
Jaguar Land Rover Cybersecurity Breach August 2025
In August 2025, Jaguar Land Rover (JLR) experienced a significant cyberattack that stopped global manufacturing for over six...

Microsoft Purview: The Must-Have Tool for Data Management
Introduction Overview of Microsoft Purview In today’s complex digital landscape, businesses continually grapple with vast amounts of data....

Google Breach From Voice Phishing to Extortion
Overview of Google Breach Incident Summary of the Incident In June, Google discovered a breach in its Salesforce...

Qantas Cybersecurity Fallout: Understanding the Data Breach
Overview of Qantas Data Breach Incident Brief Background of Qantas Qantas, Australia’s flag carrier, is renowned for its...

IBM X-Force Threat Intelligence Index 2025
Overview of IBM X-Force 2025 Threat Intelligence Index Introduction to IBM X-Force 2025 Threat Intelligence Index The IBM...

Mandiant's M-Trends 2025 Report
Overview of Mandiant’s M-Trends 2025 Report Introduction to Mandiant Mandiant, a leader in cybersecurity, has excelled in incident...

Cybersecurity Adoption in the Workplace
Introduction Overview of Literature Review on Cybersecurity Adoption in the Workplace In today’s digitally driven world, the significance...
Identity and Access Management: The Key to Protecting Your Data and Privacy
Introduction Importance of Identity and Access Management In today’s digital landscape, the significance of Identity and Access Management...
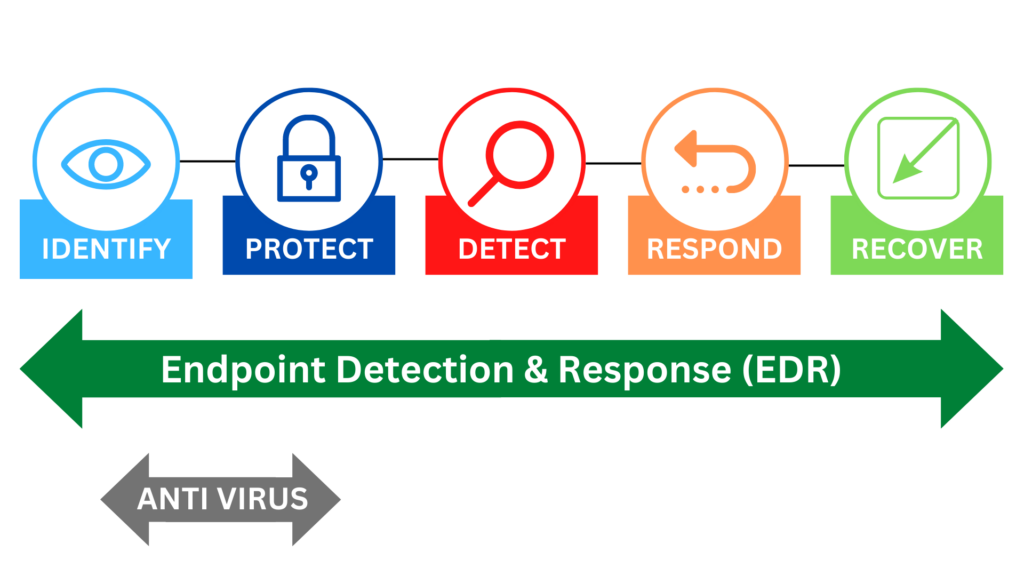
EDR Landscape: A Deep Dive into Market Trends, Leading Vendors, and Cutting-Edge Technology
Overview of EDR Landscape In today’s digital world, where cyber threats seem to evolve faster than our ability...

Medibank Breach of 2022: A Detailed Analysis
Introduction Overview of the Medibank Breach In late 2022, the healthcare sector faced a significant challenge as Medibank,...

Penetration Testing Execution Standard (PTES): A Comprehensive Guide
Introduction to Penetration Testing Execution Standard (PTES) As organizations increasingly rely on technology, the need for effective cybersecurity...

The Crowdstrike Service Disruption in July 2024
Introduction Overview of the Crowdstrike Service Disruption in July 2024 In July 2024, Crowdstrike, a leading cybersecurity firm,...

