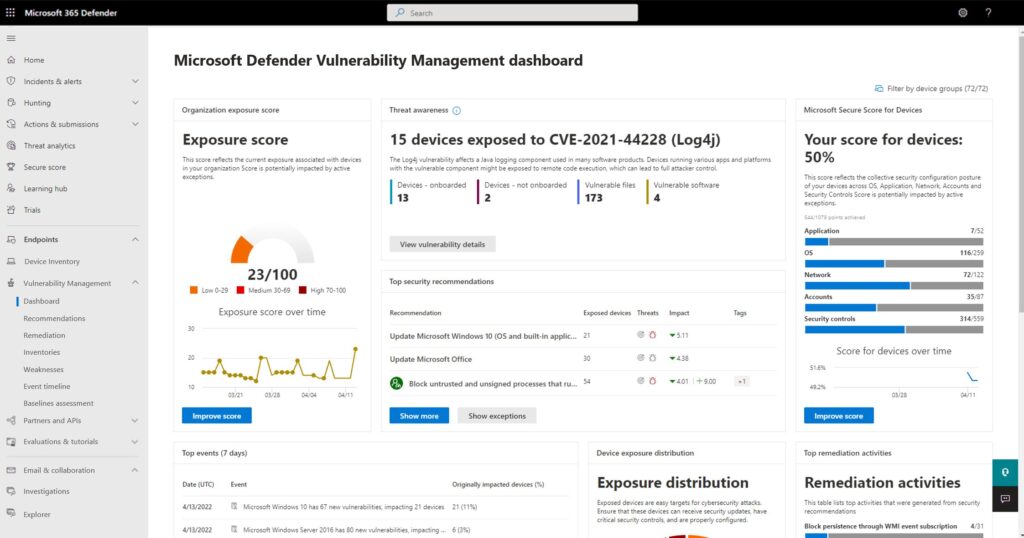
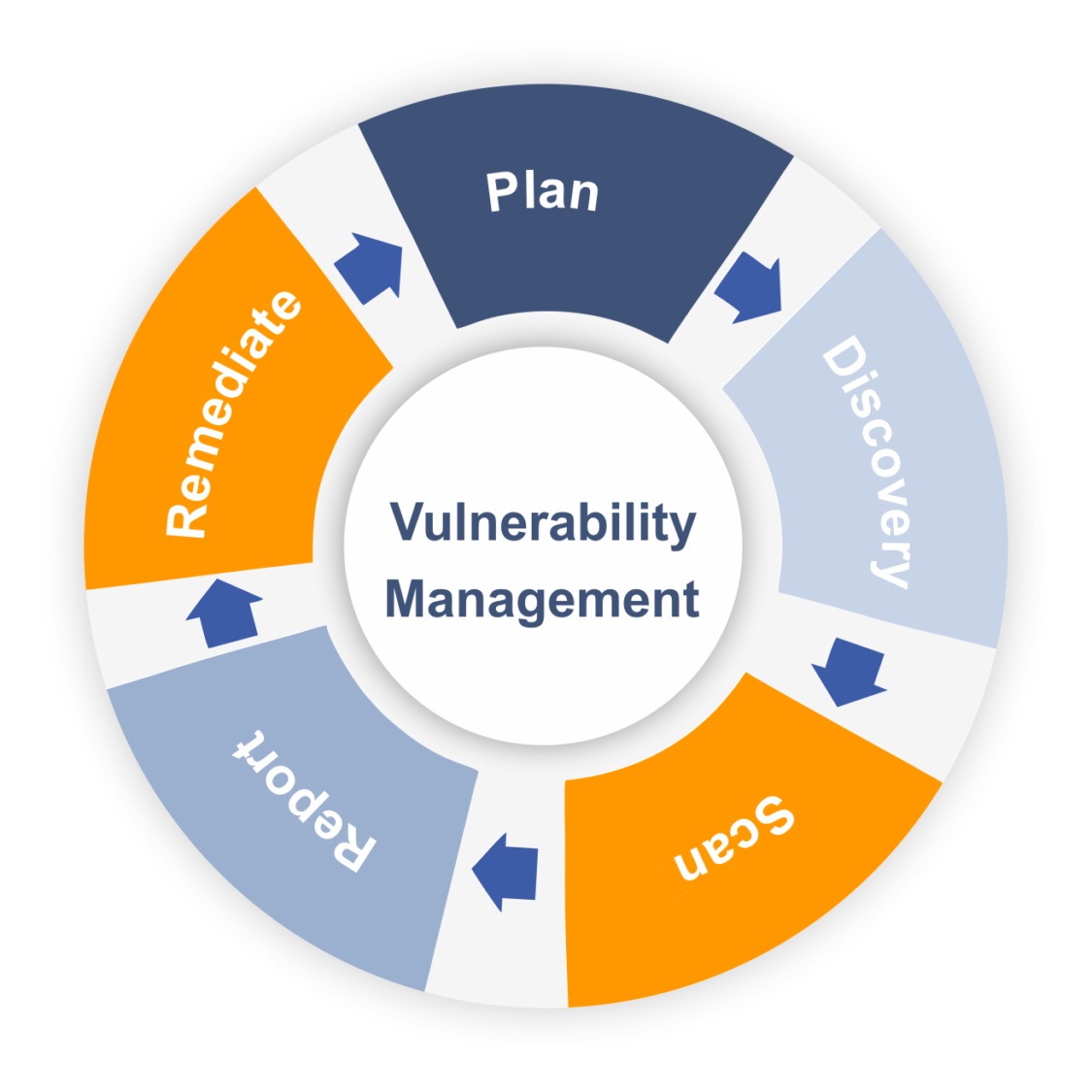
Vulnerability management starts with assessing the risk and identifying potential vulnerabilities that may exist in an IT infrastructure. These vulnerabilities may be identified through various means, such as penetration testing, network scanners, vulnerability scanners, and other security assessment tools.
Once the vulnerabilities have been identified, the next step is to prioritize them based on their potential impact, likelihood of being exploited, and the ease of remediation. This prioritization helps organizations to focus their resources on the most critical vulnerabilities and fix them first.
The process of addressing vulnerabilities involves applying patches, updates, or configurations that minimize or eliminate the risk associated with the vulnerability. This can be a challenging task due to the complexity of IT infrastructures, the number of systems that need to be patched, and the need for testing to ensure that patches do not break other systems.
Effective vulnerability management requires continual monitoring and testing to identify new vulnerabilities, as well as ongoing efforts to maintain a secure system. It also involves the collaboration of various stakeholders, such as security personnel, IT staff, and management.
In summary, vulnerability management is a critical process that helps organizations to maintain a secure system and protect against security threats. It involves the identification, prioritization, and remediation of vulnerabilities, along with ongoing monitoring and testing to ensure the security of a system.