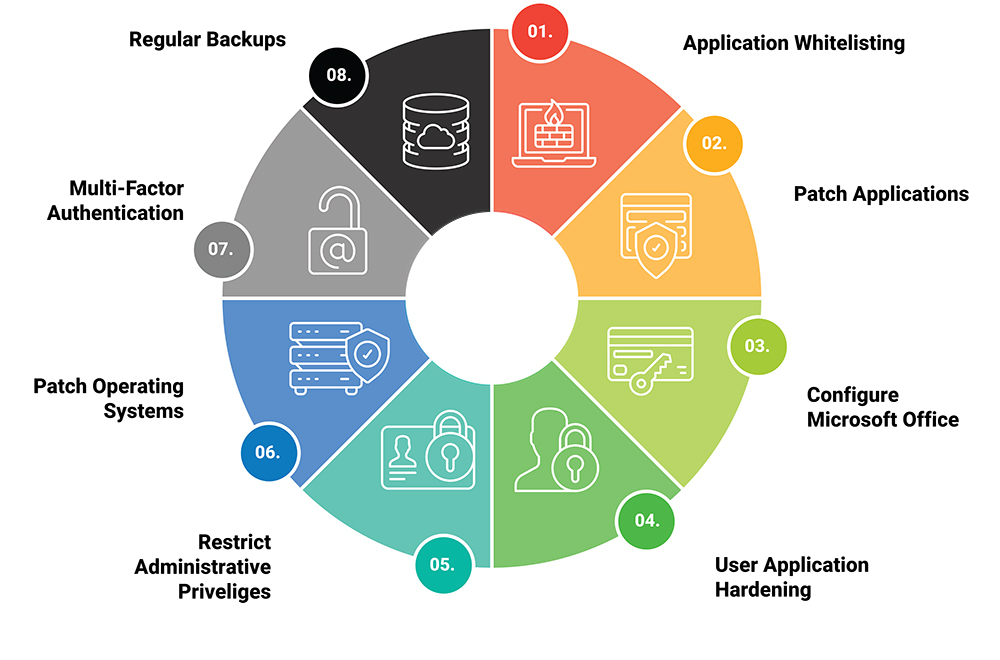
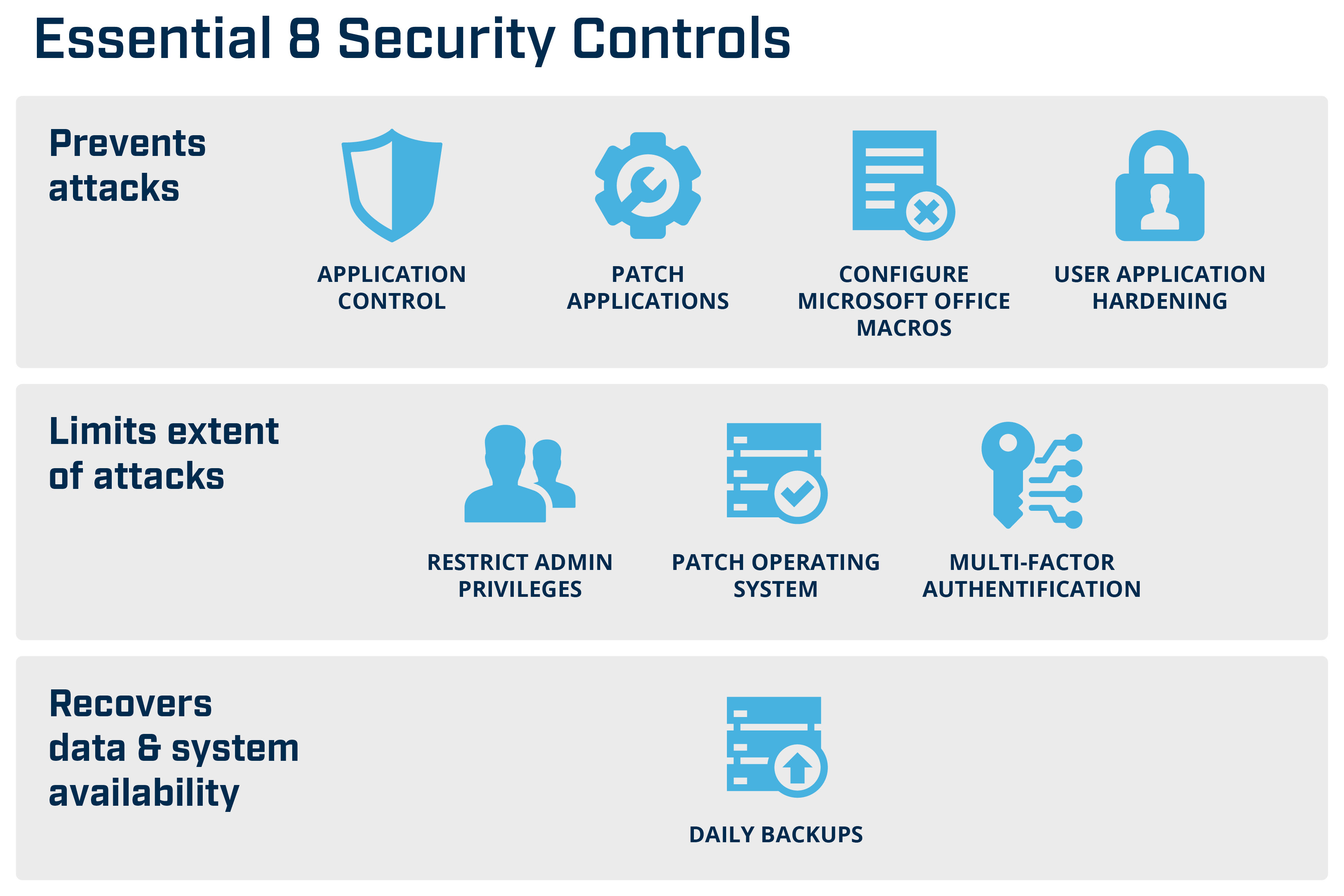
The principal objective of the Essentials 8 Cybersecurity Framework is to establish a robust foundation for cybersecurity practices within organizations. It emphasizes implementing critical security controls that are practical, actionable, and effective in minimizing potential cyber risks. The principles focus on preventing problems by using application whitelisting, patching applications, restricting administrative privileges, and doing daily backups. These advocated practices work cohesively to create multiple defensive layers against various forms of cyber-attacks or breaches. By adhering to these key objectives and principles, organizations can significantly bolster their cybersecurity framework and protect sensitive data from malicious actors.
The Importance of Cybersecurity for Australian Businesses
Cyber threats facing Australian businesses
Australian businesses, irrespective of size or industry, are constantly under threat from cyber criminals. These threats come in various forms such as malware, phishing attacks, ransomware, and sophisticated state-sponsored cyber espionage. The Essentials 8 Cybersecurity Framework aims to empower Australian organizations with the critical tools and knowledge required to defend against these ubiquitous risks. Companies must constantly update and strengthen their cybersecurity strategies to stay ahead of evolving cybercriminal tactics. Such an effort reduces the vulnerability of critical systems and sensitive data to unauthorized access and exploitation.
Impact of cybersecurity breaches on Australian companies