The Bangladesh Bank Cybersecurity Crisis 2016: Lessons Learned and Future Implications
Introduction Background of The Bangladesh Bank Cybersecurity Crisis The Bangladesh Bank cybersecurity crisis, which unfolded in early 2016,...
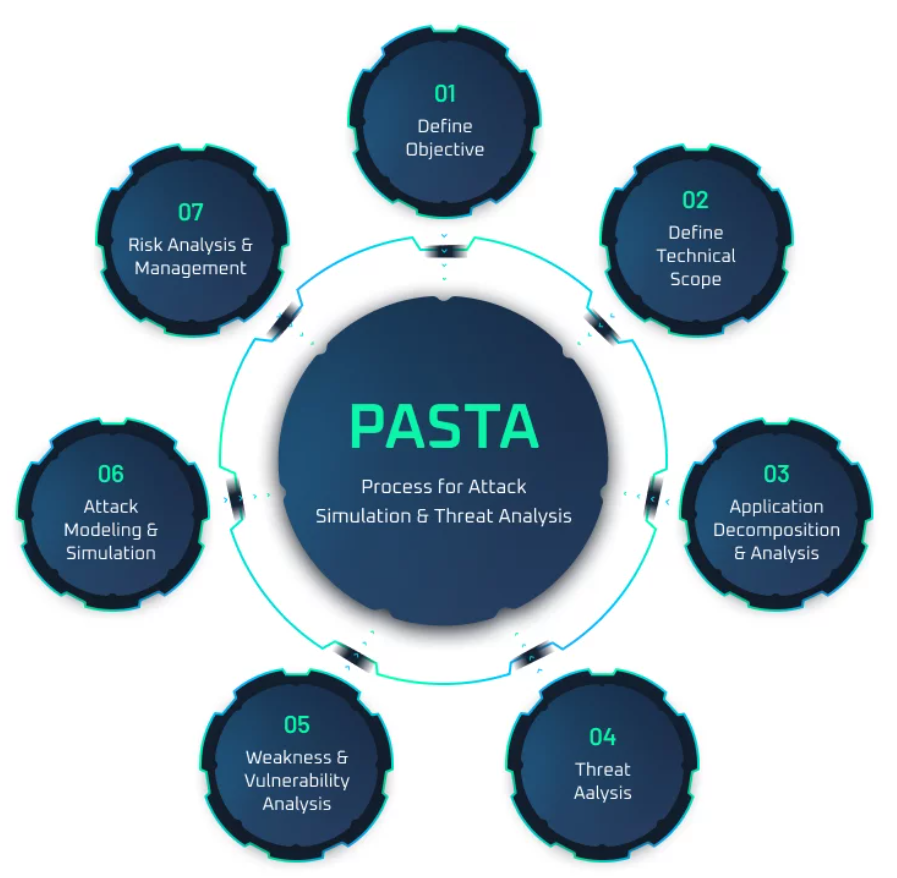
PASTA Threat Model Framework: A Comprehensive Guide
Introduction to PASTA Threat Model Framework Source: threat-modeling.com Overview of PASTA Threat Model Framework The PASTA Threat Model...

Password Attacks
Definition of password attacks A password attack is an unauthorised attempt to access a user’s account or system...

Cybersecurity Hacks: The Top 10 That Shook the World
Introduction In today’s digital age, the importance of cybersecurity cannot be overstated. A single cyber attack can have...
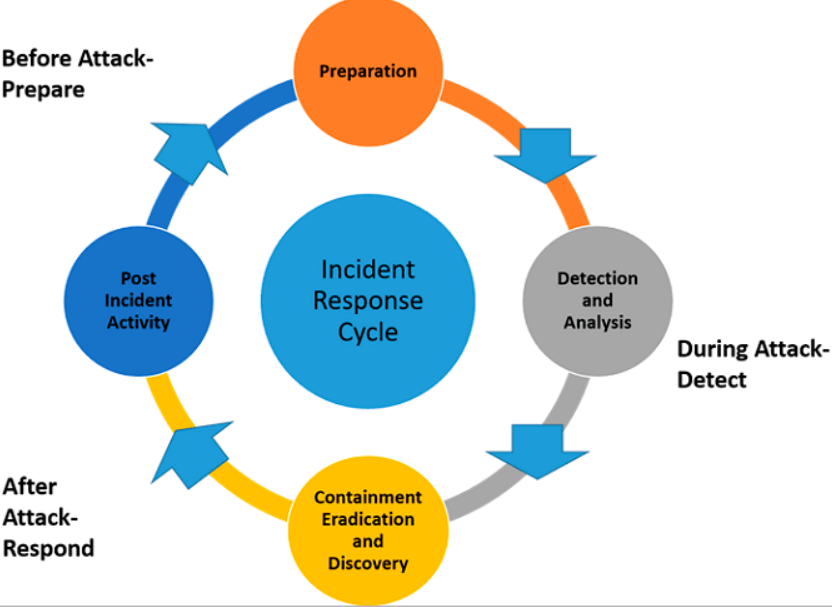
The NIST Incident Response Lifecycle: From Detection to Recovery
Introduction The NIST Incident Response Lifecycle is a comprehensive framework organizations can use to effectively manage and respond...

