
Introduction to Vulnerabilities and Exploits
In the world of cybersecurity, vulnerabilities and exploits play a critical role in understanding and mitigating risks. By identifying vulnerabilities, which are weaknesses in systems or software, you can take proactive measures to prevent potential breaches. Exploits, on the other hand, are methods or techniques that attackers use to take advantage of these vulnerabilities.
The Importance of Measuring and Scoring Vulnerabilities and Exploits
To effectively manage and address vulnerabilities and exploits, it is crucial to have a systematic approach to measure and score them. Here’s why:
- Prioritize Remediation: Measuring the severity of vulnerabilities and exploits helps your organization prioritize which ones require immediate attention. To prioritize fixing issues, assign scores or ratings based on their potential impact and likelihood of exploitation.
- Allocate Resources Efficiently: Measuring vulnerabilities and exploits allows you to allocate your resources more efficiently. With limited resources, it’s essential to identify high-risk areas that require immediate action to prevent potential damage or data breaches.
- Assess your Security Posture: Measuring vulnerabilities and exploits provides valuable insights into the overall security posture of your systems or software. It helps identify recurring patterns or trends that need to be addressed to strengthen your defenses against future attacks.
- Facilitate Communication: Having a standardized measurement and scoring system for vulnerabilities and exploits enables effective communication between different stakeholders, such as IT teams, management, and third-party vendors. It ensures everyone understands the severity of issues and facilitates decision-making processes.
By implementing a robust vulnerability management program that incorporates measurement and scoring methodologies like the Common Vulnerability Scoring System (CVSS), organizations can better protect their assets and minimize potential risks.
In conclusion, measuring and scoring vulnerabilities and exploits is crucial to cybersecurity risk management. It enables organizations to prioritize remediation efforts, allocate resources efficiently, assess their security posture, and facilitate effective communication. By proactively addressing vulnerabilities and exploits, businesses can stay one step ahead of cyber threats and safeguard their critical assets.
Common Vulnerability Scoring System (CVSS)
Overview of CVSS
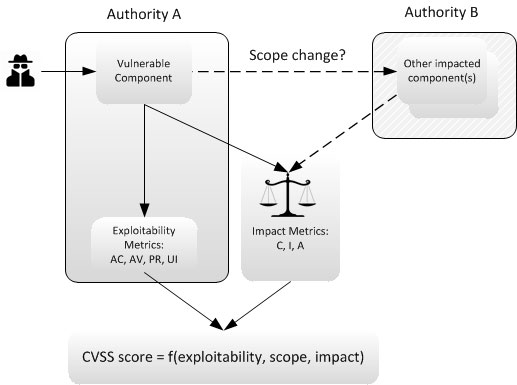
The Common Vulnerability Scoring System (CVSS) is a standardized framework developed to assess the severity of vulnerabilities and exploits. It provides a consistent method for organizations to prioritize and manage their response to security threats. The CVSS assigns a numeric score on a scale from 0 to 10, with 10 being the most severe.
Scoring Methodology
CVSS calculates scores based on factors like the impact of the vulnerability on confidentiality, integrity, and availability, as well as the complexity of the exploit and the required user interaction. These scores help organizations prioritize their efforts to mitigate vulnerabilities and allocate resources effectively.
To calculate the CVSS score, assessors evaluate the impact of each of the three main components: base, temporal, and environmental. The base score represents the inherent characteristics of the vulnerability, while the temporal score considers additional factors such as exploit code maturity and remediation availability. The environmental score takes into account unique contextual factors specific to an organization’s environment.
Practical Examples
Security professionals use CVSS scores to objectively evaluate vulnerabilities and guide decision-making processes. For example, if an organization discovers a vulnerability with a high CVSS score, they would prioritize patching it over lower-scoring vulnerabilities. This helps focus limited resources where they are most needed.
It’s worth noting that while CVSS provides a useful framework for vulnerability assessment and prioritization, it should be used in conjunction with other security measures and best practices. Organizations should consider their specific environment and risk tolerance when interpreting and applying CVSS scores.
CVSS is an essential tool for measuring and scoring vulnerabilities and exploits. Its standardized approach allows organizations to prioritize their response efforts effectively and mitigate security risks more efficiently.