When Australian companies suffer cybersecurity breaches, the consequences can be severe. Financial losses due to operational downtime, legal fines for non-compliance with data protection regulations, and reputational damage are prominent repercussions that can undermine a company’s viability. Moreover, data breaches can result in the loss of intellectual property and personally identifiable information—assets that are crucial for maintaining competitive advantage and customers’ trust. Implementing the Essentials 8 provides organizations with a defensive architecture designed to not only prevent attacks but also facilitate quick recovery in case of security incidents, thereby minimizing the overall impact on business continuity and integrity.
Governance and Risk Management in Cybersecurity
Role of governance in implementing cybersecurity measures
Strong governance is paramount for Australian businesses aiming to implement effective cybersecurity measures. It involves establishing clear policies, protocols, and responsibilities to ensure that cybersecurity is integrated into the organizational fabric. This includes creating an information security framework aligned with business objectives and compliance requirements. Governance promotes accountability by clearly defining roles and responsibilities for personnel at all levels, from the board of directors to operational staff. This helps create a culture of security within the organization.
Risk management strategies within the Essentials 8 Cybersecurity Framework
Risk management lies at the core of the Essentials 8 Cybersecurity Framework. This strategy involves identifying, assessing, and prioritizing risks to corporate assets and operations. By tailoring the application of the eight essential mitigation strategies—ranging from application whitelisting to daily backup of important data—businesses can build a risk-centric cybersecurity posture. Customization according to specific threats and vulnerabilities enables companies to allocate resources efficiently while offering robust protection against cyber-attacks. Strategies need continuous review and adaptation to manage risks and maintain resilience against evolving threats.