Building a Culture of Cybersecurity: Strategies for Employee Adoption
Importance of Building a Culture of Cybersecurity In today's digital age, building a culture of cybersecurity is of...

The Essentials 8 Cybersecurity Framework is Vital for Australian Businesses
Understanding the Essentials 8 Cybersecurity Framework Overview of the Essentials 8 Cybersecurity Framework In the digital age, cybersecurity...

Phishing Emails: How to Identify, Prevent, and Protect Yourself from Online Scams
We’ve all heard about phishing emails, but do we know what they are and how to protect ourselves?...

LastPass Hacked Many Times: A Deep Dive into the Vulnerabilities
Introduction Source: duet-cdn.vox-cdn.com LastPass is a popular password management tool known for its convenience and ability to securely...

The Colonial Pipeline Cyberattack
Overview of the Colonial Pipeline Cyber Attack The Colonial Pipeline cyberattack was a big event that affected the...

Okta Breach: A Deep Dive into the Attack
Introduction In the world of cybersecurity, even a breach at a highly reputable company like Okta can serve...

CNA Financial Hit by $40M Ransomware Attack: What We Need to Know
Introduction CNA Financial, a top US insurance company, was recently targeted by a major ransomware attack. The company...

CSPM vs DSPM
Introduction In today’s digital landscape, ensuring the security and protection of data has become a top priority for...
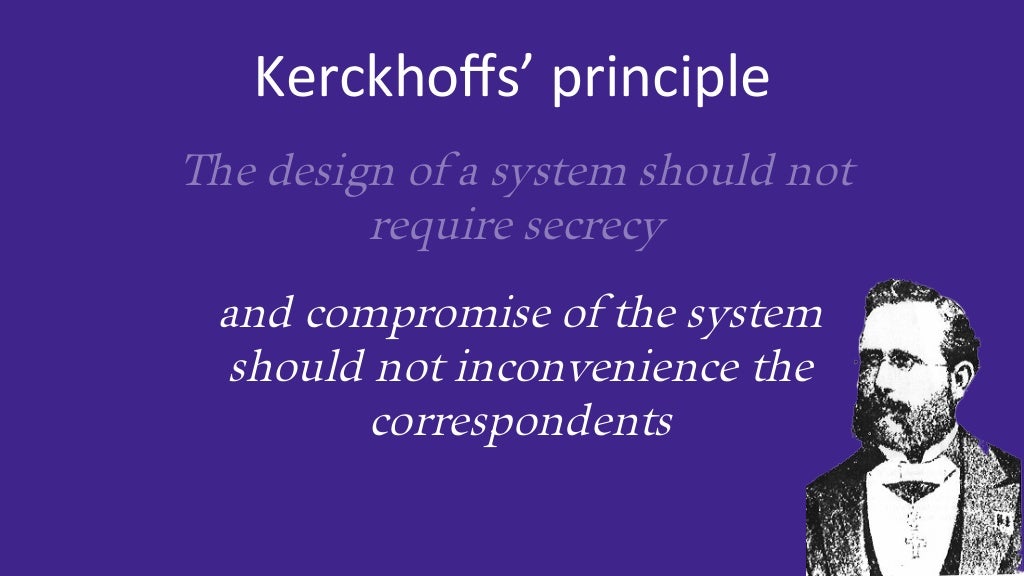
Kerckhoffs Principle vs Security Through Obscurity: Which is Better?
Introduction to Kerckhoffs' Principle Kerckhoffs' Principle, also called the "principle of the open door," says that the security...

Citrix Hack of 2023
Introduction In 2023, the technology industry was hit by a major cybersecurity incident when Citrix, a leading software...

The SolarWinds Cybersecurity Breach: What We Need to Know
Introduction In recent years, cybersecurity breaches have become a growing concern for businesses and individuals alike. The SolarWinds...

Wannacry: The Cyber Attack That Shook the World
Overview of the Wannacry Cyberattack The Wannacry cyberattack occurred in May 2017 and targeted computers running the Microsoft...

The Optus Cybersecurity Incident
Introduction In today’s digital landscape, cybersecurity is of utmost importance to protect sensitive information and maintain the trust...