Common Weakness Enumeration (CWE)
Introduction to CWE
The Common Weakness Enumeration (CWE) is a community-developed list of common software weaknesses. It provides a comprehensive and standardized way to identify and categorize software vulnerabilities. CWE helps organizations assess and prioritize vulnerabilities, making it an essential tool for vulnerability management.
Categorizing Vulnerabilities
CWE categorizes vulnerabilities into classes, each representing a unique weakness or flaw that can be exploited. These classes are organized into different views, such as the Common Vulnerability Scoring System (CVSS) view, which focuses on vulnerability scoring. CWE also provides a hierarchical structure that allows for more detailed classification and understanding of specific weaknesses.
By categorizing vulnerabilities, organizations can better understand the common patterns and themes associated with coding mistakes and design flaws. This knowledge enables developers and security professionals to identify root causes and implement appropriate remediation measures.
Mapping CWE to other standards
CWE is designed to be compatible with other vulnerability standards, such as the MITRE ATT&CK framework and the Open Web Application Security Project (OWASP) Top Ten Project. This compatibility allows for cross-referencing between different standards, providing a holistic view of vulnerabilities across various domains.
Mapping CWE to other standards enhances the effectiveness of vulnerability management efforts by bridging the gap between different methodologies and frameworks. It enables organizations to align their vulnerability assessment, mitigation, and reporting processes with industry best practices.
In conclusion, understanding and utilizing the Common Weakness Enumeration (CWE) is crucial for effective vulnerability management. By categorizing vulnerabilities and mapping them to other standards, organizations can prioritize their efforts, improve security posture, and mitigate the risk of exploitable weaknesses in their software systems.
National Vulnerability Database (NVD)
NVD Overview
The National Vulnerability Database (NVD) is a comprehensive resource that provides information on vulnerabilities and exploits. It is managed by the National Institute of Standards and Technology (NIST) and serves as a valuable tool for cybersecurity professionals and organizations.
The NVD collects vulnerability information from various sources, including public databases, security researchers, and software vendors. It then assigns each vulnerability a Common Vulnerabilities and Exposures (CVE) identifier – a unique reference number that facilitates the tracking and management of vulnerabilities.
This database not only provides detailed descriptions of vulnerabilities but also includes severity scores and impact metrics. These metrics are assigned using the Common Vulnerability Scoring System (CVSS), which helps users gauge the severity and potential impact of each vulnerability.
Accessing and Utilizing NVD Data
Security professionals can access the NVD through its online interface or download the database in various formats, such as XML or JSON. The NVD’s website also offers an API that allows users to programmatically access vulnerability data.
Once obtained, this data can be utilized in several ways to enhance an organization’s cybersecurity posture. Here are a few key applications:
- Prioritizing Patching: By analyzing NVD data and focusing on high-severity vulnerabilities affecting your systems, you can prioritize patching efforts to mitigate the most critical risks effectively.
- Vulnerability Management: The NVD enables security teams to identify vulnerabilities applicable to their infrastructure or software stack. This information can be used to implement effective vulnerability management processes, including vulnerability scanning, remediation, and monitoring.
- Threat Intelligence: By monitoring the NVD regularly, organizations can stay informed about emerging vulnerabilities and potential exploits. This knowledge empowers them to take proactive measures and develop appropriate defense strategies against evolving threats.
In conclusion, the National Vulnerability Database is a vital resource for cybersecurity professionals, providing comprehensive vulnerability information, severity scores, and impact metrics. Leveraging NVD data allows organizations to prioritize patching, enhance vulnerability management processes, and stay ahead of emerging threats.