Identity and Access Management
Key components of identity and access management
Identity and Access Management (IAM) systems are essential for controlling user access within organizations. A robust IAM comprises several key elements, including user identification, authentication, authorization, and audit. This ensures that each individual has access only to the resources necessary for their role. The system must also manage identities throughout their lifecycle, from initial provisioning to final deprovisioning. Effective IAM fosters a secure and compliant environment where access is precisely controlled and monitored, minimizing the potential for unauthorized access or breaches.
Benefits of implementing strong identity and access controls
The advantages of deploying stringent identity and access controls are significant. They provide a higher level of security by verifying user identities and enforcing appropriate access privileges. Efficient IAM systems streamline operations by automating user lifecycle management, which results in cost savings and reduced IT workloads. Systems like this help companies comply with regulations by providing clear records and making sure data privacy rules are followed. Ultimately, the adoption of these systems not only enhances overall security posture but also supports operational efficiency.

Data Protection and Privacy
Importance of data protection for Australian businesses
In Australia, the significance of data protection cannot be overstressed for businesses across myriad sectors. With the ever-increasing incidences of cyber-attacks, ensuring the confidentiality, integrity, and availability of information is paramount. The adoption of robust data protection strategies helps in safeguarding sensitive corporate data as well as personal information of customers. This vigilant approach to data security not only safeguards against potential financial losses but also upholds an organization’s reputation. Moreover, customers are increasingly aware and concerned about their data privacy, hence businesses prioritizing data protection are more likely to earn and retain trust from their clientele.
Ensuring compliance with data privacy regulations
Compliance with data privacy regulations is a crucial aspect for businesses operating within Australia. Entities must follow strict guidelines mentioned in the Australian Privacy Act and GDPR for European customers. This involves implementing adequate measures to protect personal information from misuse, interference, loss, unauthorized access, modification, or disclosure. Ensuring compliance not only avoids substantial penalties but also fortifies the customer’s confidence in how their data is managed—integral for maintaining long-term business relationships.
Incident Response and Recovery
Developing an effective incident response plan
In the realm of cybersecurity, a well-developed incident response (IR) plan is a critical asset for Australian businesses. Such a plan outlines procedures and actions to be undertaken following a data breach or cyber-attack. Companies must create detailed IR plans that outline roles, responsibilities, and communication strategies to effectively handle potential threats. Expertise in swift identification, containment, eradication of the threat, and post-incident analysis is crucial. This systematic approach mitigates the impact on business operations and preserves stakeholder trust.
Best practices for swift recovery from cybersecurity incidents
To bounce back from cybersecurity setbacks, companies should embrace certain best practices that expedite recovery efforts. Regularly updating and testing IR plans ensures that businesses can respond with agility when required. Employing advanced monitoring systems aids in the early detection of irregularities, minimizing potential damages. Further investment in staff training programs for swift and appropriate responses enhances a company’s resilience against future incidents. Top-tier firms also foster relationships with external cybersecurity experts who provide additional support to recover from these security breaches smoothly
Security Architecture and Technologies
Implementing robust security architecture within businesses
To effectively safeguard their digital infrastructure, businesses must implement a robust security architecture. This involves structuring an organization’s network in a way that incorporates multiple layers of defense to detect, deter, and respond to threats. The pillars of strong security architecture often include firewalls, intrusion detection systems, malware protection, and data encryption. Beyond these technical aspects, companies should develop strategic policies that encompass access controls and regular audits. This cohesive blueprint is paramount for creating a secure environment that can withstand evolving cyber threats while supporting business continuity.
Leveraging the latest cybersecurity technologies for protection
In the dynamic landscape of cybersecurity, leveraging the latest technologies is fundamental for protection against sophisticated threats. Modern businesses should invest in cutting-edge solutions such as AI-driven threat intelligence, cloud-based security platforms, and automated response tools. These technologies offer proactive defense mechanisms by constantly analyzing patterns to predict and respond to potential breaches more efficiently. Moreover, implementing security orchestration and automated response (SOAR) integrates different tools and processes facilitating rapid incident response. Such investments not only shield organizations from imminent dangers but also bestow a competitive edge through enhanced cyber resilience.
Creating a culture of cybersecurity awareness within organizations
Instilling a culture of cybersecurity awareness is as crucial as the deployment of advanced technological defenses. Organizations should prioritize ongoing awareness campaigns that stress the importance of every individual’s role in safeguarding data and systems. Through interactive workshops, gamified learning platforms, and consistent communication regarding potential cyber risks, businesses can engrain a mindset that values vigilance and responsibility. This cultural pivot is not a one-time exercise but a sustained effort that evolves in tandem with the ever-changing digital threat environment.