Incident Response: Its Role in Cybersecurity
Introduction Incident response refers to the process of effectively and efficiently addressing and managing cybersecurity incidents within an...
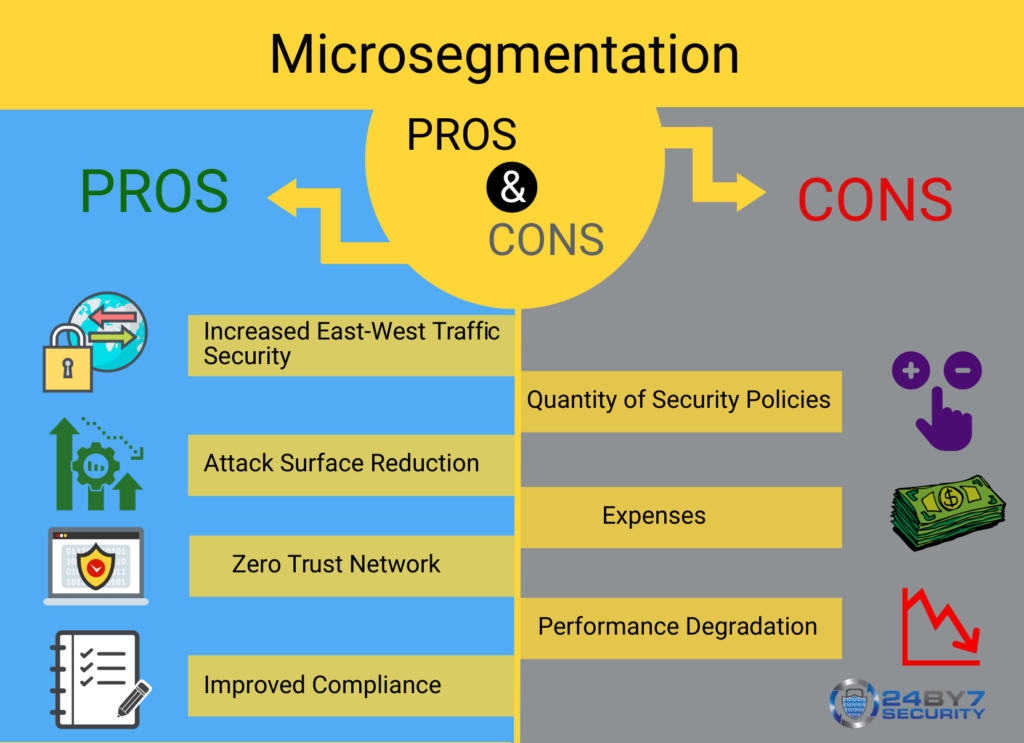
Network Microsegmentation: Protecting Your Business from Cyber Threats
Introduction Network microsegmentation is a crucial component of any comprehensive cybersecurity strategy. In today’s digital landscape, where cyber...

Cybersecurity Adoption in the Workplace
Importance of Cybersecurity for Organizations 1. Understanding the significance of cybersecurity Cybersecurity has become a critical aspect of...

The MGM Cyberattack: A Closer Look at What Happened
Introduction The MGM cyberattack is one of the most notable instances of a company falling victim to a...
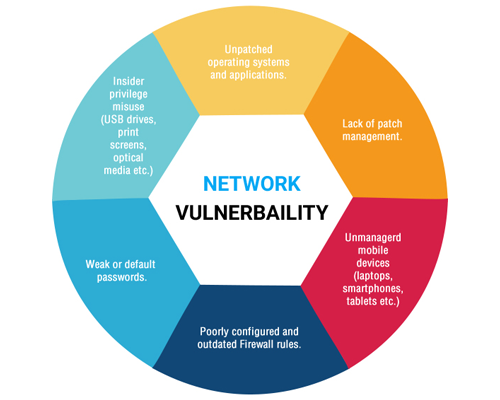
Effective IT Network Security Vulnerability Management Program
Introduction An effective IT network security vulnerability management program is essential for businesses to protect their sensitive data...

URL Filtering versus DNS Filtering
Introduction URL filtering and DNS filtering are two popular methods used to control and manage internet access within...

Vulnerability Measuring and Scoring
Introduction to Vulnerabilities and Exploits In the world of cybersecurity, vulnerabilities and exploits play a critical role in...

The Target Data Breach: How Hackers Stole Millions of Customer Records
Introduction The Target data breach in 2013 sent shockwaves through the retail industry and raised concerns about the...

The MOVEit Data Breach
Introduction The Move-It Data Breach sent shockwaves through the tech industry, highlighting the importance of strong cybersecurity measures....

ISO27001 Infosec Management System
ISO 27001 is a global standard that outlines the specifics of establishing, implementing, maintaining, and continuously improving an...

Python for Cybersecurity
Introduction to Python for Cybersecurity In the world of cybersecurity, staying one step ahead of hackers and protecting...