Exploit-Proof Security Scoring (ePSS)
Understanding ePSS
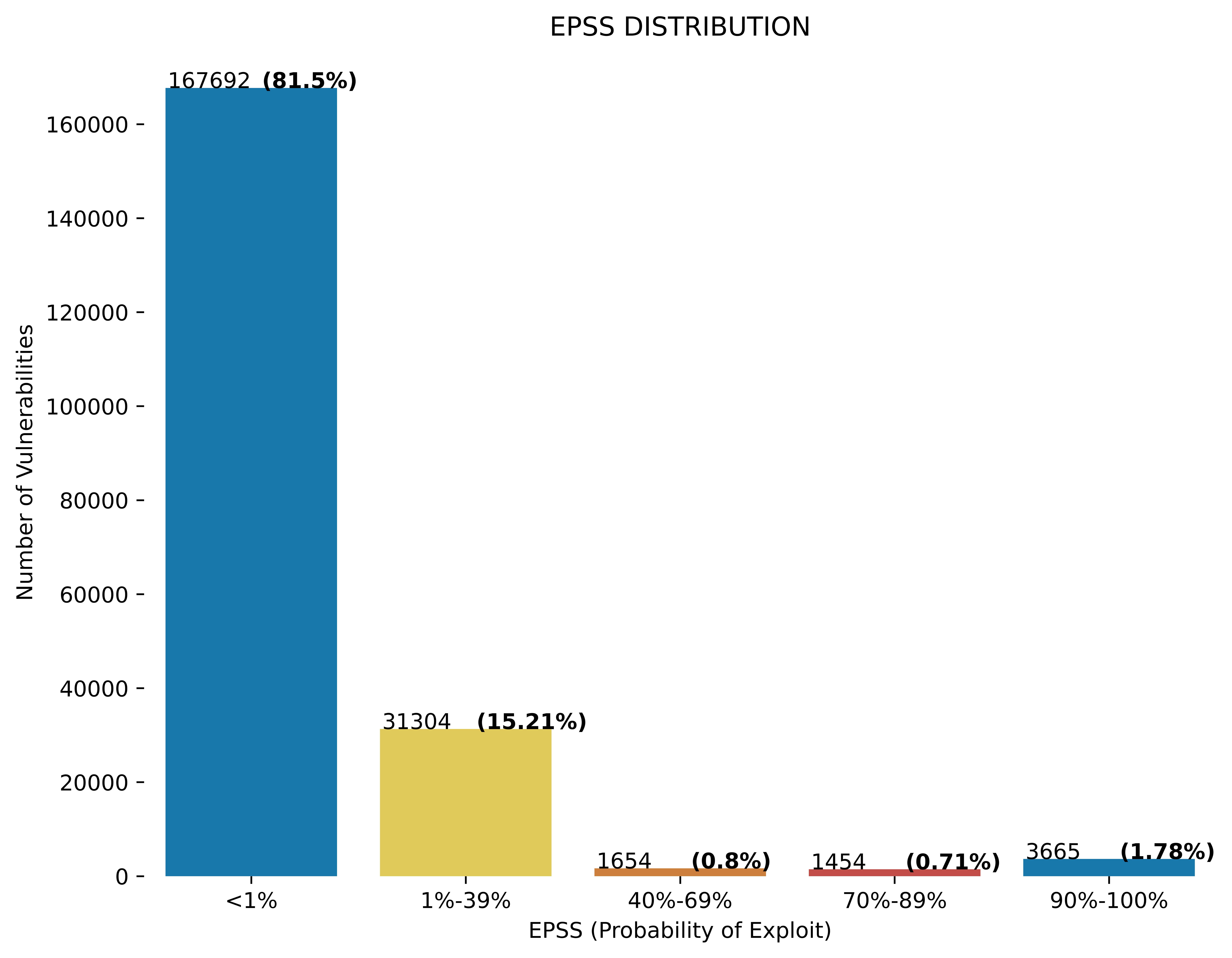
Exploit-Proof Security Scoring (ePSS) is a comprehensive system used to measure and score vulnerabilities and exploits. It provides organizations with valuable insights into the security of their systems and helps them prioritize their efforts to enhance security.
ePSS takes into account various factors such as the severity and potential impact of vulnerabilities, the ease of exploitability, and the availability of patches or mitigations. It analyzes and assigns scores to different vulnerabilities and exploits, highlighting the most critical areas that need immediate attention.
Scoring Methodology
The scoring methodology used by ePSS follows a standardized approach that allows for consistency in evaluating vulnerabilities across different systems and platforms. The scoring is typically based on the Common Vulnerability Scoring System (CVSS), which is a widely accepted industry standard.