Infosec and Cybersecurity
Understanding Infosec and Cybersecurity Information security, often referred to as infosec, is the practice of protecting digital information...
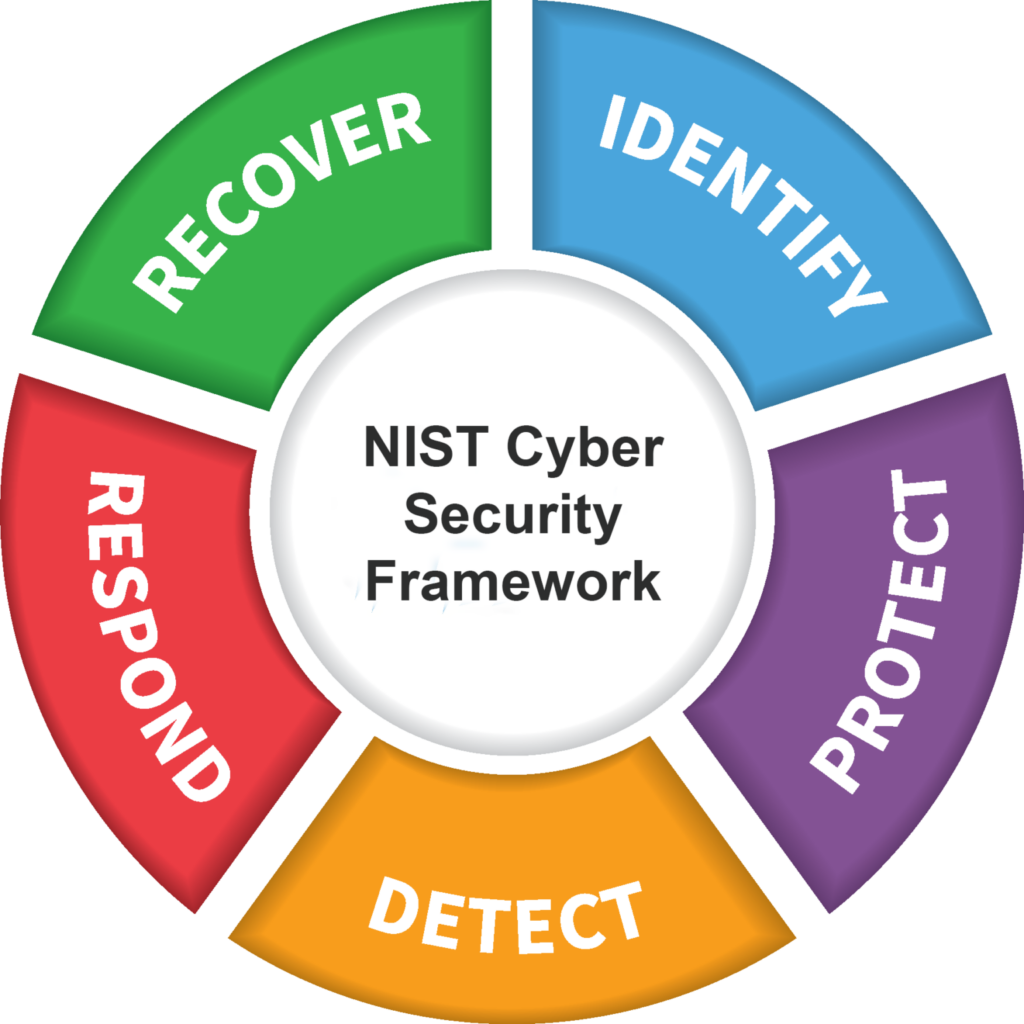
NIST Cybersecurity Framework
The NIST framework is a widely used cybersecurity framework designed by the National Institute of Standards and Technology...

CIS Controls V8
CIS Controls Version 8 is a cybersecurity framework that provides a recommended set of prioritized cyber defense best...

CISA: Keeping Businesses Safe from Cybercrime
Introduction Cybersecurity has become a critical concern for businesses of all sizes. With the increasing frequency and sophistication...

Wazuh SIEM: Why Wazuh Comes Out on Top
Introduction to Wazuh and SIEMs In today’s digital landscape, cybersecurity has become a top priority for organizations of...
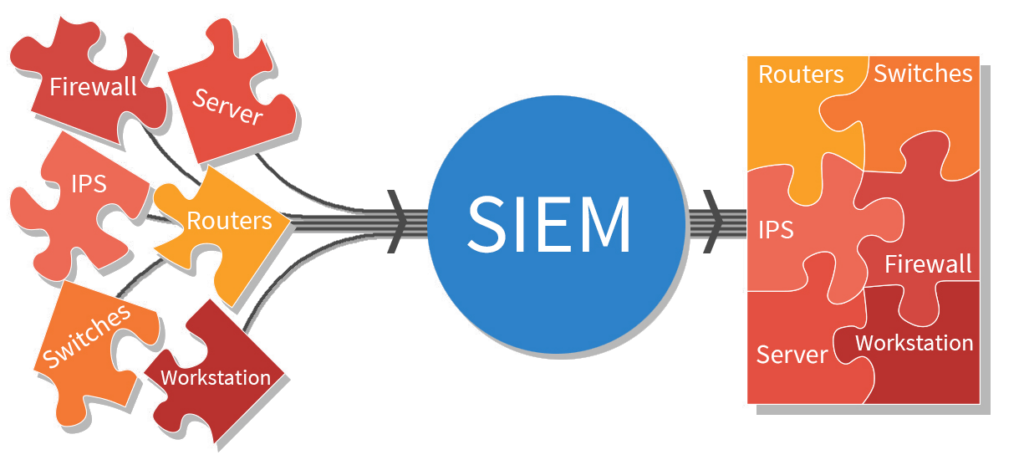
SIEM: An Introduction to Cybersecurity Monitoring, Detection and Response
I. Introduction to SIEM What is Security Information and Event Management (SIEM)? Security Information and Event Management (SIEM)...
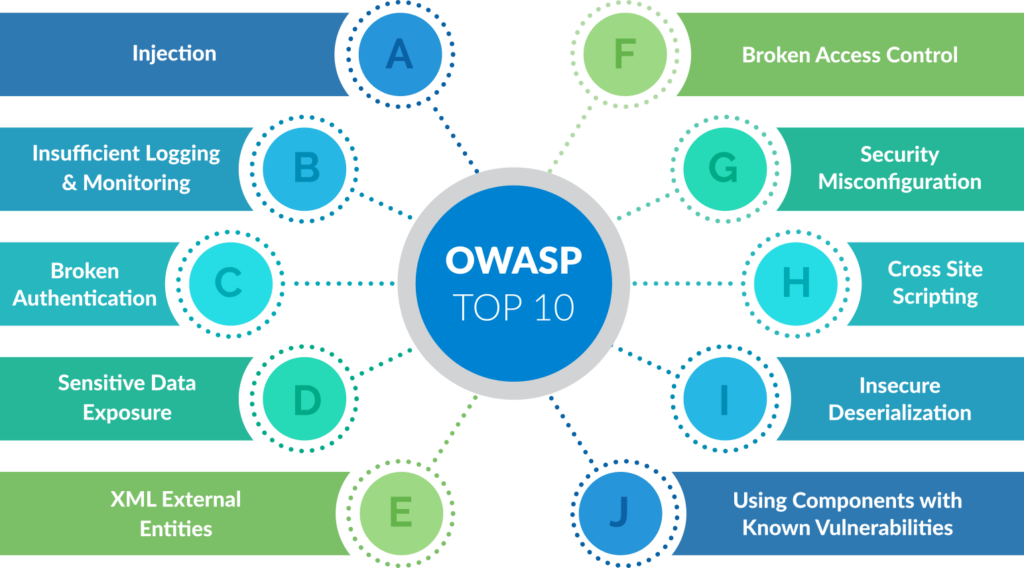
OWASP Top 10: A Guide Web Application Security Risks
I. Introduction to OWASP Top 10 Overview of OWASP (Open Web Application Security Project) OWASP (Open Web Application...