The CVSS assigns scores to vulnerabilities based on three main metrics: the base score, the temporal score, and the environmental score. The base score reflects the intrinsic characteristics of the vulnerability, such as its impact and exploitability. The temporal score takes into account factors like the availability of patches or mitigations. The environmental score considers the specific conditions of the target system.
These scores are then combined to give an overall rating, ranging from low to critical, indicating the severity of the vulnerability or exploit. This allows organizations to prioritize their remediation efforts by focusing on higher-rated vulnerabilities that pose a greater risk.
By using ePSS, organizations can make informed decisions regarding their security posture, allocate resources effectively to address vulnerabilities, and proactively protect their systems from potential attacks.
In conclusion, ePSS provides organizations with a comprehensive framework for measuring and scoring vulnerabilities and exploits. It enables them to prioritize their security efforts based on the severity of the risks they face. By leveraging ePSS, organizations can enhance their security posture and reduce the potential impact of cyber threats.
Open Vulnerability and Assessment Language (OVAL)
OVAL Overview
The Open Vulnerability and Assessment Language (OVAL) is a standardized framework for assessing and reporting security vulnerabilities and configuration issues in computer systems. Developed by the MITRE Corporation, OVAL provides a common language and format for organizations to measure, assess, and report on the security posture of their systems.
OVAL adopts an open and extensible approach, allowing the community to contribute tests for various platforms, applications, and systems. This collaborative effort ensures that OVAL stays up-to-date with the latest security vulnerabilities and configuration issues.
XML Schema and Definitions
OVAL uses XML to define the structure of vulnerability definitions and assessment results. The XML schema provides a standardized way to define attributes such as system characteristics, tests, states, objects, and variables. This structured approach allows for consistency in representing vulnerability data across different platforms and environments.
The definitions in OVAL include detailed information about different vulnerabilities, including their severity, impact, affected platforms, and associated reference materials. By leveraging this standardized format, organizations can easily share vulnerability information with vendors, researchers, and other stakeholders.
Implementing OVAL for Scoring
OVAL can be used as a basis for developing vulnerability scoring systems. By mapping vulnerability definitions to scores, organizations can prioritize mitigation efforts based on the severity of the vulnerabilities detected. This scoring approach enables businesses to allocate resources efficiently and focus on addressing the most critical security issues first.
Additionally, OVAL provides guidance on how to assess vulnerabilities through testing methodologies and recommendations for remediation. This helps organizations evaluate their security posture accurately and develop effective strategies to mitigate risks effectively.
In conclusion, OVAL is a powerful framework that enables organizations to measure, assess, and score vulnerabilities accurately. By adopting OVAL standards, businesses can improve their security posture by identifying and addressing vulnerabilities promptly and efficiently.
Cybersecurity and Infrastructure Security Agency (CISA)
CISA’s Role in Vulnerability Scoring
The Cybersecurity and Infrastructure Security Agency (CISA) plays a crucial role in assisting organizations with measuring and scoring vulnerabilities and exploits. CISA protects the nation’s critical infrastructure from cyber threats, making their expertise invaluable in this field.
When it comes to vulnerability scoring, CISA provides comprehensive guidance and resources to help organizations accurately assess and quantify the risks they face. They offer a variety of tools, such as the Common Vulnerability Scoring System (CVSS), which provides a consistent and standardized approach to scoring vulnerabilities. By utilizing these resources, organizations can prioritize their remediation efforts based on the severity of the vulnerabilities present.
Utilizing CISA Guidance for Scoring
To effectively measure and score vulnerabilities and exploits, organizations can follow CISA’s guidance:
- Identify Vulnerabilities: Begin by identifying potential vulnerabilities within your systems or infrastructure. This can be done through regular vulnerability scanning or conducting penetration testing.
- Assess Severity: Utilize CISA’s guidance, such as CVSS, to assess the severity of each identified vulnerability. Consider factors like exploitability, impact on confidentiality, integrity, and availability.
- Quantify Risks: Assign a numerical score to each vulnerability based on its severity. This allows for easier prioritization of remediation efforts.