CVSS 4: What's New
I. Introduction to CVSS 4 The Common Vulnerability Scoring System (CVSS) is a crucial industry standard that provides...
MITRE ATT&CK Framework: Understanding the Anatomy of Cyber Threats
The threat landscape in the digital world is constantly evolving, with cyber-attack organisations becoming increasingly sophisticated and pervasive....
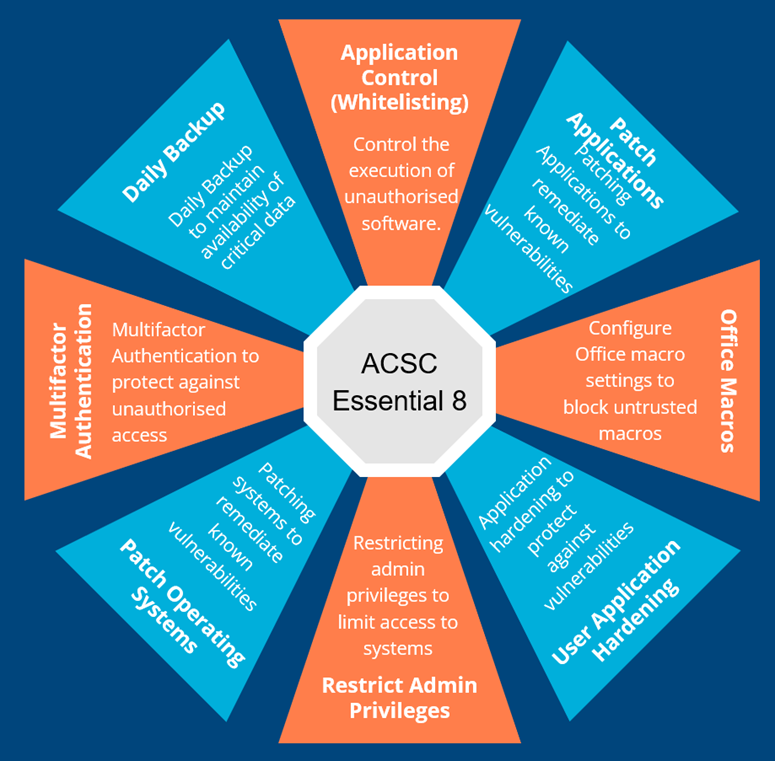
Essentials Eight: Introducing the ACSC’s Framework
The Australian Cybersecurity Centre (ACSC) has developed a comprehensive framework, the Essential Eight Maturity Model, designed to enhance...
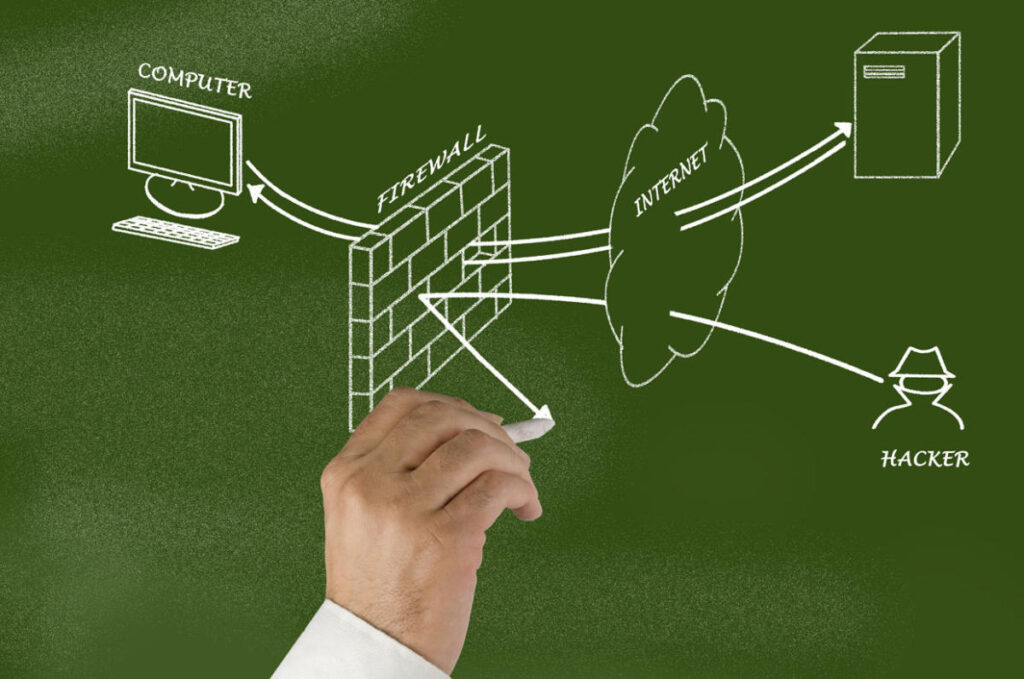
IT Network Security: Online Attacks and Defence Strategies
In today’s interconnected digital landscape, network attacks have become a pervasive threat that can have severe consequences for...
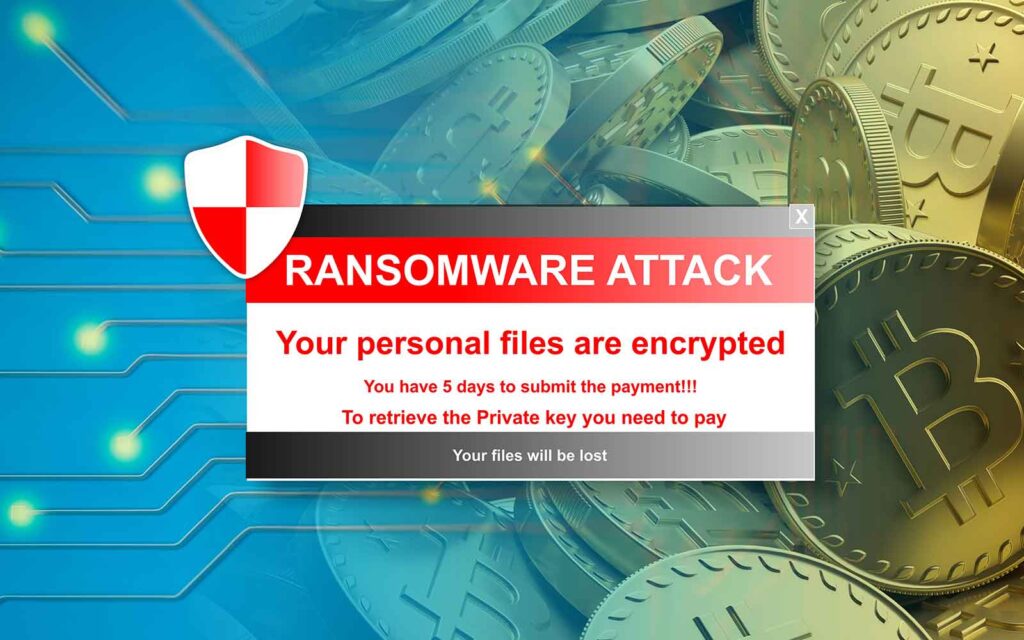
Ransomware
Ransomware attacks have become increasingly prevalent in today’s digital landscape, posing a significant threat to individuals and businesses....
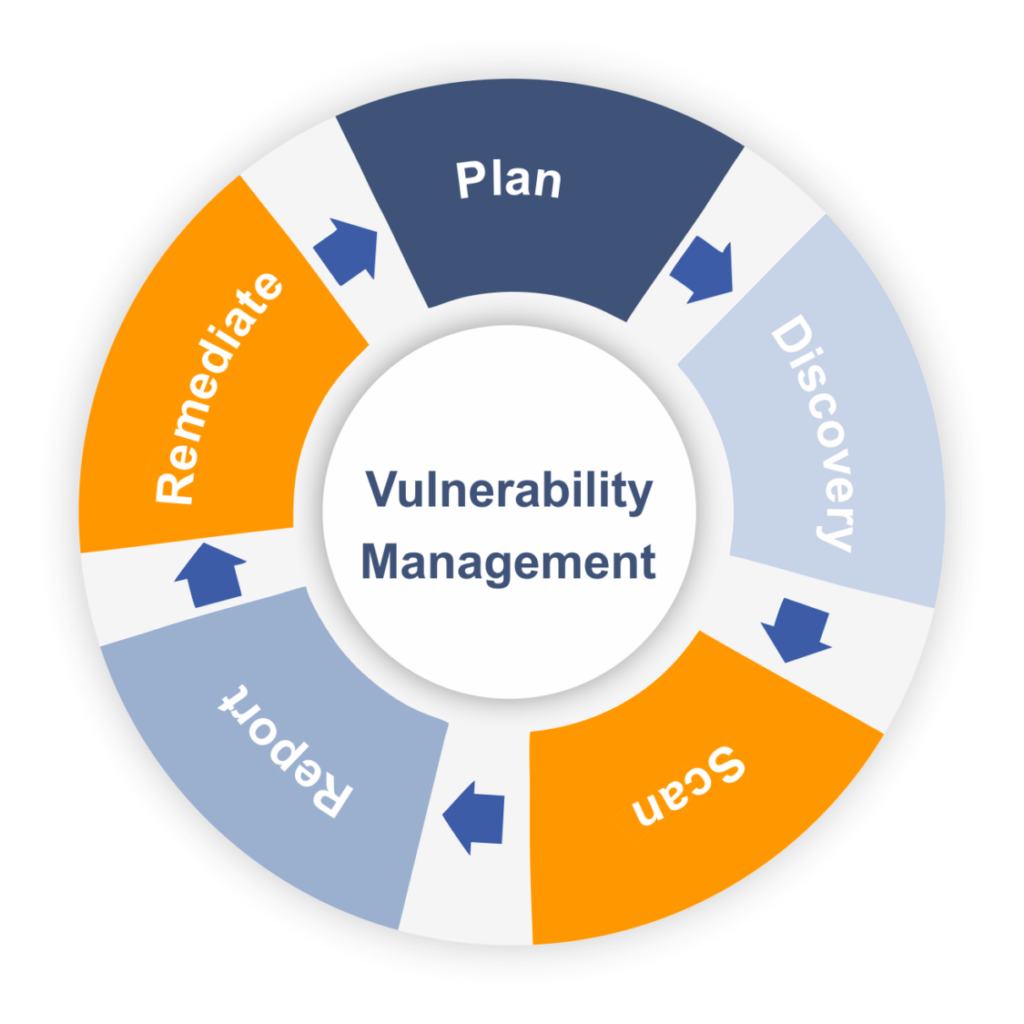
Vulnerability Management
Vulnerability Management is the process of identifying, evaluating, and addressing security vulnerabilities in a system. It encompasses...

Password Managers
A password manager is a tool that helps users securely store and manage their passwords. It is designed...