- Prioritize Remediation: Focus on addressing vulnerabilities with higher scores first, as they pose greater risks to your organization.
By following CISA’s guidance and leveraging their expertise, organizations can effectively measure and score vulnerabilities and exploits. This enables them to make informed decisions regarding risk management and prioritize remediation efforts to protect their systems and infrastructure from potential threats.

Importance of Continuous Monitoring and Updates
In today’s digital age, the threat of vulnerabilities and exploits is ever-present. To protect your business and its valuable assets, it is crucial to have a comprehensive understanding of the vulnerabilities that exist within your systems. Get this guide to easily measure and score vulnerabilities and exploits and stay ahead of threats.
Strategies for Continuous Vulnerability Monitoring
Continuous vulnerability monitoring is essential for identifying and mitigating potential risks before they can be exploited by malicious actors. Here are a few key strategies to implement:
- Automated Scanning: Utilize vulnerability scanning tools that automate the process of identifying vulnerabilities across your network and systems. Regular scans ensure that any new vulnerabilities are promptly discovered.
- Patch Management: Keep your systems current by promptly installing patches and updates released by software vendors. These patches often address known vulnerabilities and help mitigate potential risks.
- Network Segmentation: Segment your network into different segments to limit the impact of a potential breach. By restricting access between segments, you can contain any potential exploit.
Keeping Scoring Systems Up to Date
An essential component of vulnerability management is the scoring system used to evaluate the severity of vulnerabilities. To ensure accurate risk assessment, it is vital to keep these scoring systems up to date. Regular updates from organizations such as the Common Vulnerability Scoring System (CVSS) allow you to assign accurate scores to vulnerabilities based on their impact and exploitability.
Regularly updating your scoring system also enables more effective prioritization of remediation efforts. By understanding the potential impact of each vulnerability, you can allocate resources efficiently and address high-risk vulnerabilities first.
In conclusion, continuous vulnerability monitoring, along with regular updates to your scoring systems, is essential for maintaining a secure digital environment. By implementing these strategies and staying vigilant, you can proactively protect your business from potential threats and ensure the safety of your valuable assets.

Conclusion
In conclusion, measuring and scoring vulnerabilities and exploits is crucial to maintaining security in today’s digital landscape. By analyzing and quantifying potential weaknesses, organizations can prioritize their remediation efforts effectively and allocate resources where they are most needed. However, it’s important to recognize that this process has its limitations and should be used in conjunction with other security measures.
Benefits and Limitations of Measuring and Scoring Vulnerabilities and Exploits
When it comes to measuring and scoring vulnerabilities and exploits, there are several benefits:
- Improved Risk Management: By understanding the severity and impact of vulnerabilities, organizations can make informed decisions about risk mitigation strategies and prioritize their efforts accordingly.
- Prioritization of Patching: Scoring vulnerabilities allows organizations to identify high-risk issues that require immediate attention, ensuring that critical patches are deployed promptly.
- Efficient Resource Allocation: By focusing on the most critical vulnerabilities, organizations can allocate their limited resources effectively, addressing the areas of greatest concern first.
However, it’s important to note the limitations of measuring and scoring vulnerabilities and exploits:
- Complexity: The process of measuring vulnerabilities can be complex, requiring a deep understanding of various factors such as the affected systems, the exploitability of the vulnerability, and its potential impact.
- Incomplete Assessment: Measuring vulnerabilities is often based on available information at a specific time. The assessment may become outdated as new vulnerabilities emerge or existing ones evolve.
- False Sense of Security: Relying solely on vulnerability scores may give organizations a false sense of security. It’s important to consider additional factors such as threat intelligence and attack vectors to get a more comprehensive understanding of the organization’s security posture.
Key Takeaways
Measuring and scoring vulnerabilities and exploits is a valuable tool for organizations to assess and prioritize their security efforts. It helps in identifying high-risk vulnerabilities, prioritizing patching, and allocating resources efficiently. However, it should be used with other security measures and considerations to ensure a comprehensive approach to cybersecurity. Organizations should stay updated on emerging vulnerabilities and continually reassess their security posture to avoid potential threats.




